Using the Synapse-Mitre-Attack Power-Up to Ask Questions of the MITRE ATT&CK Framework
by savage | 2023-07-12
Ask most threat intelligence analysts and you’ll likely find that they have at least heard of the MITRE ATT&CK® framework. MITRE first developed the ubiquitous ATT&CK framework in 2013, intending for ATT&CK to serve as a "knowledge base of adversary tactics and techniques based on real-world observations". In addition to cataloging tactics and techniques identified in Enterprise, ICS, and Mobile environments, ATT&CK also lists software and groups linked to intrusion activity, as well as mitigation strategies. Today, organizations often reference the framework when reporting on threat activity or sharing new research. Here we’ll show how we can use the Synapse-Mitre-Attack Power-Up to import and map references to ATT&CK elements.
What is the Synapse-Mitre-Attack Power-Up?
Synapse-Mitre-Attack is a publicly available Synapse Power-Up that analysts can use to retrieve the current Enterprise, ICS, and Mobile matrices from MITRE's public Github repository and represent them within Synapse. Analysts can then link ATT&CK elements to other nodes, as well as to tags, providing the ability to ask questions of the framework and related data.
Representing and Querying the MITRE ATT&CK® Matrix and Elements Within Synapse
Run the mitre.attack.sync command to import and model the ATT&CK-cataloged tactics, techniques, mitigations, software, and groups in your Synapse instance. This will give you the ability to view and navigate the ATT&CK matrices without needing to leave Synapse. The Power-Up will specify the associated matrix (Enterprise, Mobile, or ICS) for tactics, techniques, and mitigation nodes, and will also capture the page URLs for each. Therefore, if you need to reference the web page itself you can do so by clicking the link in the :url property and selecting the "open" option.
Having the MITRE ATT&CK® framework represented within Synapse means that you can run queries to answer questions such as:
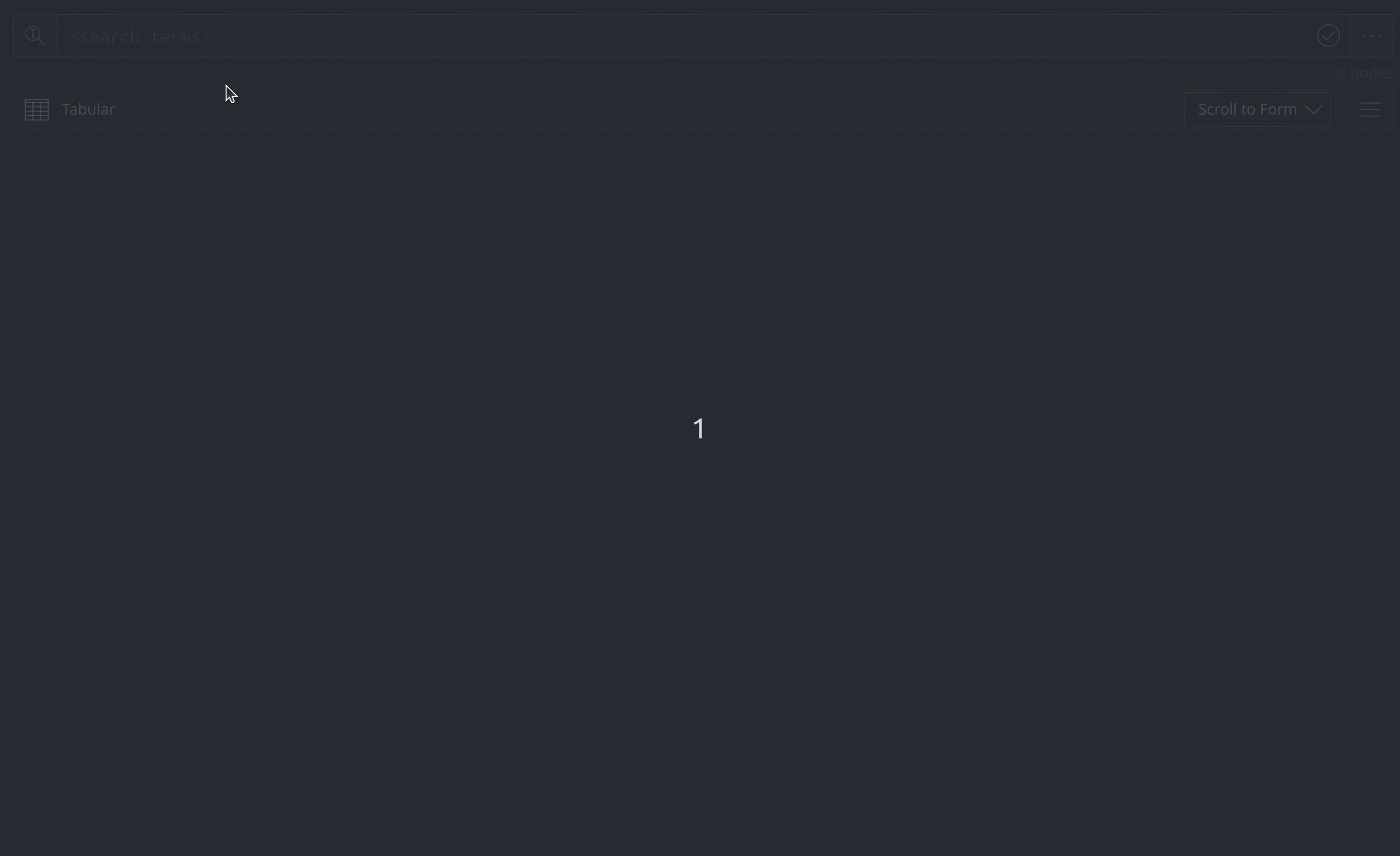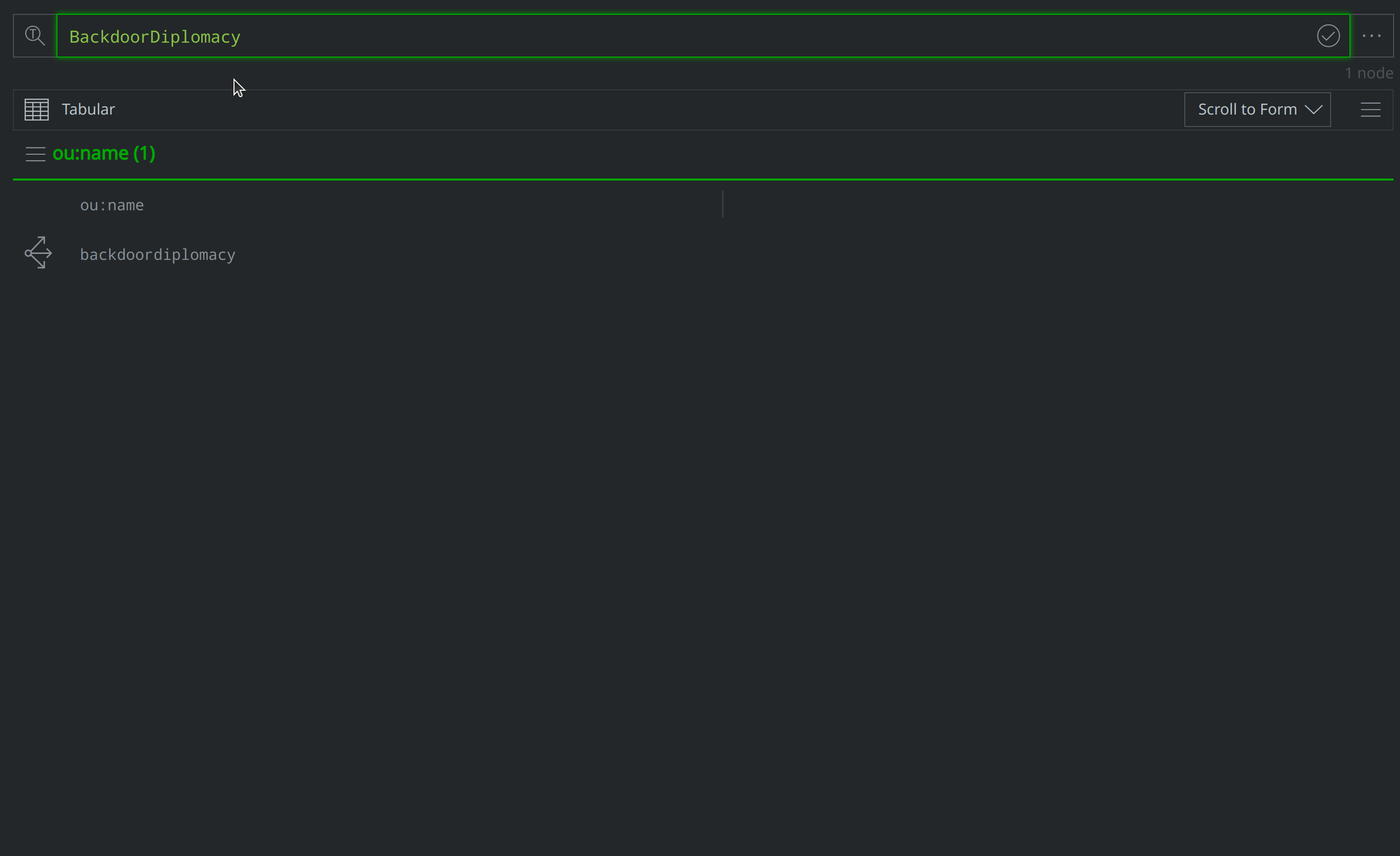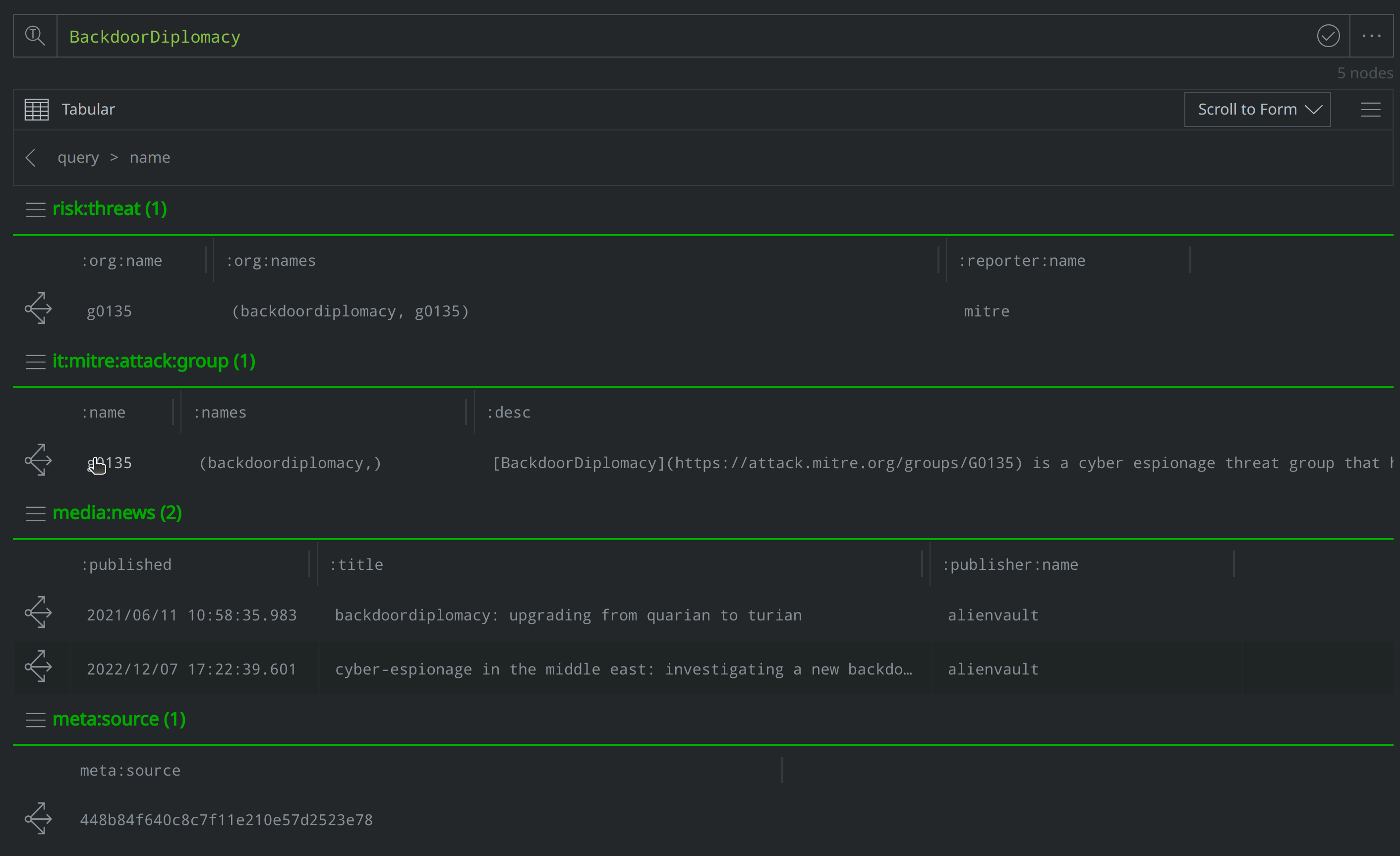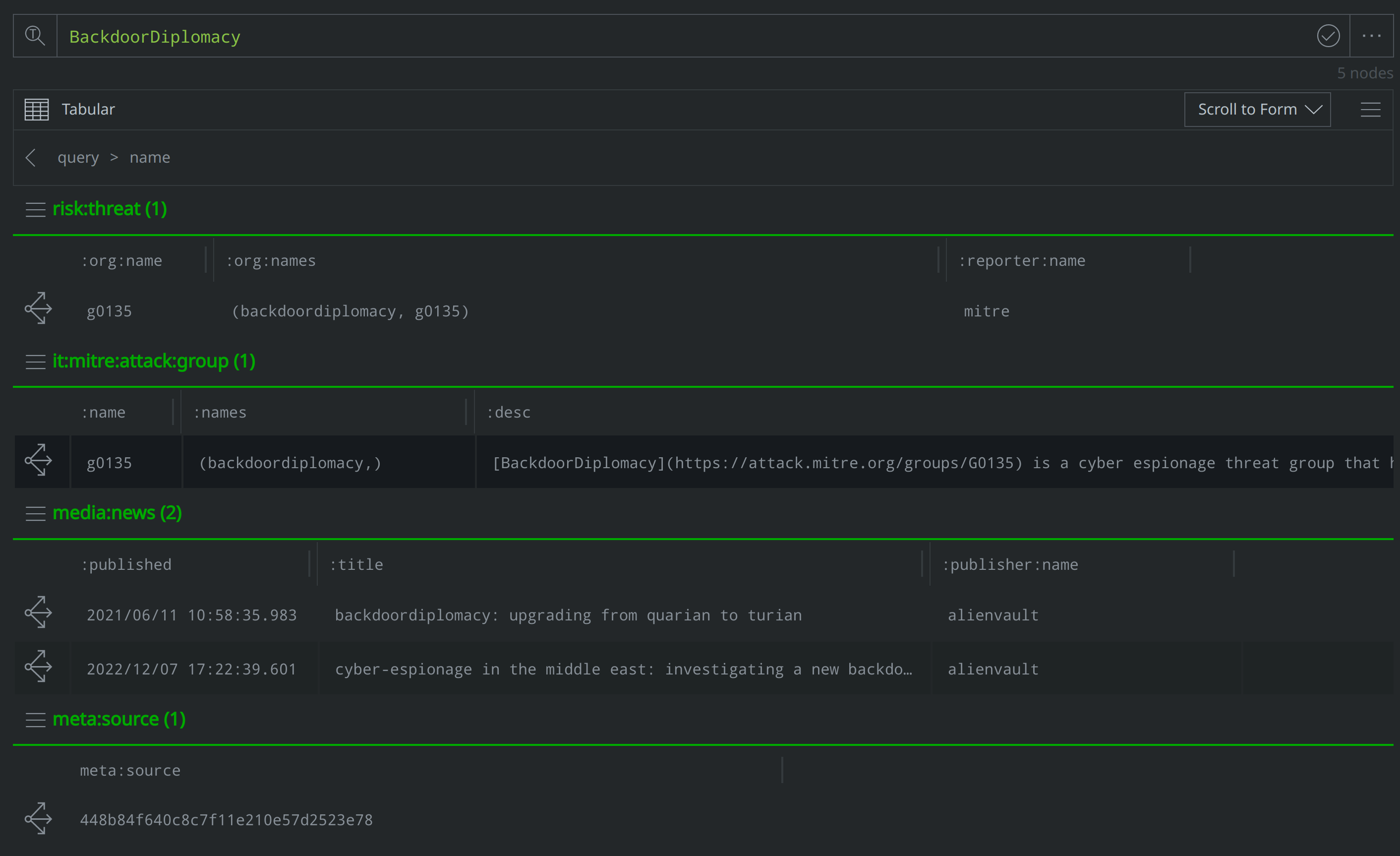
How can I use Text Search query mode to look-up the ATT&CK group equivalent to "BackdoorDiplomacy"?
