Analyzing Two of Russia's Military Intelligence Units with Synapse
by savage | 2023-04-25
In July 2018 and October 2020, the US Department of Justice indicted multiple Russian nationals for conducting malicious cyber operations against the US and its allies. The indictments alleged that the individuals worked for two units within Russia’s military intelligence agency, the Main Intelligence Directorate of the General Staff of the Armed Forces, better known as the GRU. We were able to model the information in the indictments pertaining to the identified individuals and intelligence units for which they allegedly work as Synapse’s data model is designed to capture both technical and strategic information. This means that not only can we record and ask questions about technical details such as user accounts, malware samples, and infrastructure, but we can also document and analyze non-technical information about the individuals and entities engaged in malicious operations. In this blog, we’ll walk through some examples of how modeling information about the GRU units and indicted members allows us to then ask questions of that data to learn more about the individual operators, unit compositions, and sponsorship.
A Note About the Concept of an Organization in Synapse:
When it comes to modeling data in Synapse, our concept of what constitutes an organization is intentionally broad. We’ll use the ou:org form to represent any human organization, rather than restrict its use to a company or other formalized entity. This means that in terms of modeling, an organization could be:
A company
A club
The HR department
An international organization
A federal government
A criminal syndicate
A terrorist cell
Using Synapse to Ask Questions about GRU Units 26165 and 74455
The two indictments identify 17 Russian nationals who are allegedly members of two Moscow-based intelligence units within Russia’s GRU, Unit 26165 and Unit 74455, which are also known as the 85th Main Special Service Center (GTsSS) and the Main Center for Special Technologies (GTsST) . The indictments note the street addresses for both units, which, along with FBI Wanted posters, provide the following information for each of the indicted GRU officers:
Name (in both English and Cyrillic)
Photograph
Date and location of birth
Last known location
Military rank (if known)
Unit for which they worked
Specific team and role within the unit (if known)
Handles and aliases used during malicious activity highlighted in the indictment
