Using Synapse to Investigate Suspected Credential Theft Activity
by savage | 2023-05-22
On March 14th and 18th 2023, Cloudflare and Inky reported on phishing activity that used Silicon Valley Bank as a lure and prompted email recipients to click on a link to access a document through Docusign. After ingesting their findings into Synapse, we leveraged several different Synapse Power-Ups to conduct our own research, verifying and expanding upon their findings. This blog will walk through how we used Synapse to identify additional infrastructure, actor techniques, and likely victims.
Public Reporting
In March 2023, Cloudflare released a blog describing an ongoing phishing campaign detected on March 14, 2023 when the company’s CEO received one of the phishing emails. The email looked as if it had been sent from DocuSign on behalf of Silicon Valley Bank’s compliance team, and purportedly sought to verify the recipient’s identity to fulfill the banking requirement known as Know Your Customer. The message prompted the recipient to click on a link, which Cloudflare reported would then redirect the user through the following URLs:
A link hosted on the domain
bs.serving-sys.com, which is run by Amazon Ad Server,A Google Firebase application hosted on
na2signing.web.app,A Wordpress site,
eaglelodgealaska.com, which Cloudflare noted may be either compromised or hosting a plugin redirecting usersAn operator-controlled site,
docusigning.kirklandellis.net
Several days later, Inky reported similar activity it described as an attempt to harvest Microsoft account credentials. Whereas Cloudflare had seen a redirect from a malicious Google Firebase application to eaglelodgealaska.com, Inky observed a redirect to dse.docuonline.eu and listed several additional domains and IP addresses as related infrastructure. Inky also noted March 16th, 2023 as the beginning of the campaign.