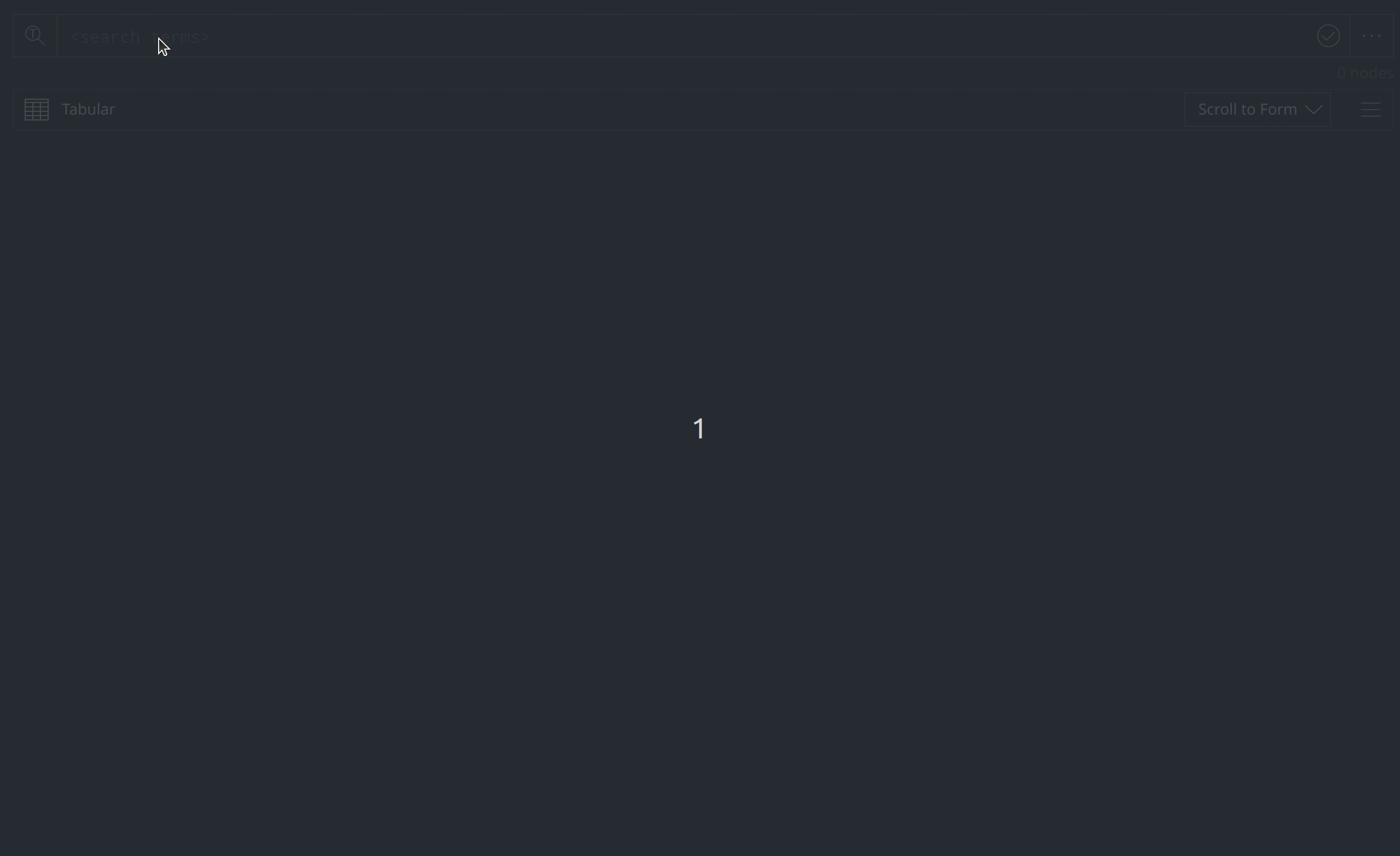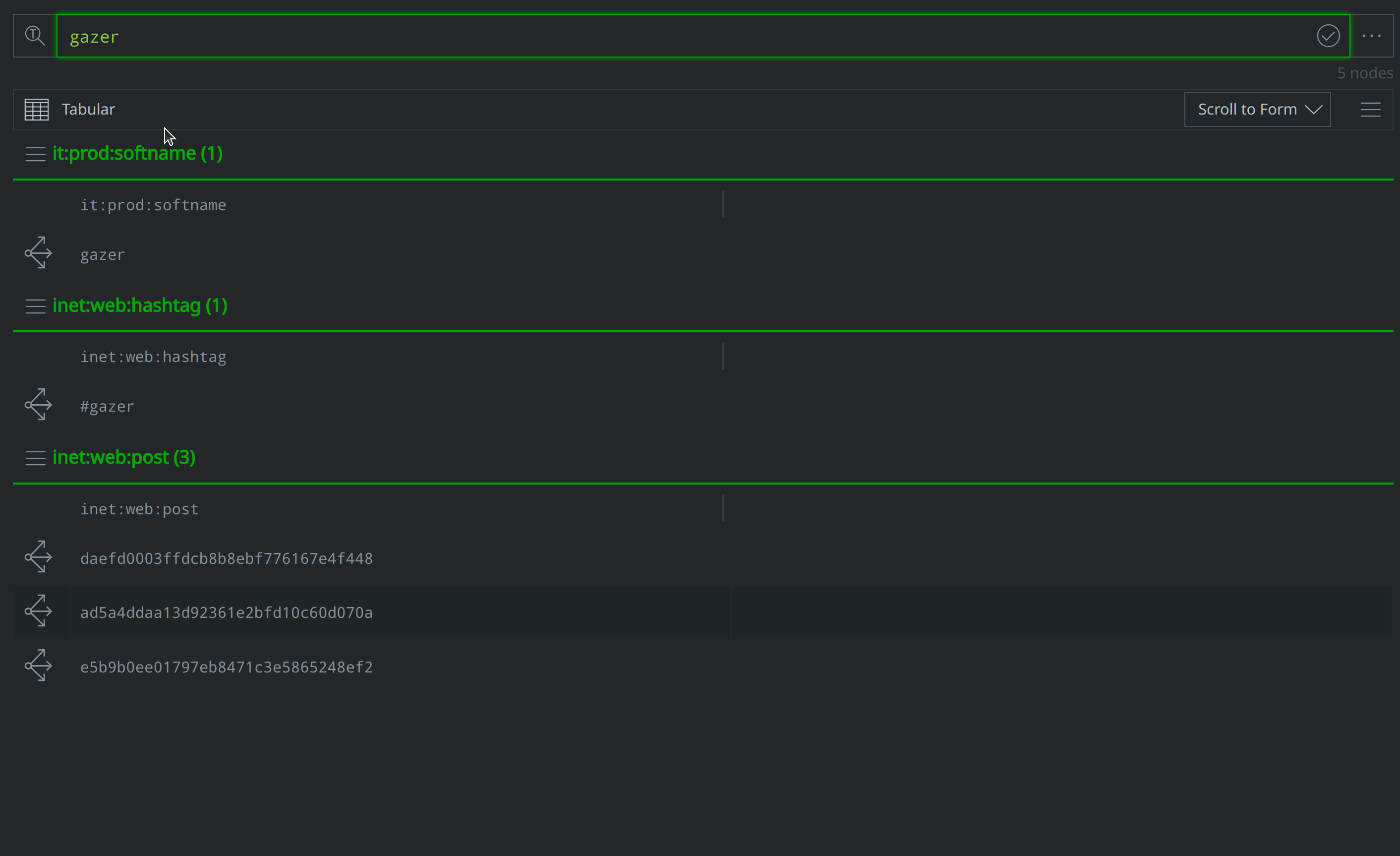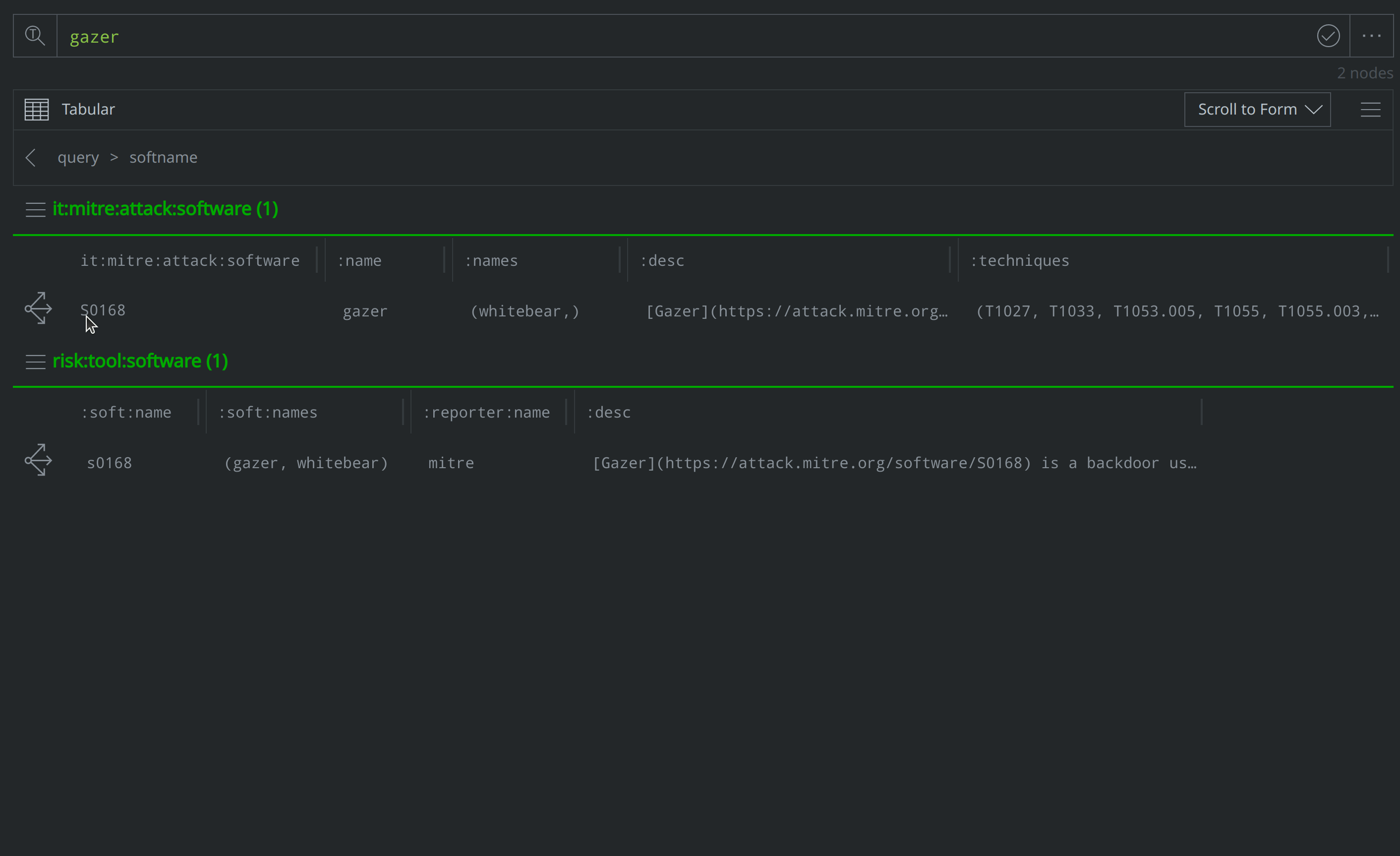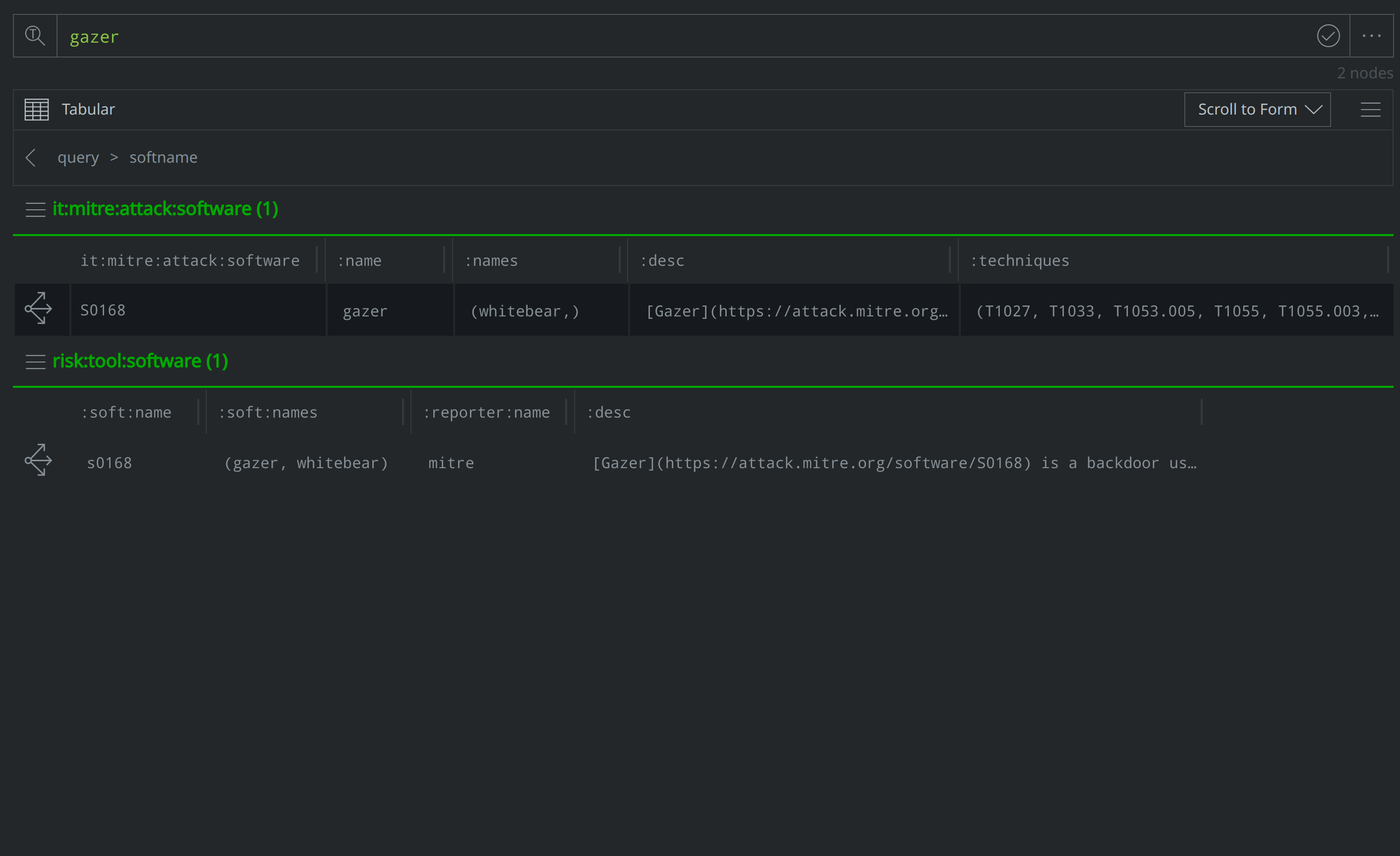
How can I use Text Search query mode to look-up the ATT&CK software equivalent to "Gazer" malware?