After modeling the indictments and FBI Wanted posters in Synapse using media:news nodes, we captured the rest of the relevant data primarily using the following forms:
ou:org
ou:suborg
ps:contact
ou:position
geo:place
Modeling this information allowed us to answer questions such as:
1) What is the relationship between Units 26165 and 74455 and other organizations that we know of within Synapse?
We can lift and pivot from the ou:org nodes for Unit 26165 and Unit 74455 to see that both units are modeled as ou:suborg nodes and linked to Russia's Main Intelligence Directorate of the General Staff of the Armed Forces (GRU). Note that we took advantage of the Embed Column feature to display the nodes by organization name:
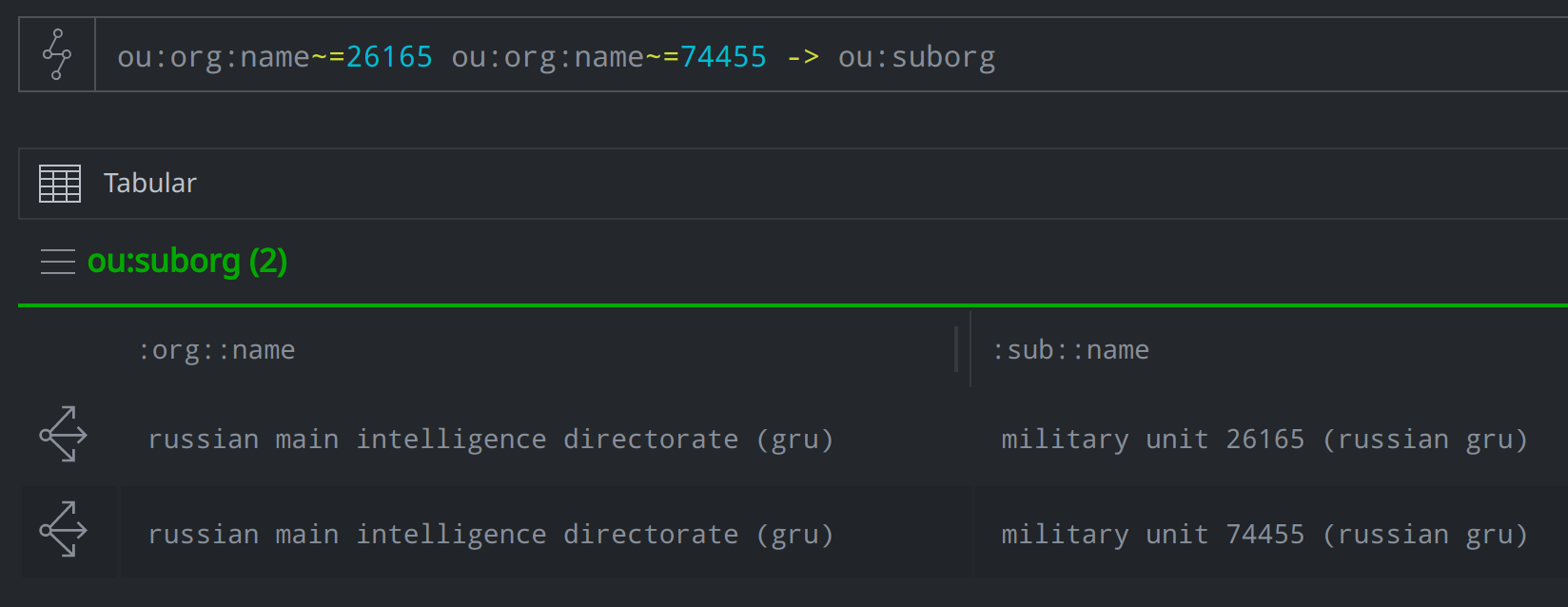
When we pivot again from the ou:org for the GRU, we’re able to see all the military intelligence units within that same directorate that we know of and have previously modeled. We displayed those units by the :name and :loc properties in the image below:
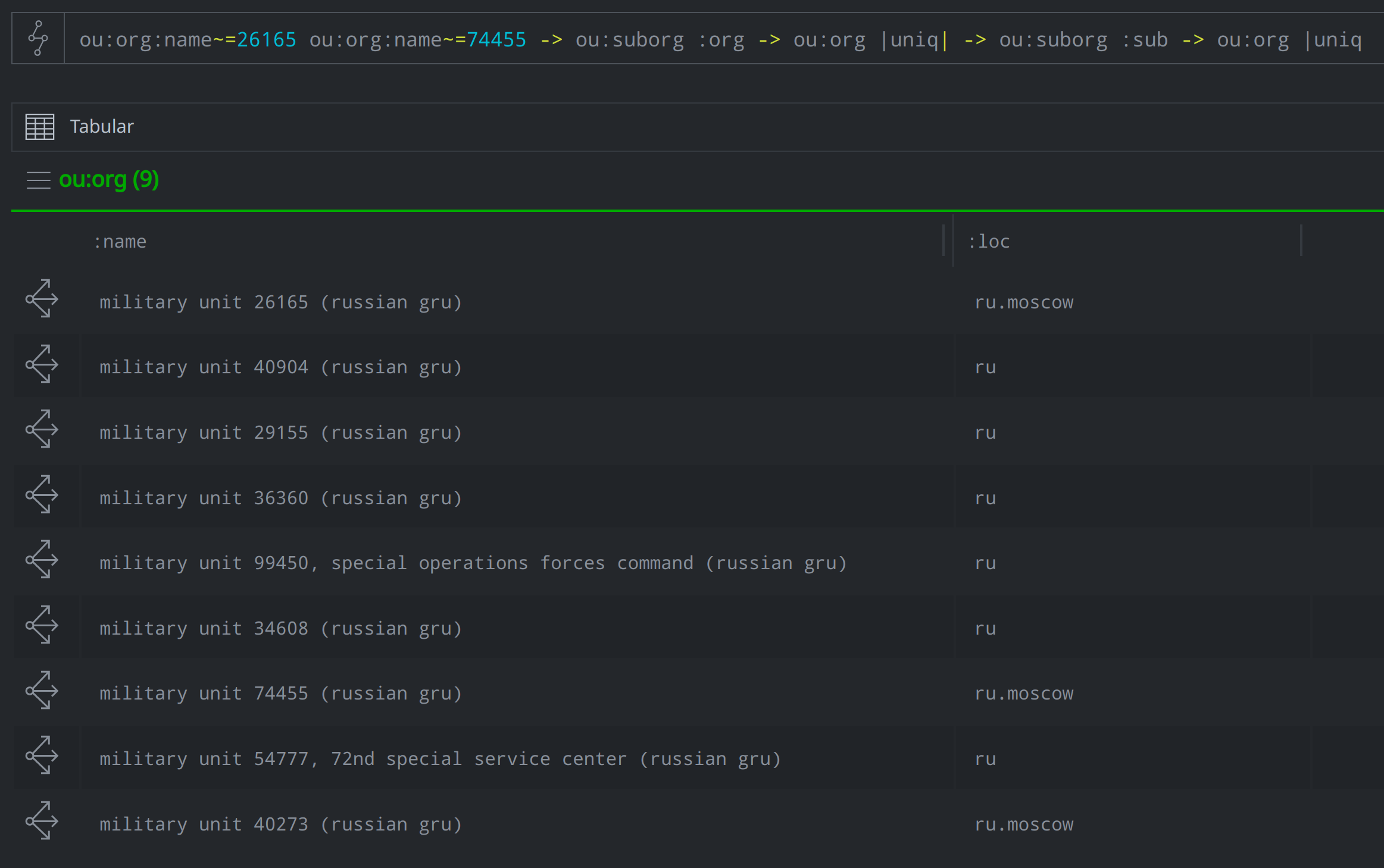
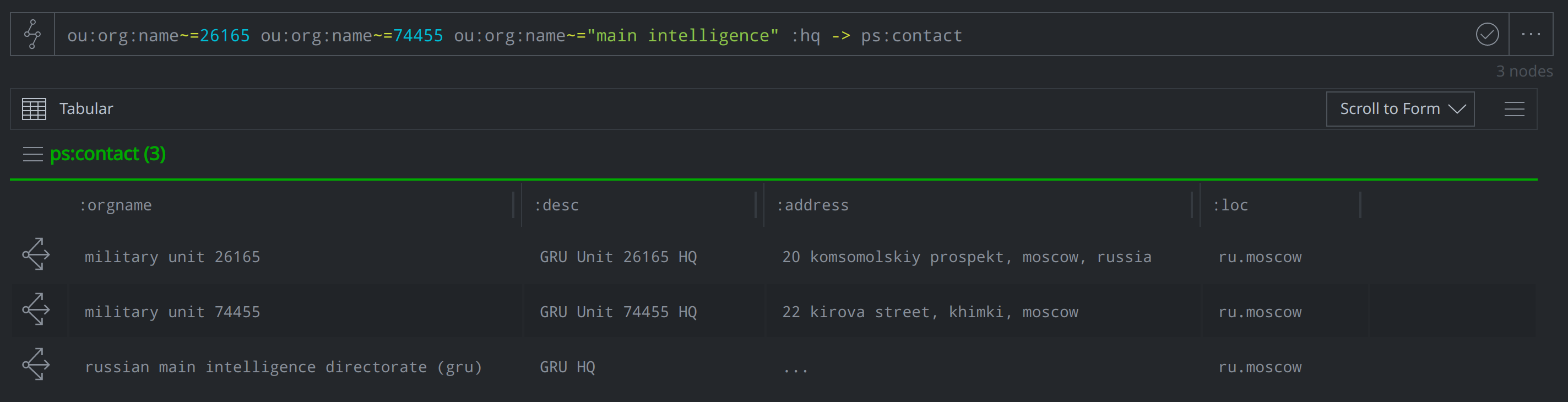
2) Where are Units 26165 and 74455 based? Where are they in relation to the GRU headquarters?