Research and Analysis with Synapse
We imported and modeled the Cloudflare and Inky blogs using Synapse’s Spotlight Tool, which created media:news nodes to represent the blogs themselves, then linked the referenced indicators using a -(refs)> light edge.
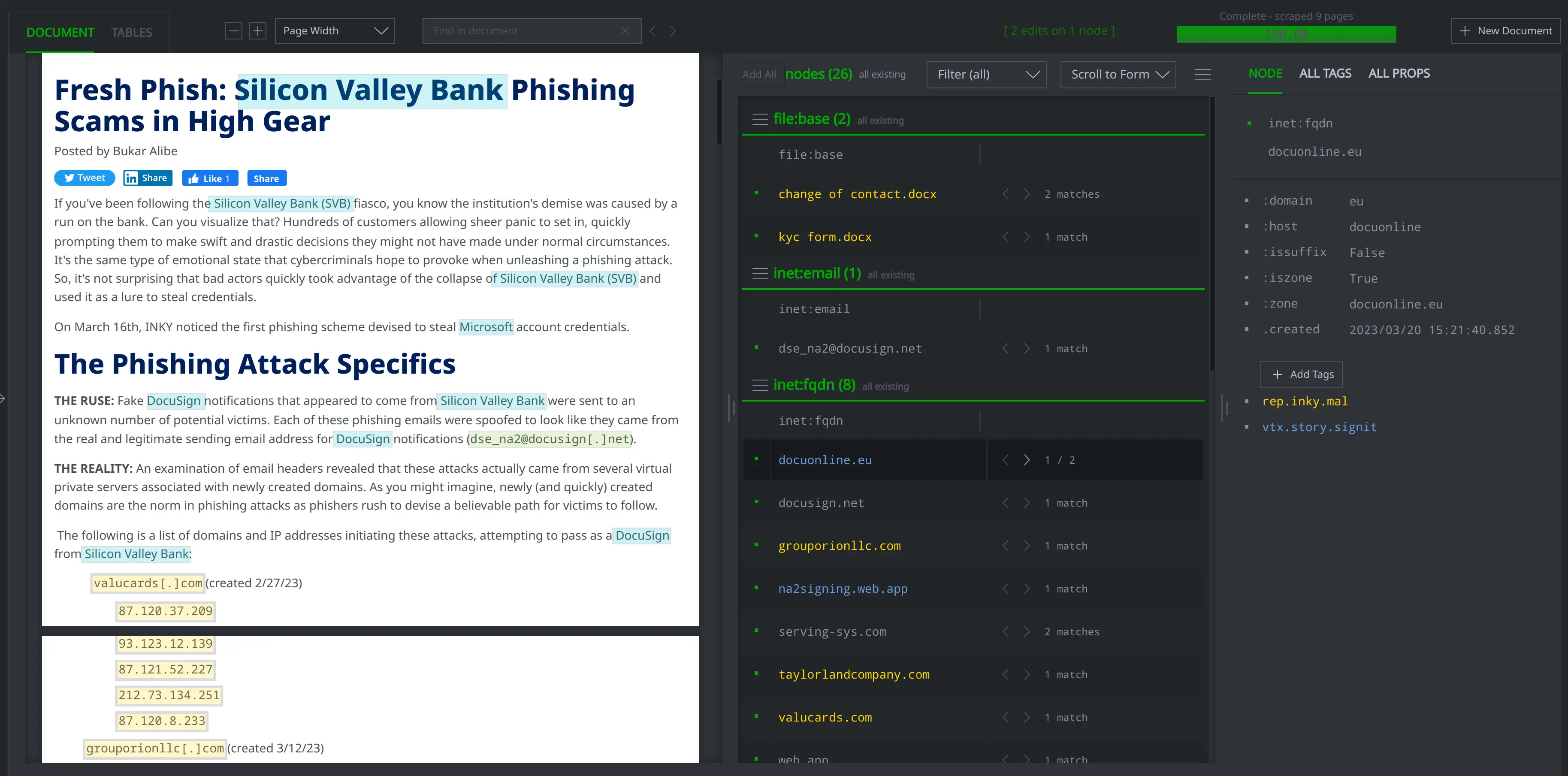
The indicators reported in the Cloudflare and Inky blogs are shown in yellow in Force Graph display mode below:
After modeling the blogs, we used several Synapse Power-Ups to enrich the referenced indicators with data from various third party sources, querying:
Synapse-Nettools for DNS A and WhoIs records
Synapse-URLScan to import and model additional URls and URL redirection activity
Synapse-Alienvault for pDNS records
Synapse-Whoxy for WhoIs and historic WhoIs records
Synapse-Zetalytics for pDNS data
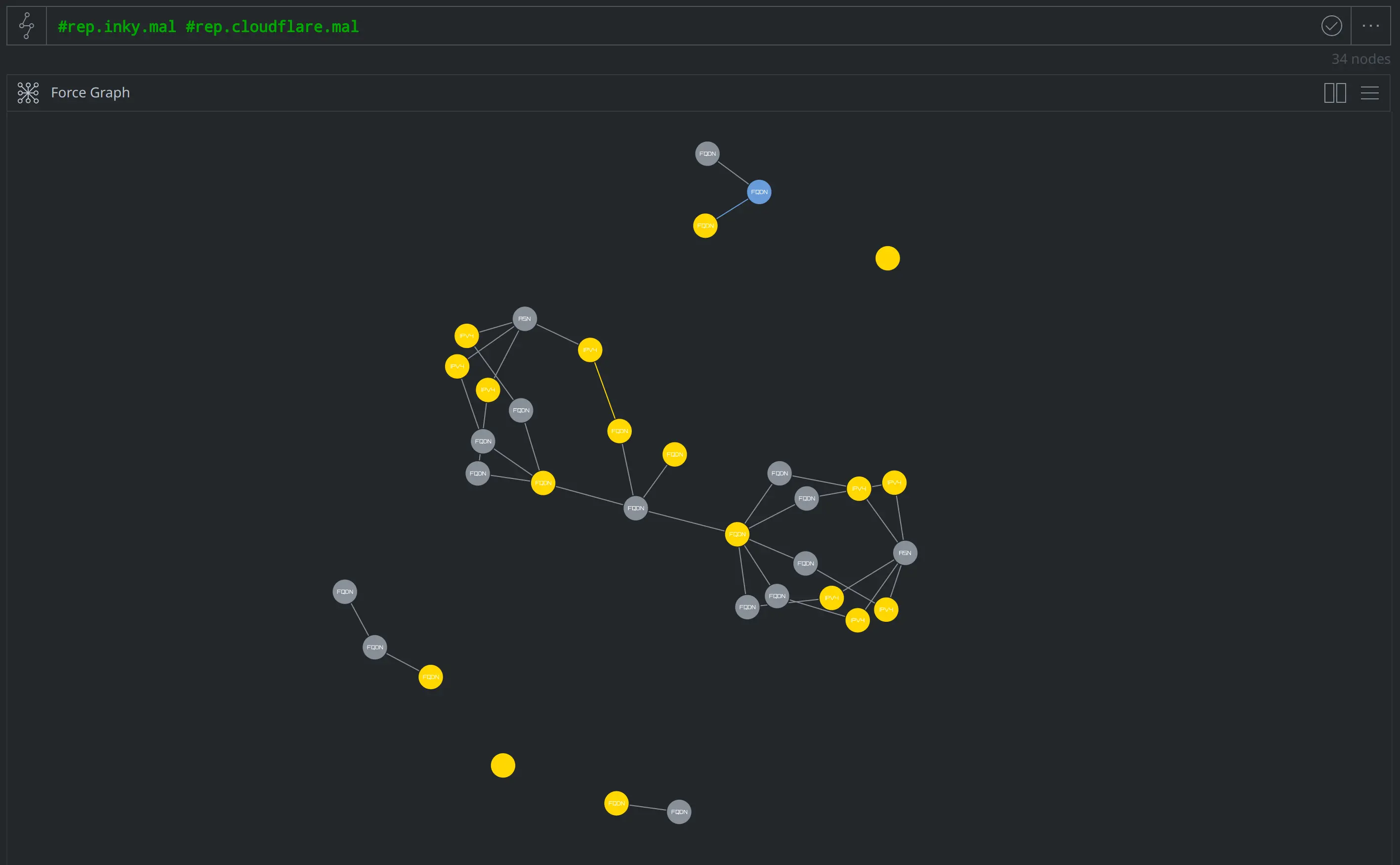
We then pivoted through the returned data (running additional enrichments as needed) to identify related infrastructure, determine whether a domain was compromised or otherwise controlled by the operator, track the chain of URL redirects, and identify suspected victims. The Force Graph display mode below represents the additional activity, infrastructure, suspected victims, and other related data we identified over the course of our research:
The Findings
The reported campaign was most likely a continuation of similar activity that was ongoing as of late February 2023 and potentially as early as November 2022. The activity was still ongoing as of the time of writing in mid April 2023.