How can I use Storm mode to view all threat groups ATT&CK tracks?
it:mitre:attack:group
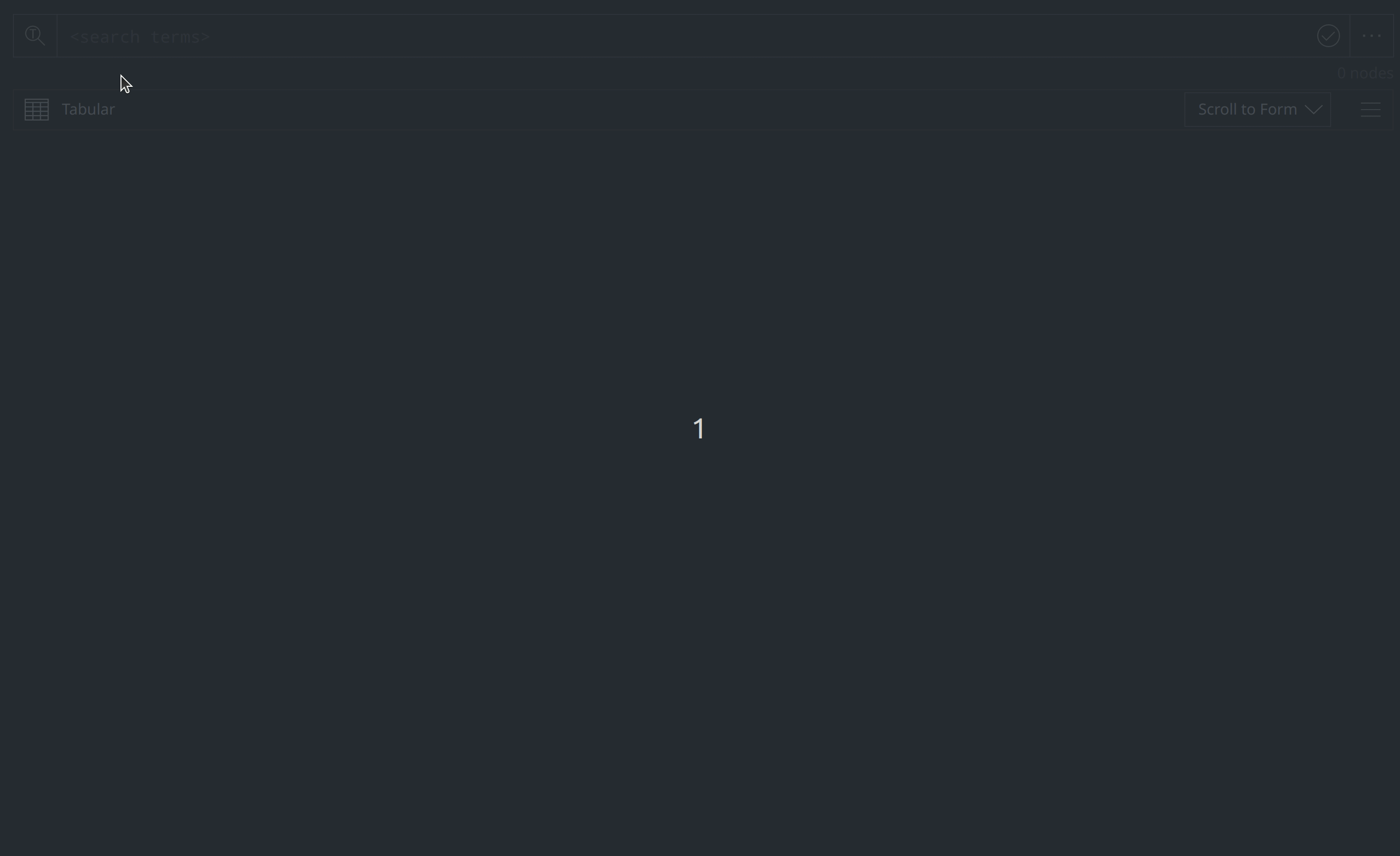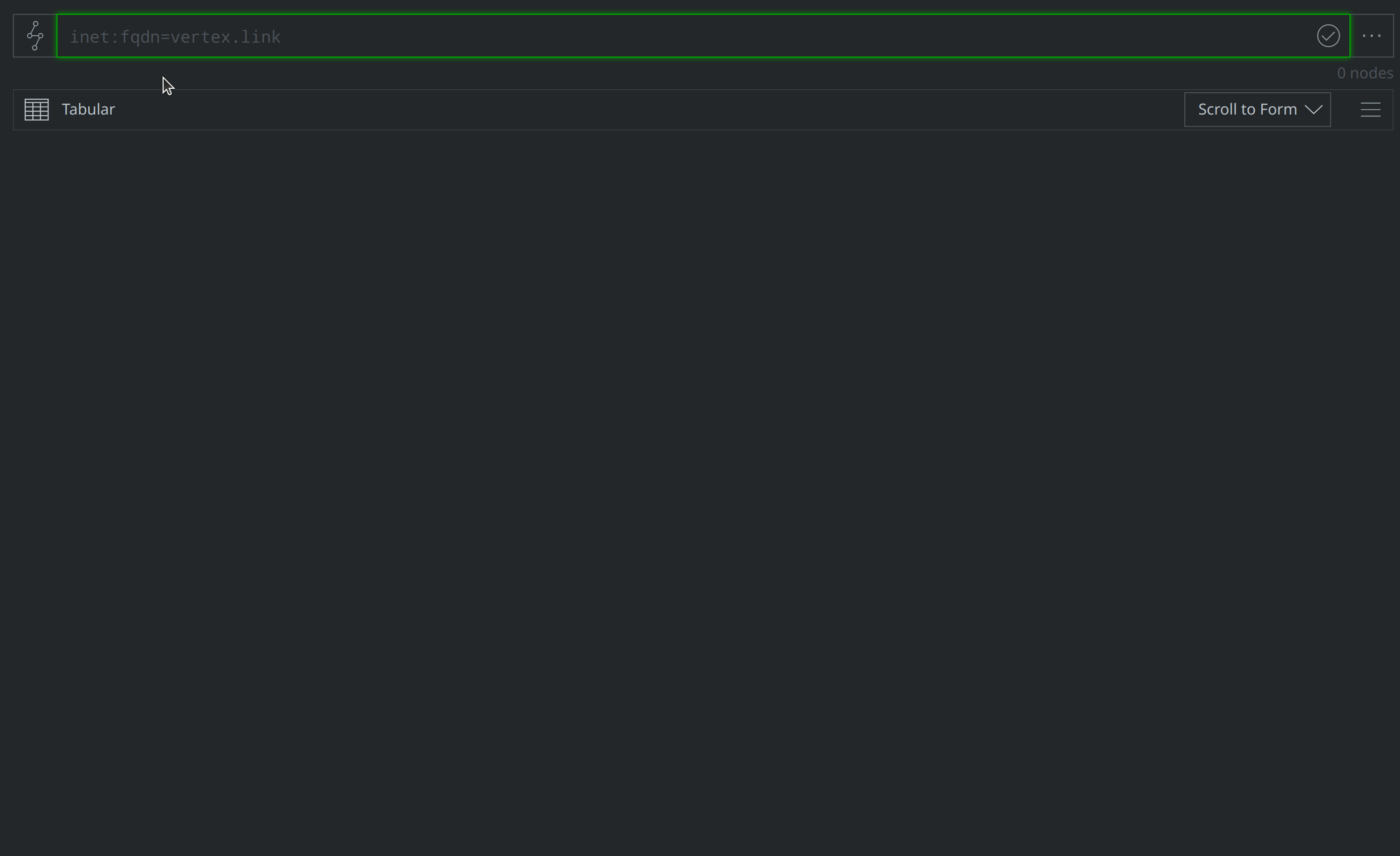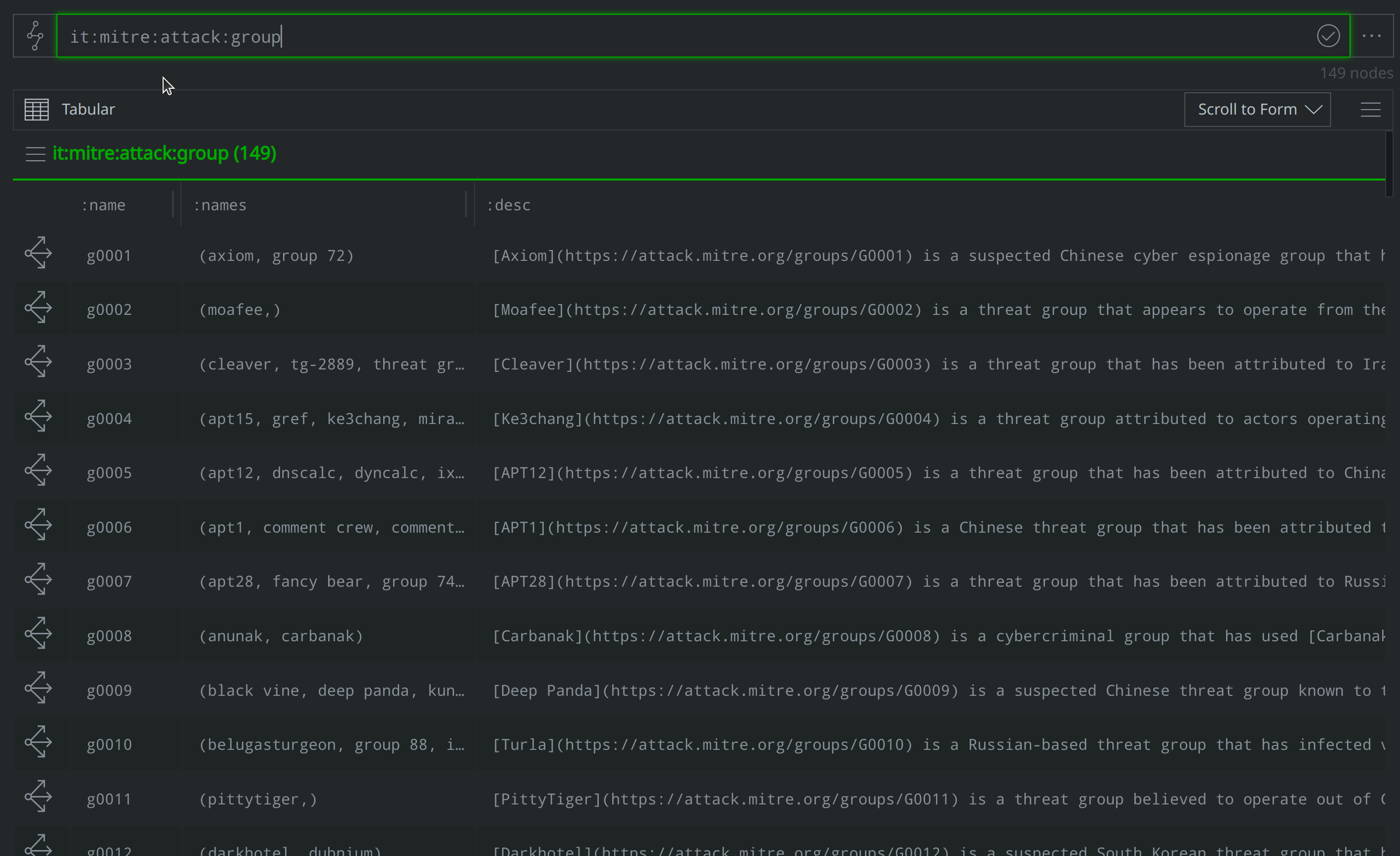