According to both indictments, GRU Unit 74455 primarily operates out of "22 Kirova Street, Khimki, Moscow, Russia," while, per the July 2018 indictment, GRU Unit 26165 is "located at 20 Komsomolskiy Prospekt, Moscow, Russia." While we were unable to find an address for the GRU headquarters, we were able to locate the building on a map and note the geolocation coordinates. We captured these details in ps:contact nodes modeled to the ou:org nodes' :hq property:
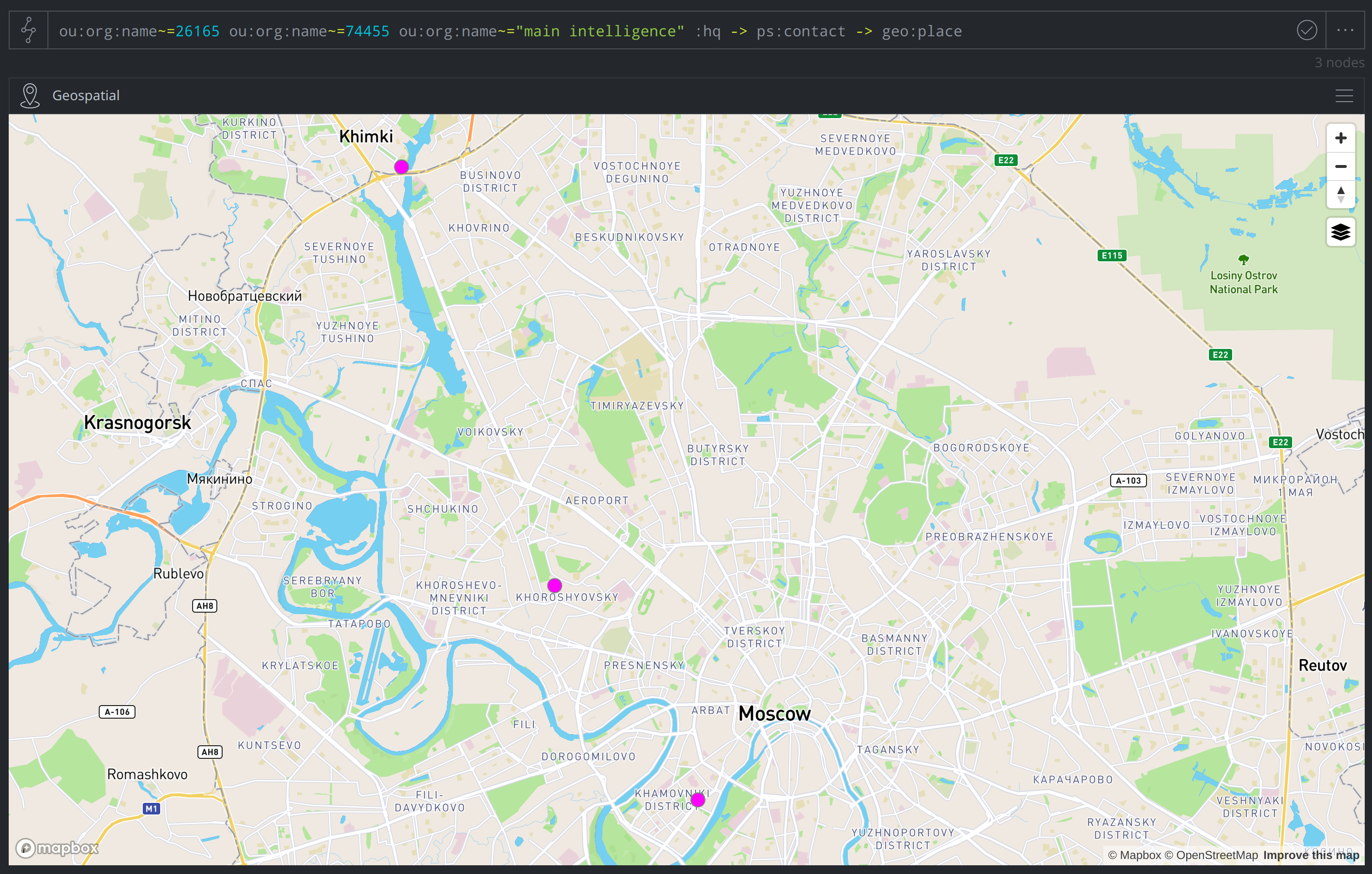
When we created the ps:contact nodes, we populated the :place property so as to corresponds to a geo:place node with the geolocation data for the organization. We can lift these nodes (shown in pink, below) in Geospatial Mode to see where the organizations are located on the map, and can select each node to view its properties and other details in the Details Panel:
3) What members of Unit 26165 do we know of? What are their names and roles within the unit? What about members of Unit 74455?