The operators most likely relied on DocuSign and Concur-related lures during their earlier activity, based on the infrastructure we identified. However, we were unable to recover any phishing messages and could not determine whether the operators were also referencing Silicon Valley Bank. The operators may have only begun to reference Silicon Valley Bank beginning in mid-March 2023 to capitalize on media attention surrounding the bank’s recent collapse.
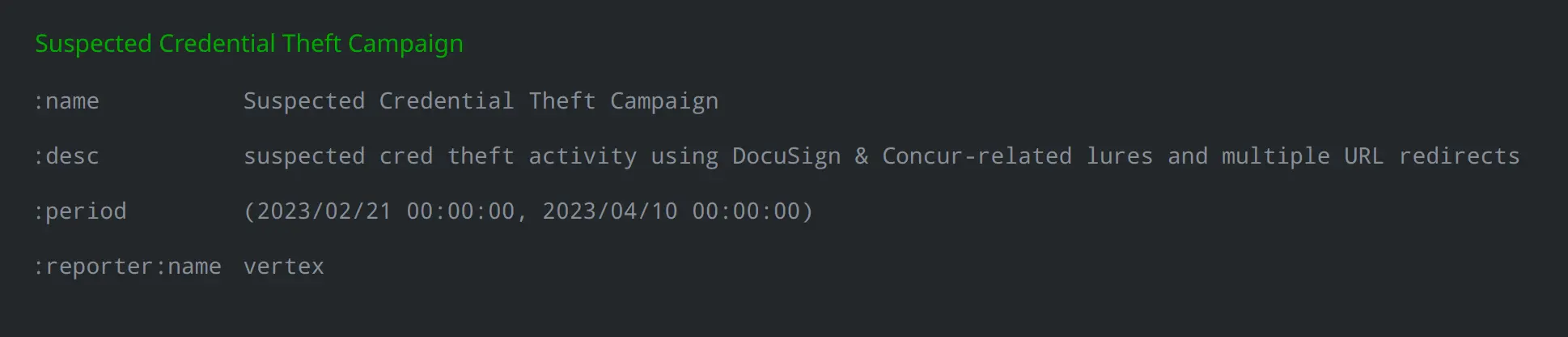
We used the ou:campaign node below to represent the campaign within our Synapse instance, the observed time frame of activity, and our assessment that the goal was to collect users’ credentials:
From a high level, the chain of events we observed appeared largely consistent with Cloudflare’s reporting, although we were able to identify additional infrastructure that the operators used at several of the steps. The chain of events and observed infrastructure employed during each step is outlined below:
Reported Use of Phishing Email with an Embedded Link
While we were unable to obtain any phishing emails associated with this activity, Cloudflare and Inky both reported that the operators used phishing emails that prompted the recipient to click on an embedded link.
URL Redirect to a Tracking/Analytics Link
The operators would then redirect the user to a URL using the domain bs.serving-sys.com, which is associated with Amazon Ad Server. The operators most likely used this to track which email recipients clicked on the embedded link in the phishing message.