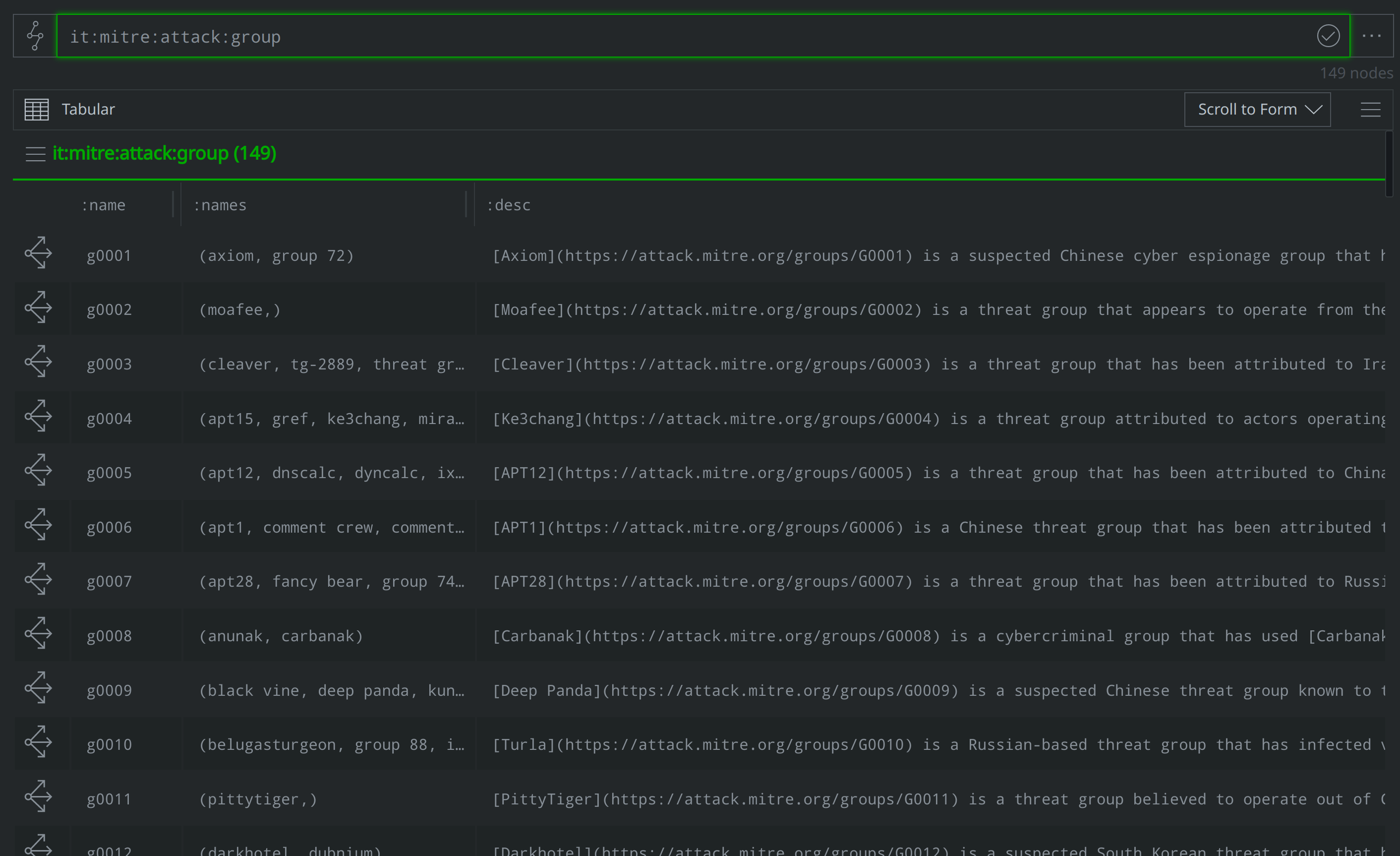
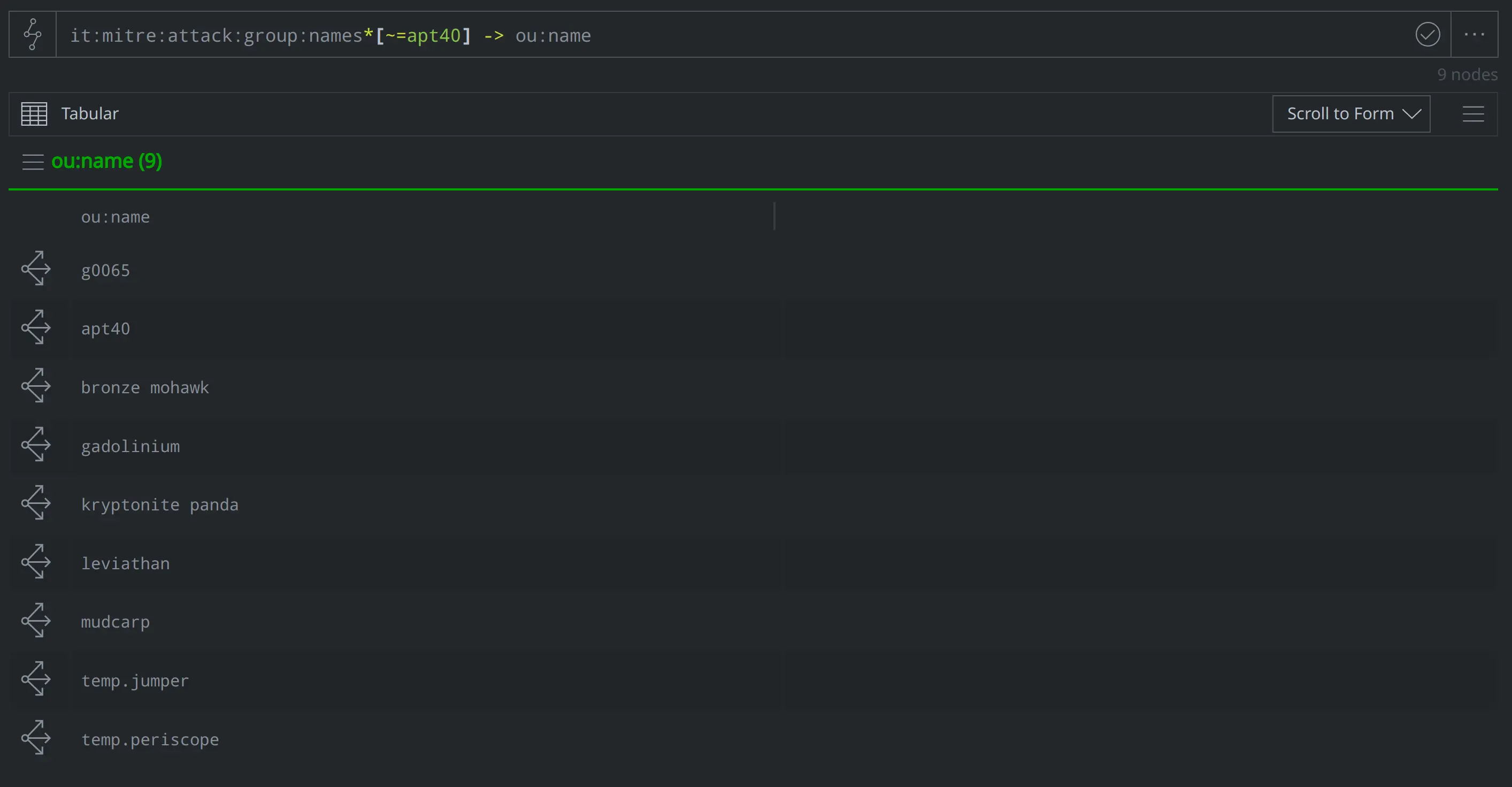
What other names does ATT&CK associate with APT40?
it:mitre:attack:group:names*[~=apt40] -> ou:name
What techniques does ATT&CK associate