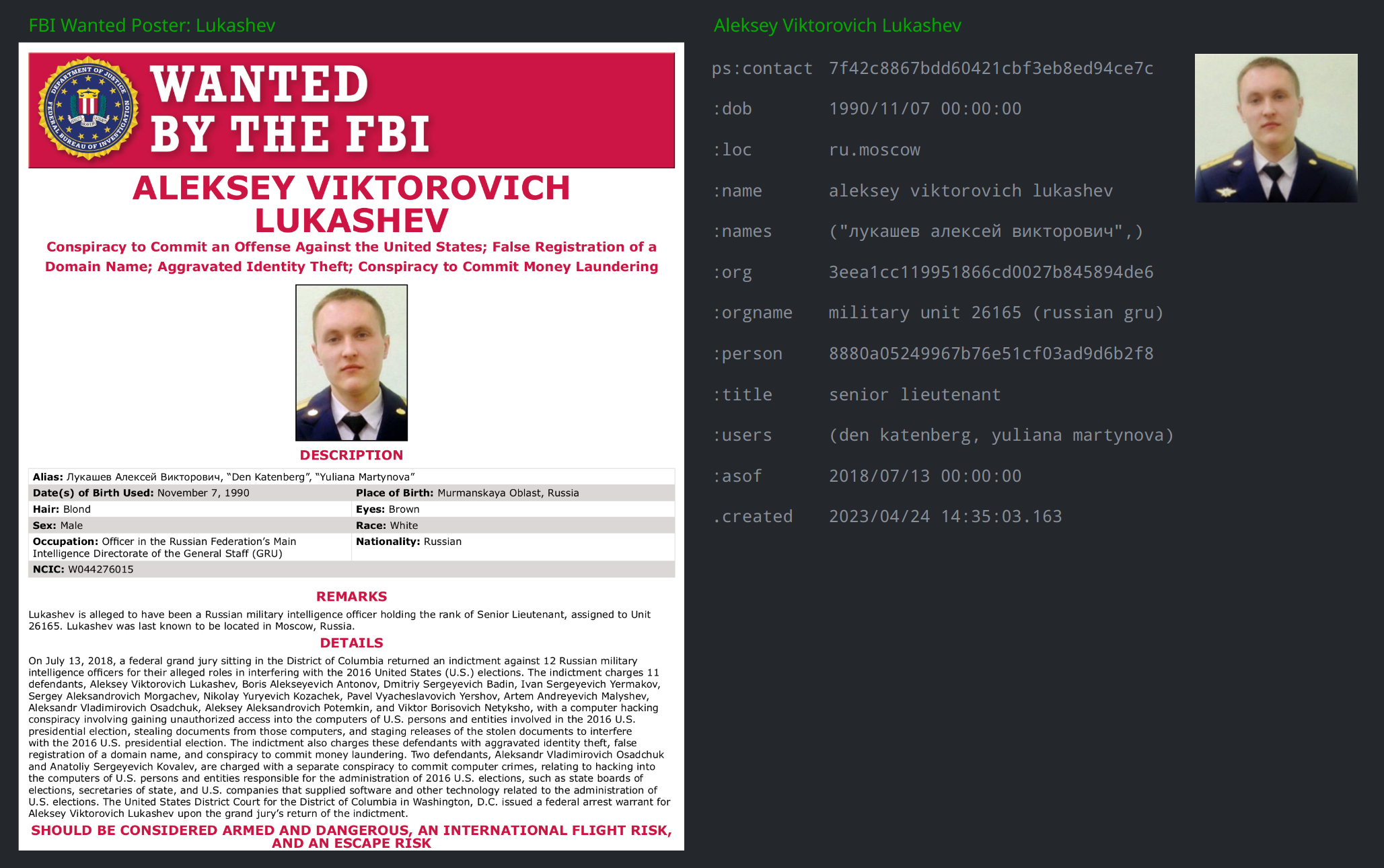
The two indictments identify multiple members of GRU Units 26165 and 74455 by name, and in some cases, also note their military rank and role in the unit. We primarily captured this information using ps:contact nodes, which let us connect each named individual to their respective GRU unit and title, while also noting their name (we used the :names property to capture the names in both English and Cyrillic). In several instances, the indictment included associated "Wanted" posters with labeled photographs. We uploaded the individual photos as file:bytes nodes, and linked them to the relevant ps:contact node using the :photo property. If we had enough information to model the units’ reporting structures, we could do so using the ou:position nodes to model a role and use the :reports property to connect it with other ou:position nodes that the individual oversees.