URL Redirect to a Malicious Google Firebase Application
The bs.serving-sys.com URL contained an embedded URL and would subsequently redirect the user to a malicious Google Firebase application. The operators used several different Google Firebase applications, many of which incorporated DocuSign-related references into the domains, as seen below:
|
|
|
|
|
|
|
|
Based on screenshots from Joe Sandbox, the Google Firebase-related web pages may have displayed a message telling the user that they were being routed to their organization’s login webpage:
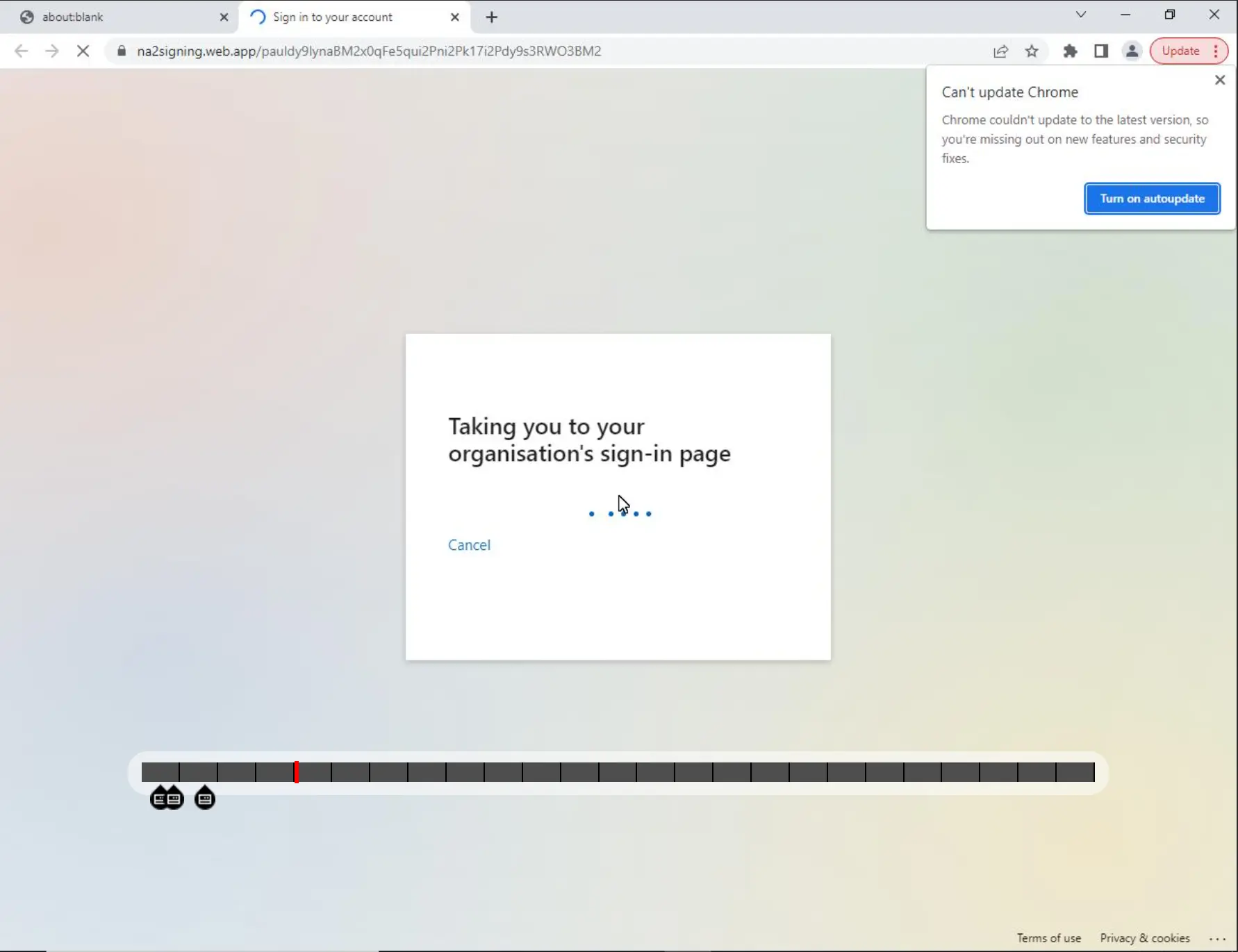
URL Redirect to Operator-Controlled Page Prompting User to Login
Cloudflare reported that the operators would then redirect users from the Google Firebase application to a likely compromised wordpress site, eaglelodgealaska.com, which redirected users once more to the operator-controlled docusigning.kirklandellis.net. We found that the operators also used several other likely compromised domains, including shareasale.com, inmobiliariacercasa.com, and thefootgroup.com.au, that similarly redirected users to operator-controlled login pages. In some instances, they appeared to skip the use of a likely compromised website and redirect users straight from a Google Firebase application to an operator-controlled login page.