with the Sofacy group? (Answer: a lot....)
it:mitre:attack:group:names*[~=sofacy] -> it:mitre:attack:technique
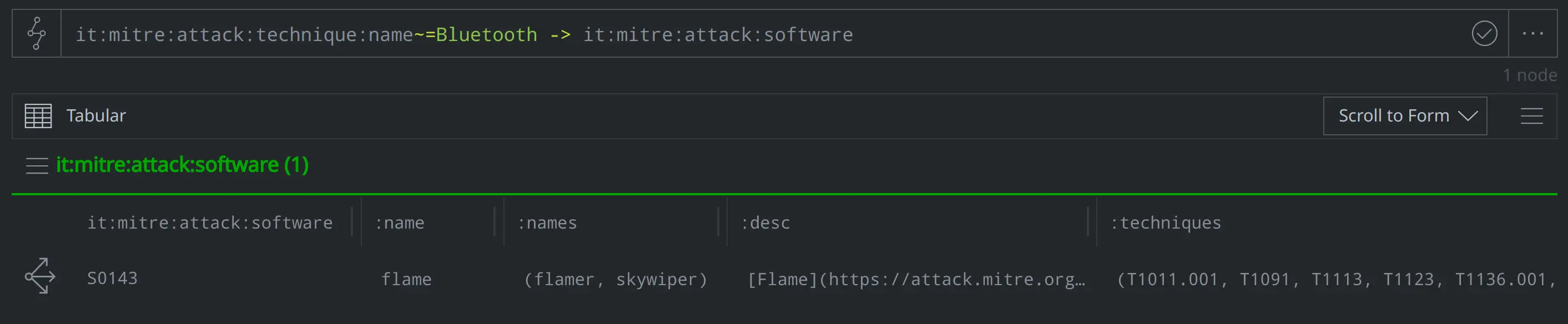
What software does ATT&CK associate with exfiltrating data over bluetooth?