The following image is an example of how we captured this data. The image is from a Story in which we paired FBI Wanted Poster that accompanied the indictment of GRU officer Aleksey Viktorovich Lukashev alongside the ps:contact node capturing the relevant details:
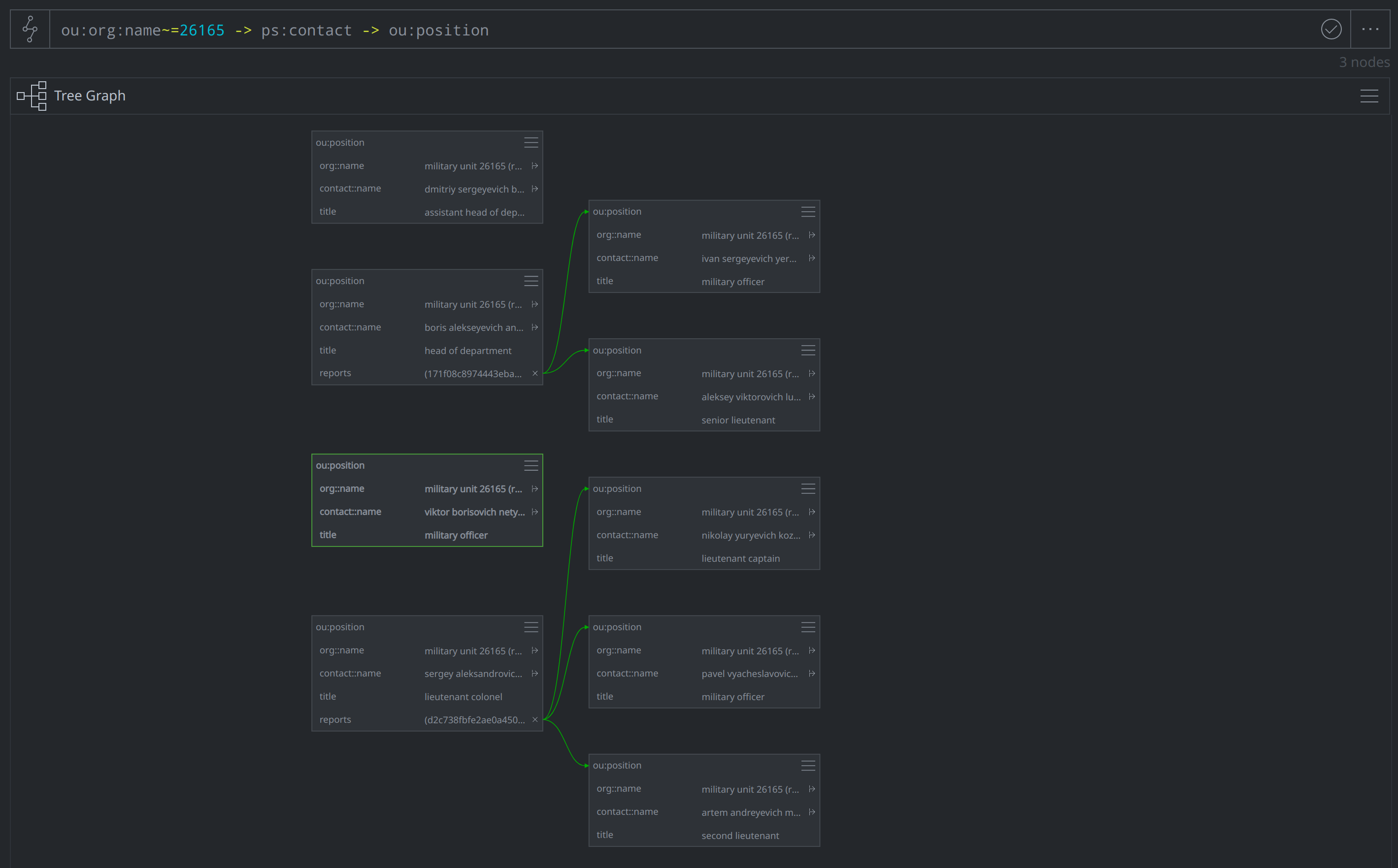
The indictments noted that two members of Unit 26165 led teams that included several of the other indicted individuals, which we were able to reflect using the :reports property in the ou:position nodes. This let us build out a partial hierarchy for Unit 26165, which is shown below in Tree Graph Mode:
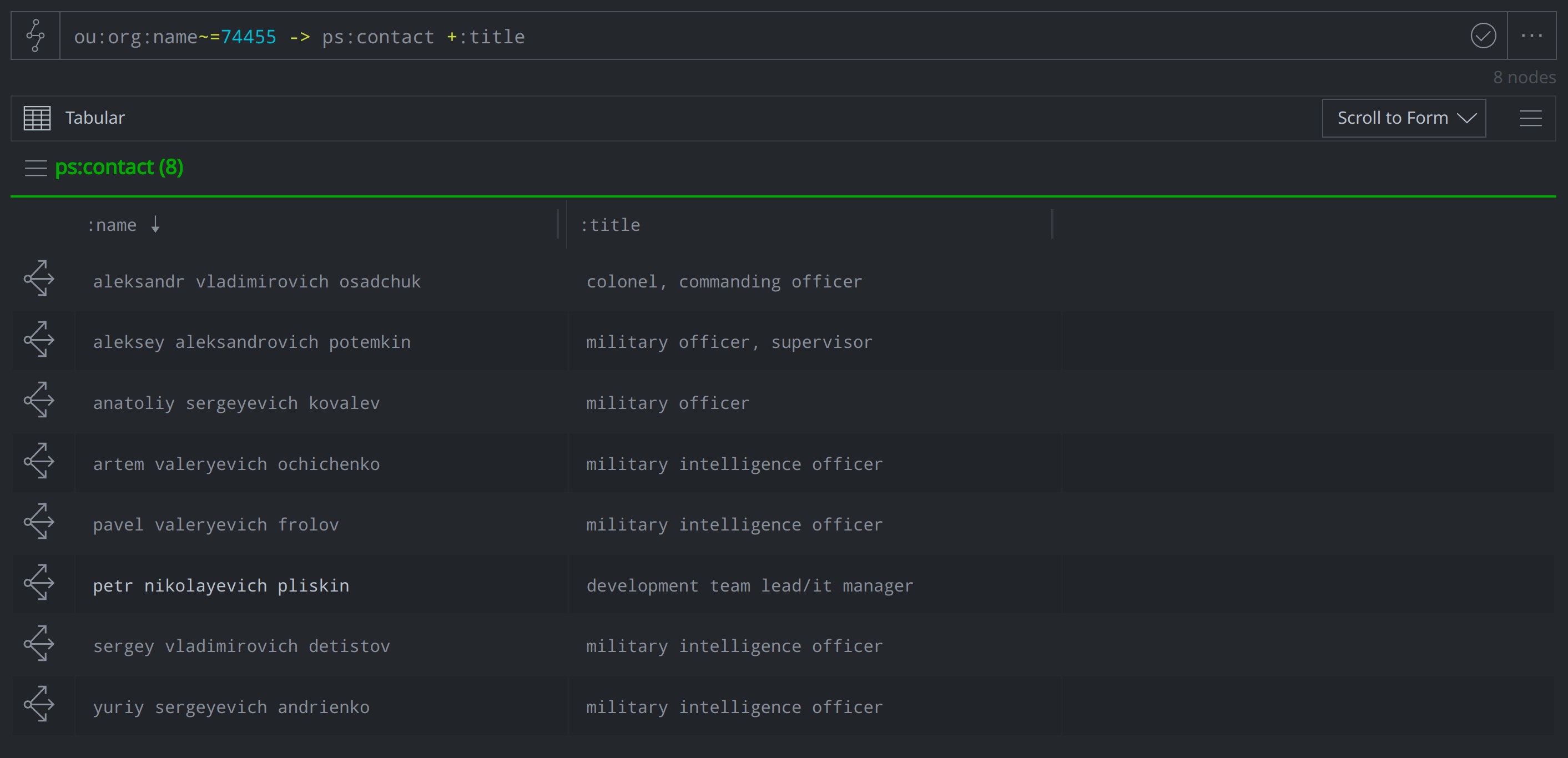
While the ou:position form is a helpful way to capture hierarchy, there are instances in which we might only know titles and not whether certain individuals oversaw others. In such cases, we can just capture this information using ps:contact nodes. The known members of Unit 74455 are listed here:
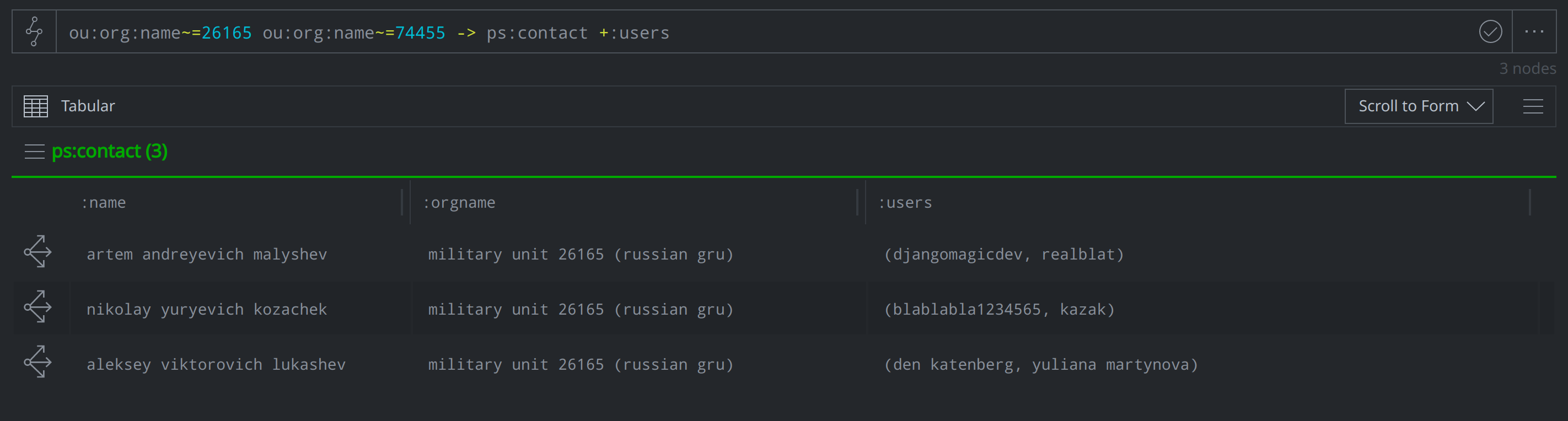
4) Were any members of Units 26165 and 74455 using handles (that we know of)?
The indictments noted handles and usernames that some of the indicted individuals had employed, which we were able to capture by populating the :users property in ps:contact:
5) Do we have any associated web accounts modeled for those usernames?
We made a secondary property to secondary property pivot (using :users) to pivot from the ps:contact nodes to any inet:web:acct nodes. Unfortunately it looks like we don’t have any associated inet:web:acct information modeled in Synapse:

While it is out of the scope of this piece, an analyst may at this point choose to navigate back to the identified usernames and query the Synapse-Google Power-Up (or another resource) to search for and model the associated web accounts.
Modeling Organization Data to Enable Analysis
Modeling the information from the two indictments pertaining to GRU Units 26165 and 74455 allowed us to encode and keep track of that data, as well as ask analytical questions, as shown above. Synapse’s extensive data model and our broad concept of what constitutes an organization means that we have enough flexibility when modeling that we can capture and record a range of details about any human-based entity, from threat groups to countries to Fortune 500 companies. In this particular example of modeling the two GRU units, we were working with somewhat limited data. However, most of the nodes are GUID forms , which allowed us to model what information was available in the two indictments.
To learn more about Synapse, join our Slack community, check out our videos on YouTube, and follow us on Twitter.