Given that the domains used to host the login pages are the most visible part of the operators’ infrastructure, they most likely sought to evade scrutiny by using domains that appeared to belong to legitimate organizations. In some instances, the operators used domains that had previously belonged to organizations that had since allowed the registration to lapse, giving the operators the opportunity to re-register the domain themselves. In other cases, they used domains that they had most likely designed to masquerade as the legitimate domain of an existing organization. Examples of these latter domains include:
Operator Domain |
Likely Masquerading as... |
|---|---|
|
|
|
|
|
|
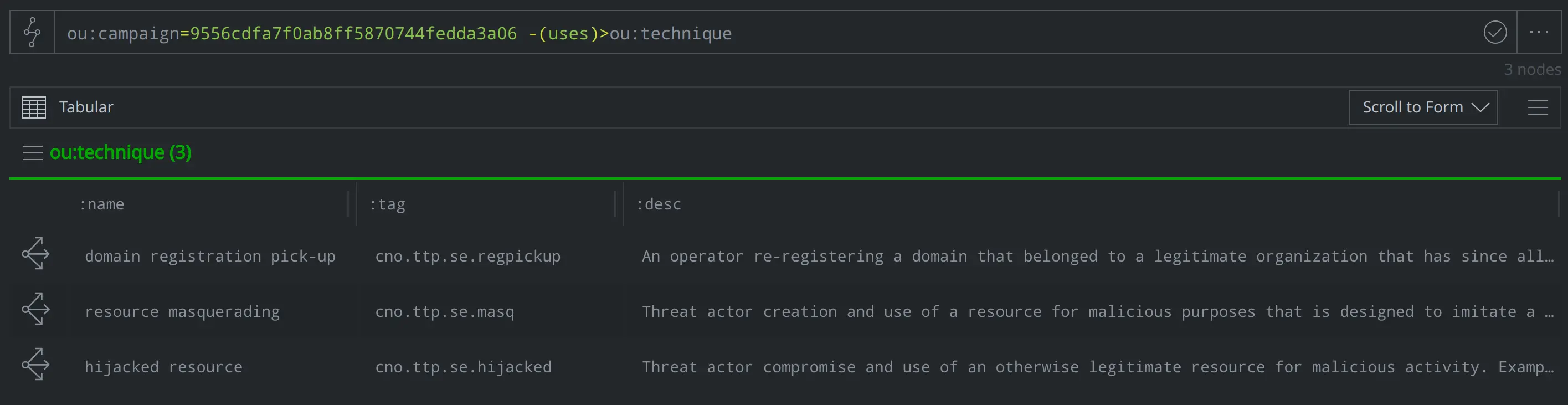
We captured these techniques (the use of likely compromised domains, re-registration of domains previously associated with legitimate organizations and use of domains masquerading as the domains of legitimate organizations) as ou:technique nodes that we linked back to the ou:campaign node with a -(uses)> light edge. Each ou:technique node has a tag that we applied to the inet:fqdn nodes representing the domains corresponding to the technique.
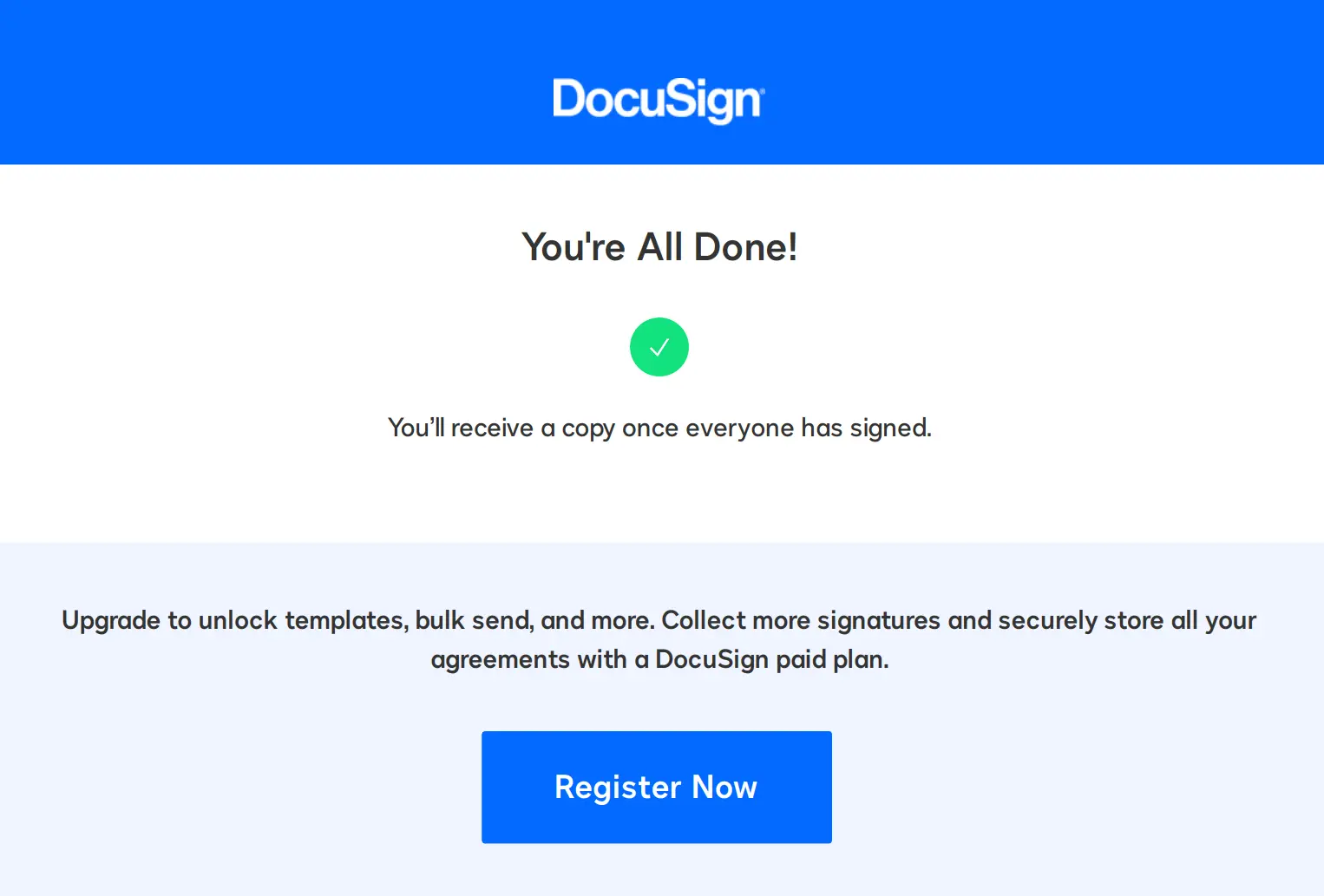
Final Redirect to a Legitimate Concur or DocuSign Page
After the user entered their credentials, the operators would redirect them once more to a legitimate Concur or Docusign page. Some of the pages, such as that shown below (postsign.docusign.com), thank the user for signing the document:
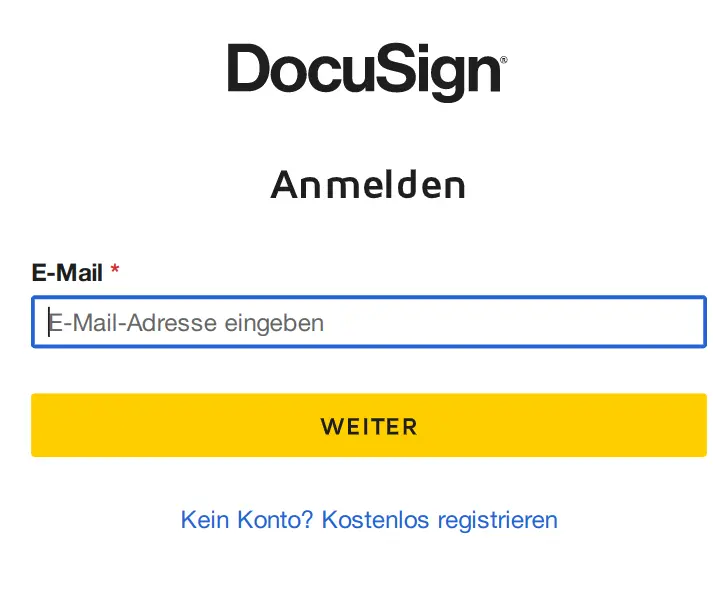
However, in some instances, users were directed to DocuSign (account.docusign.com) and Concur (www.concursolutions.com) login pages:

And in at least a few cases, users were redirected to a legitimate Concur page displaying a warning that it was unable to navigate to the requested URL:

Likely Victims
The operators most likely sought to target enterprise credentials based on their use of DocuSign and Concur-related lures, and may have had a particular interest in organizations associated with financial and technology industries. However, we suspect that this activity was not highly targeted given that the likely victims were associated with companies across a range of industries and countries. When investigating the operator-controlled login pages, we identified multiple URLs containing what were most likely the email addresses users had entered when prompted for their credentials. We used these email addresses to identify 138 likely victims of this activity, who are associated with at least 125 unique organizations, based on the email domains. The majority of these organizations are headquartered in the US, followed by the UK and Canada, although we identified organizations headquartered across more than 15 countries overall. Although these organizations are affiliated with a range of industries, we categorized the majority as falling into financial and technology-related industries.