it:mitre:attack:technique:name~=Bluetooth -> it:mitre:attack:software
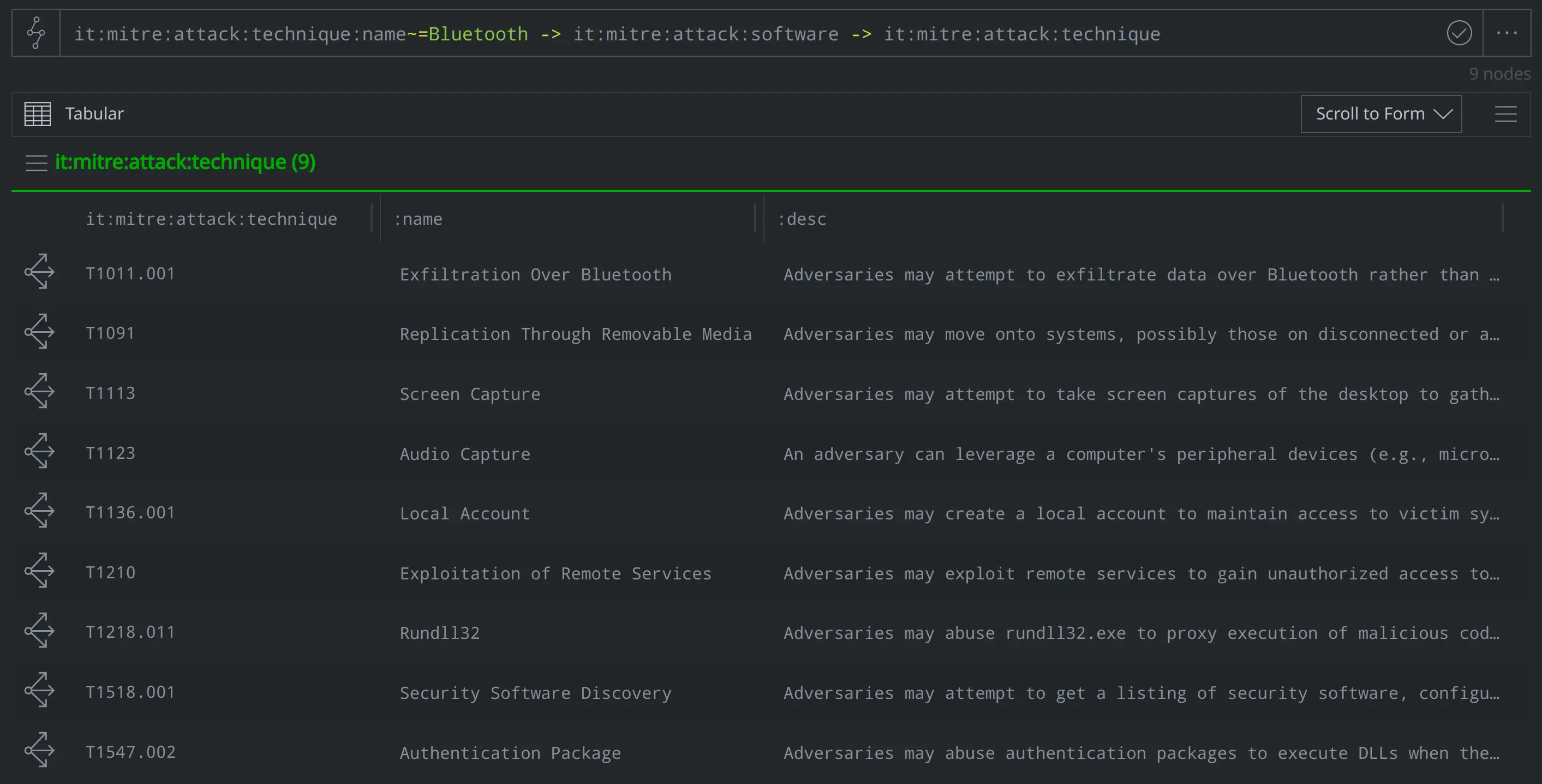
What other techniques does ATT&CK associate with that software?
it:mitre:attack:technique:name~=Bluetooth -> it:mitre:attack:software -> it:mitre:attack:technique
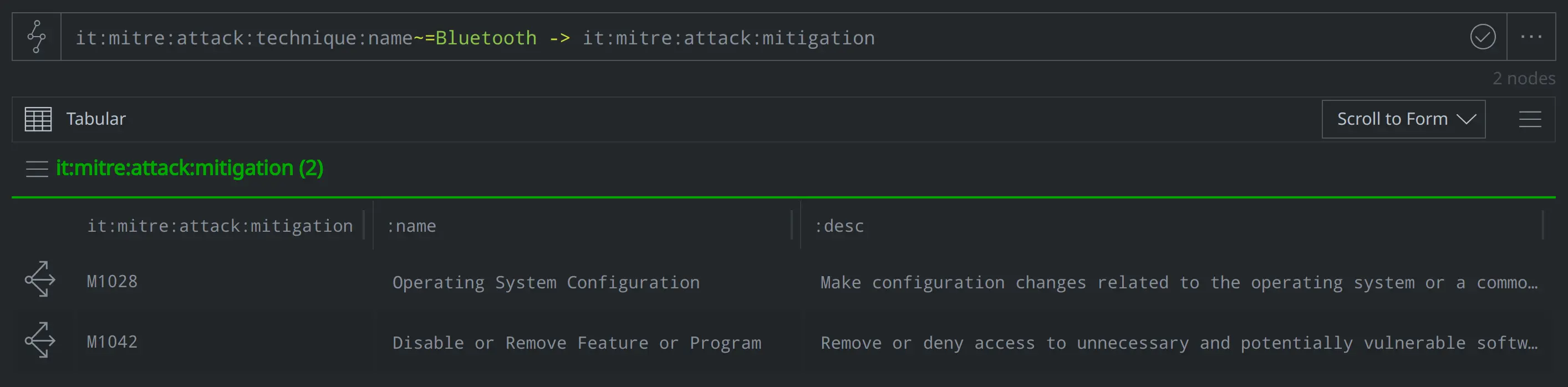
What mitigation strategies does ATT&CK recommend to address exfiltrating data over bluetooth?
it:mitre:attack:technique:name~=Bluetooth -> it:mitre:attack:mitigation
Pivoting from ATT&CK Elements to Query Other Nodes in Synapse
We can also create and pivot across light edges to answer questions about references to ATT&CK elements. Two other Synapse-Mitre-Attack commands, mitre.attack.scrape and mitre.attack.enrich, will identify references to ATT&CK elements in node properties and create light edges between those nodes and the ATT&CK elements that they reference. The mitre.attack.scrape command will scrape existing ATT&CK elements from any specified form and property, while mitre.attack.enrich will scrape ATT&CK elements from media:news:summary and inet:web:post:text properties. As analysts, we can use these commands to do things like map references from reports modeled as media:news nodes to an ATT&CK element noted in the :title or :summary properties, or map an it:app:yara:rule node (as an example) to an ATT&CK element contained in the node’s :text property, or any text we specify.
The Synapse-Mitre-Attack Power-Up also includes the mitre.attack.scrapefile command, which acts as a custom fileparser capable of parsing out ATT&CK strings from a file:bytes node and linking the modeled references back to the node. For Synapse Enterprise users, installing the Synapse-Mitre-Attack Power-Up will automatically add the ability to scrape ATT&CK references to the Spotlight Tool.
These commands give us the ability to ask questions like:
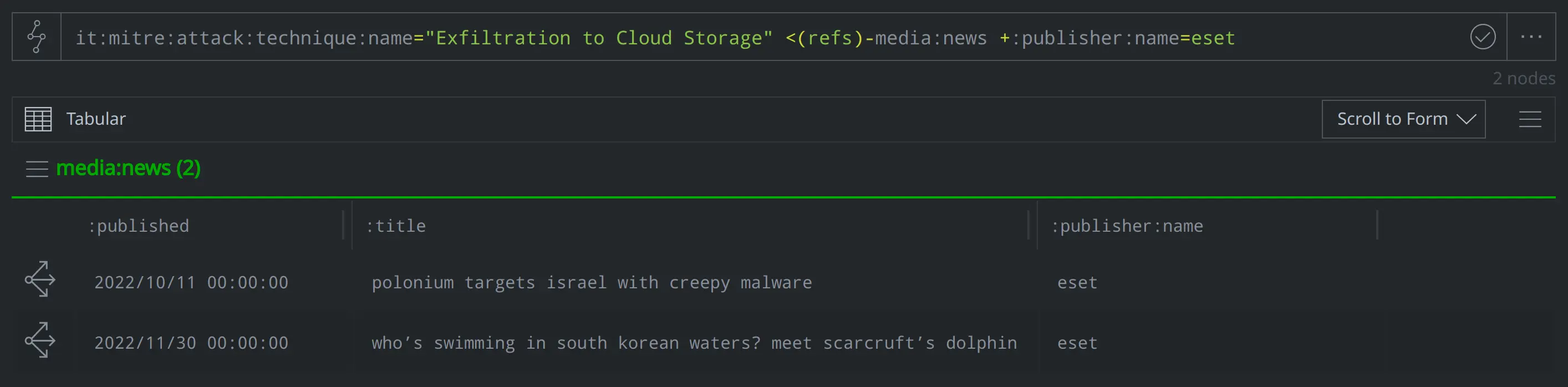
Have we modeled any reports from ESET mentioning activity that involves exfiltrating data to cloud storage?
