Using the Vertex-Threat-Intel Power-Up Workflow
by thesilence | 2023-05-22
We recently highlighted the new Vertex-Threat-Intel Power-Up in a series of Threat Intel webinars. The Power-Up installs a Workflow that simplifies analysts' ability to work with operational and strategic data related to threat intelligence, such as the techniques used by a particular tool or threat cluster, or targeting associated with specific industries, countries, or organizations.
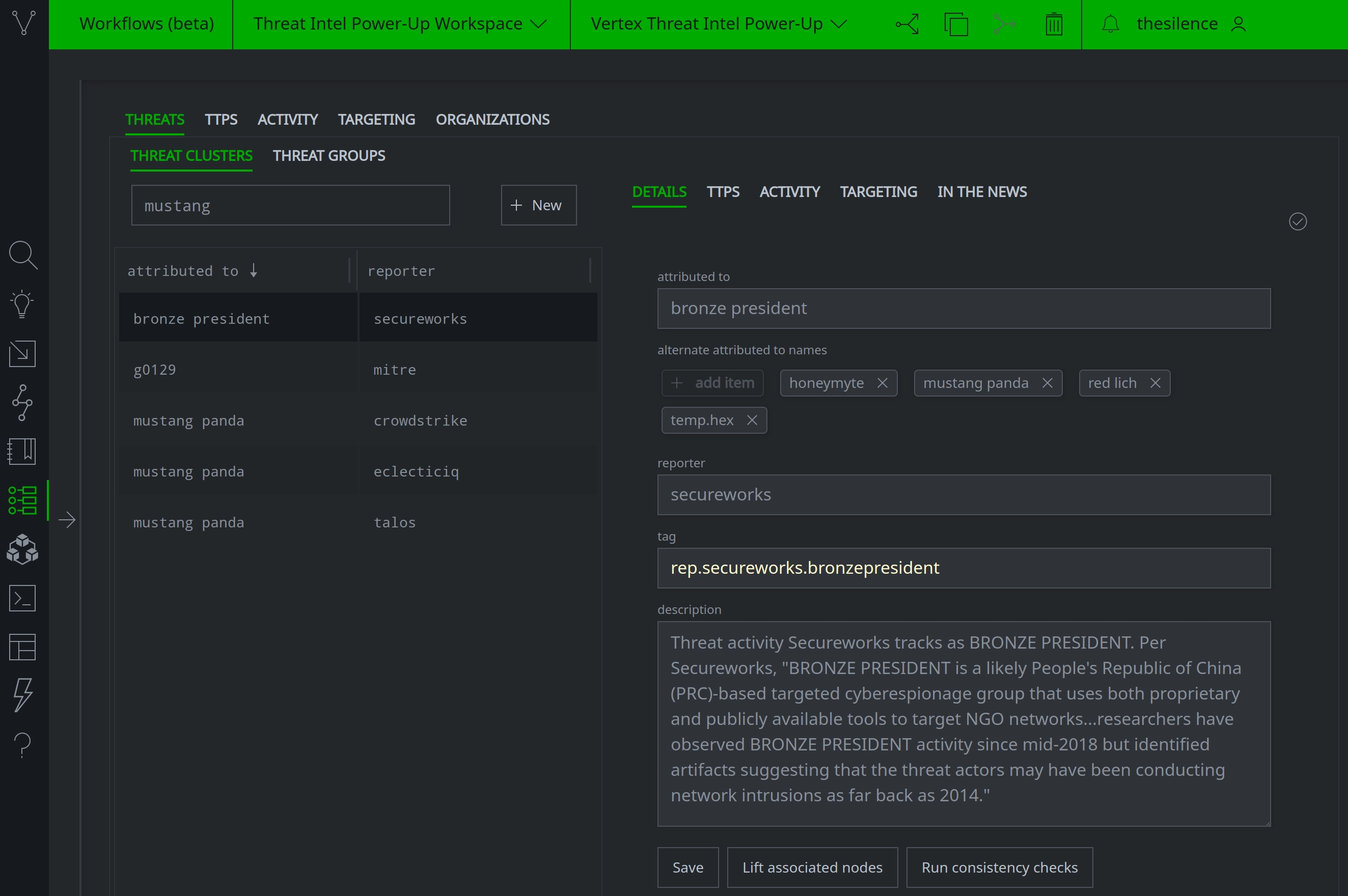
Part 1 of our series described the Workflow and covered working with threat clusters, threat groups, tools, and software. Part 2 expanded on Part 1 to include threat activity such as attacks, compromises, and campaigns. If you missed the original presentations, you can watch both Part 1 and Part 2 on our YouTube channel. If you want a more in-depth tour of the Workflow and some essential background on the threat intelligence portion of the Synapse data model, see the Vertex-Threat-Intel Power-Up User Guide.
The videos and background documents should allow you to jump-start your use of the Power-Up and Workflow! That said, we know that nothing beats sample data for diving in to see what things look like "in practice". For that reason, we're making the sample data used in our presentations available as a Synapse .nodes file that you can load into your instance of Synapse.
Tip
As always, we strongly recommend that you fork a view (or create a fully isolated view) to load the .nodes file so that the sample data remains separate from your production data!
All of our sample data was derived from public reporting. Threat intelligence objects such as threat clusters, tools, and compromises are linked to their sources (media:news nodes) so you can see how we created various nodes based on the original reports.
Examples of the various threat intel objects can be viewed in the Workflow.
Any object from the Workflow can be viewed in the Research Tool by right-clicking the object and selecting query > selected node.
You can (of course!) query objects directly in the Research Tool using Storm.
In the Research Tool, you may wish to customize the properties displayed for objects such as threat clusters (
risk:threat) or campaigns (ou:campaign).
A few notes on the data itself:
We have attempted to provide basic examples of the threat intelligence objects highlighted in the Workflow. That said, not every object is "feature complete" (i.e., we did not necessarily populate all possible properties or create all possible links in the sample data).
Many features of Synapse are intentionally customizable. The tag trees and taxonomies we defined, and the industries and goals we created, represent one example of how these elements can be used to meet specific analysis needs. As always...you do you!
You can download the sample .nodes file here.
To learn more about Synapse, join our Slack community, check out our videos on YouTube, and follow us on Twitter.