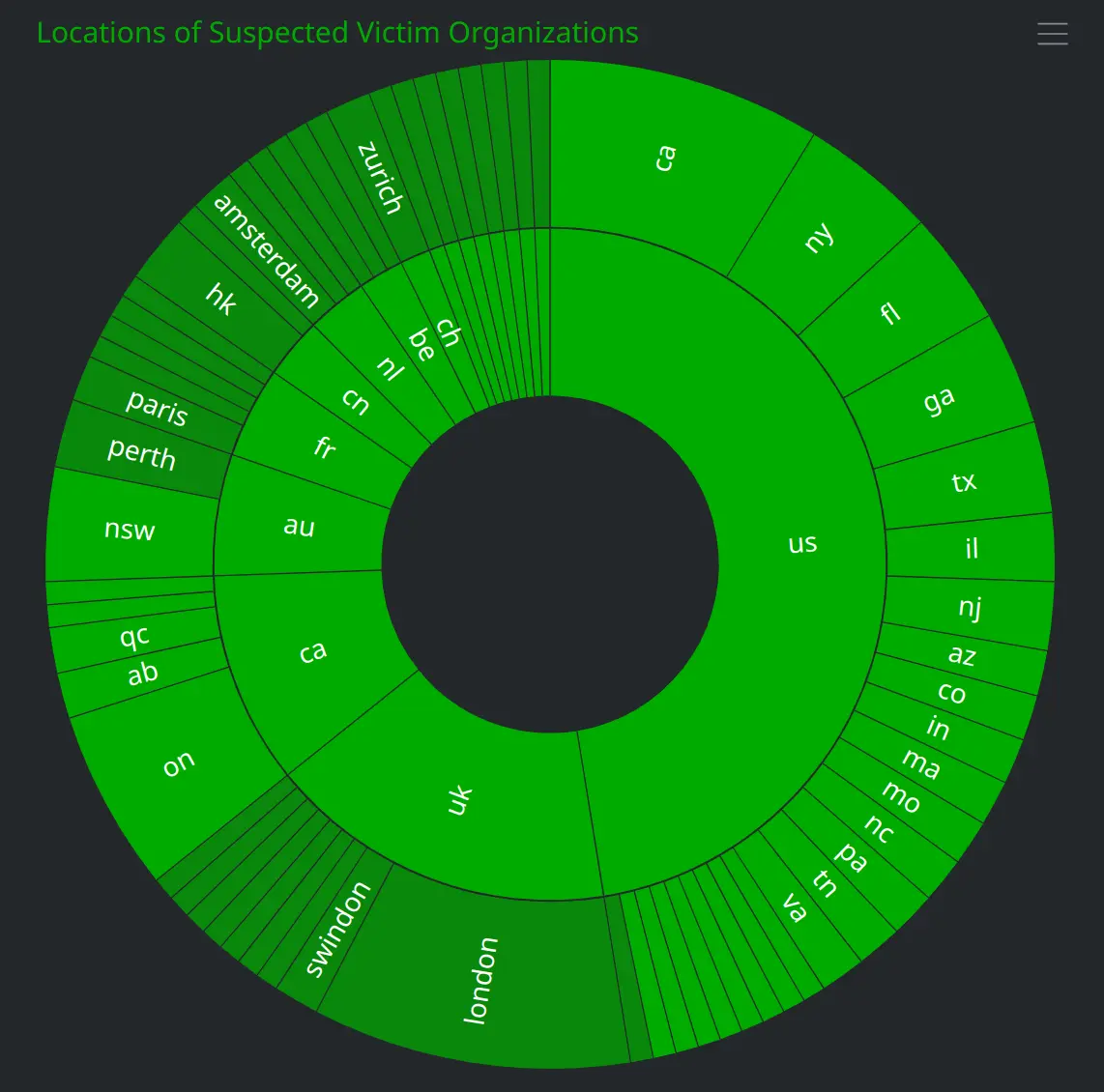
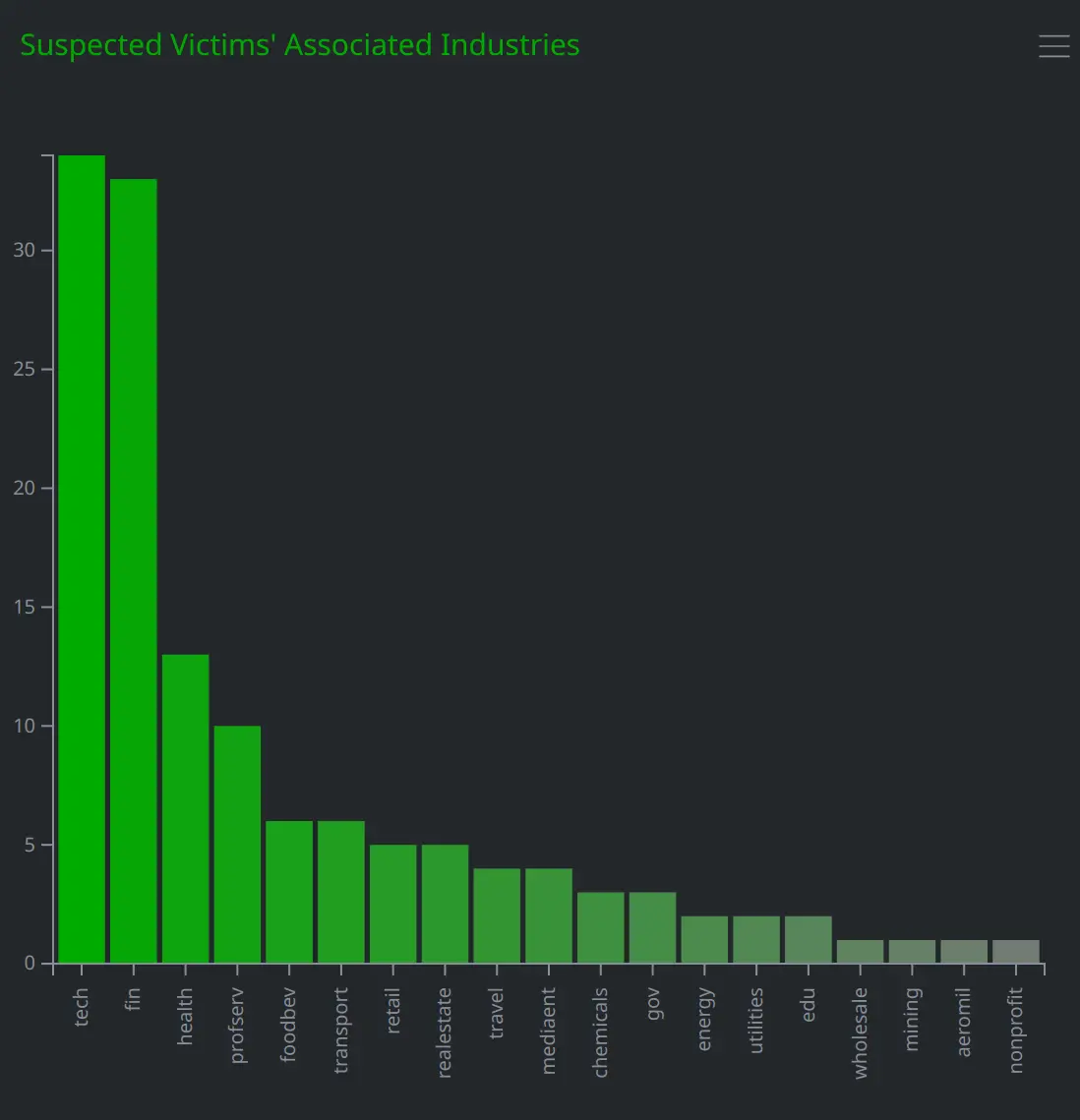
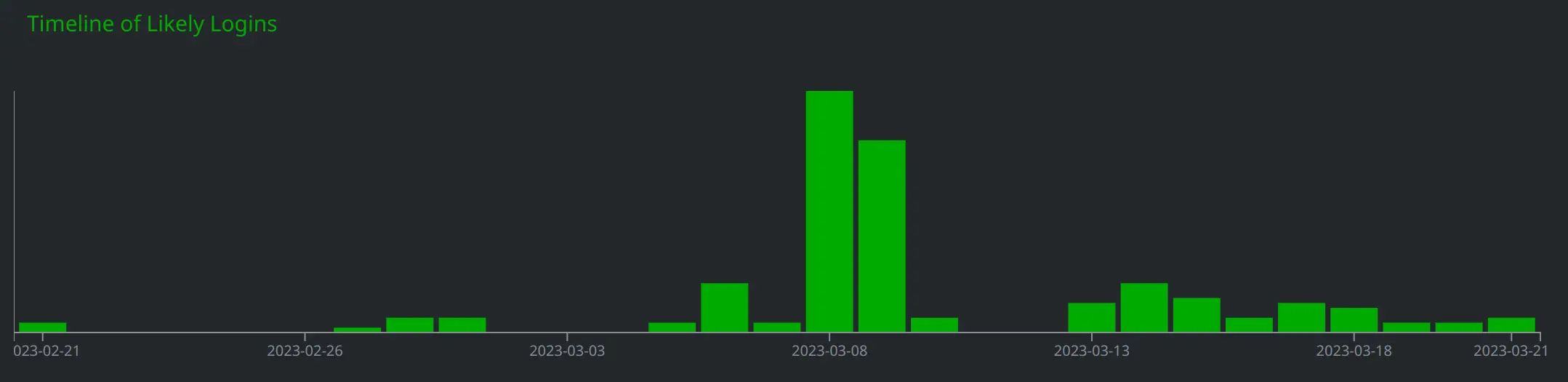
We also created risk:attack nodes for each of the inet:urlredir nodes with a destination URL containing a suspected victim’s email address. These risk:attack nodes, which we modeled to the overall ou:campaign node, used the first .seen time on the inet:urlredir node as the :time property value, and were linked to the associated inet:urlredir and inet:email nodes by -(uses)> and -(targets)> light edges. Based on the timeline view of these risk:attack nodes, shown below, the majority of the targeted users appeared to enter their credentials into the fake login pages between March 8th and 9th 2023:
Analyzing Suspected Credential Theft Operations with Synapse
In this blog we walked through our use of Synapse to research and analyze suspected credential theft activity. We began with public reporting, which we were able to import and model, before leveraging Synapse Power-Ups to enrich the indicators with additional data. Despite limited visibility in some areas (we never were able to obtain any of the phishing emails), we were able to use Synapse to identify additional activity, overlapping infrastructure, actor techniques, and likely victimology.
To learn more about Synapse, join our Slack community, check out our videos on YouTube, and follow us on Twitter.