it:mitre:attack:technique:name="Exfiltration to Cloud Storage" <(refs)-media:news +:publisher:name=eset
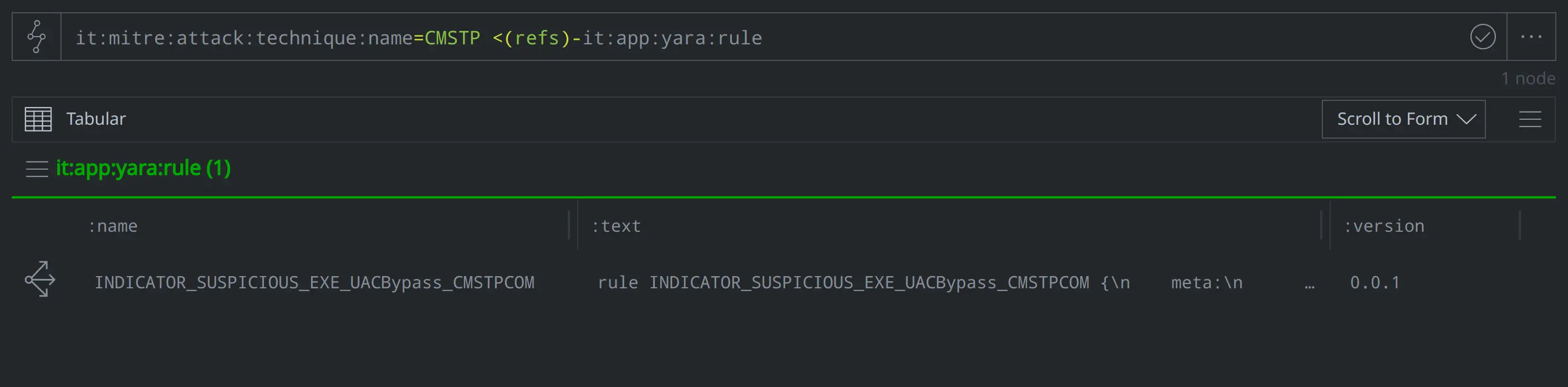
Have we modeled any YARA rules that reference abusing Microsoft Connection Manager Profile Installer (CMSTP.exe)?
it:mitre:attack:technique:name=CMSTP <(refs)-it:app:yara:rule
Translating ATT&CK Elements into Synapse's Risk Data Model
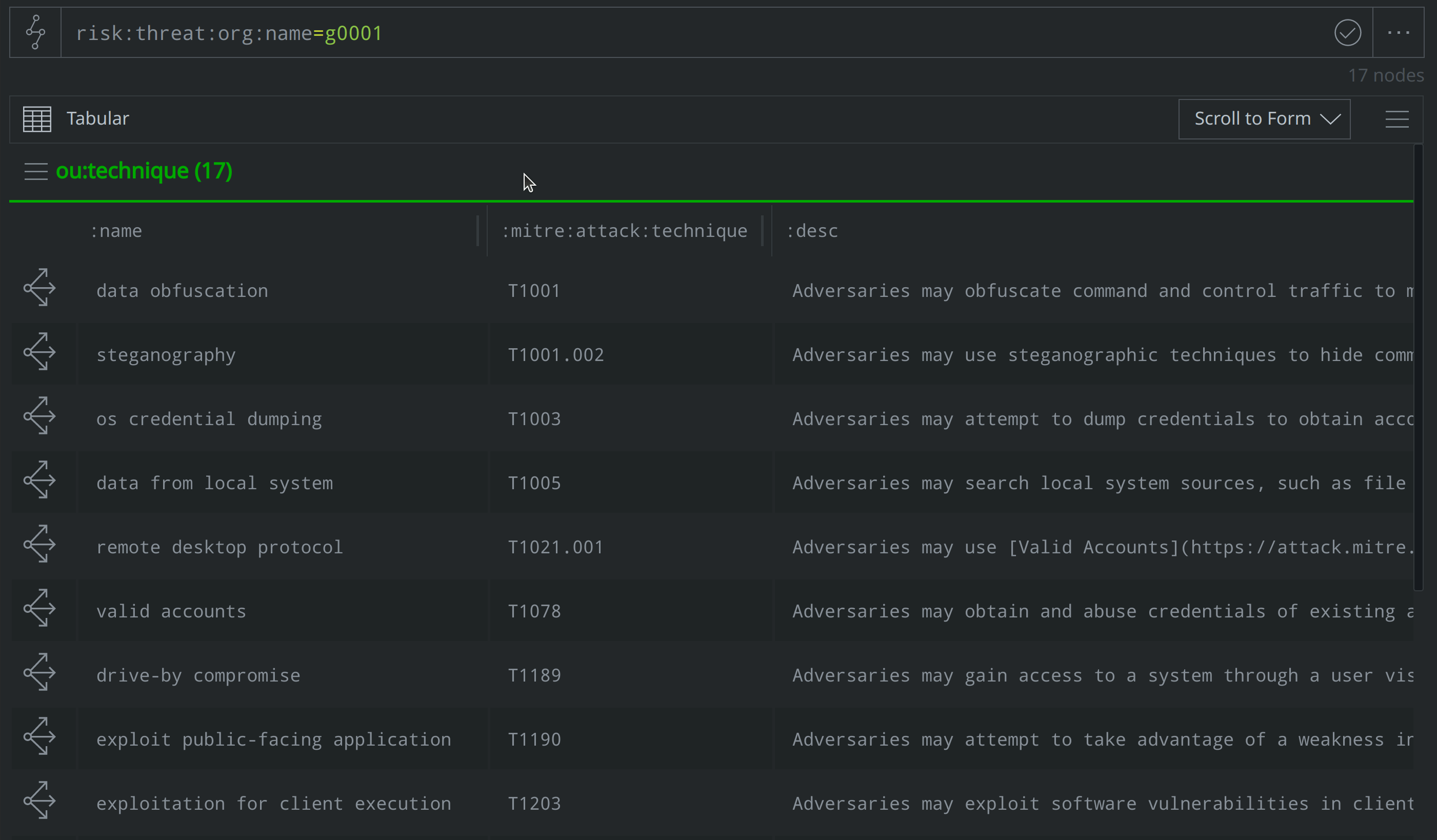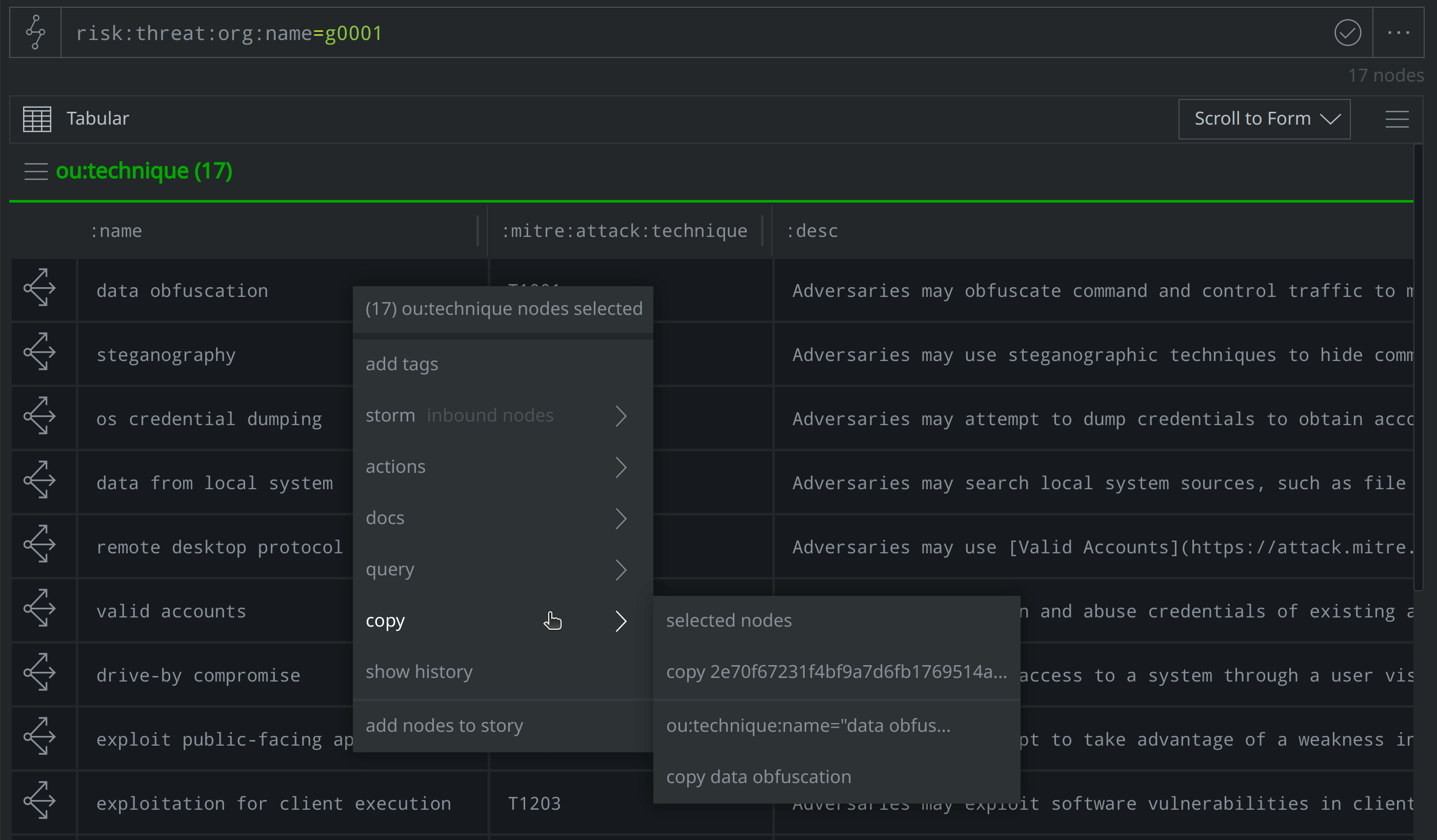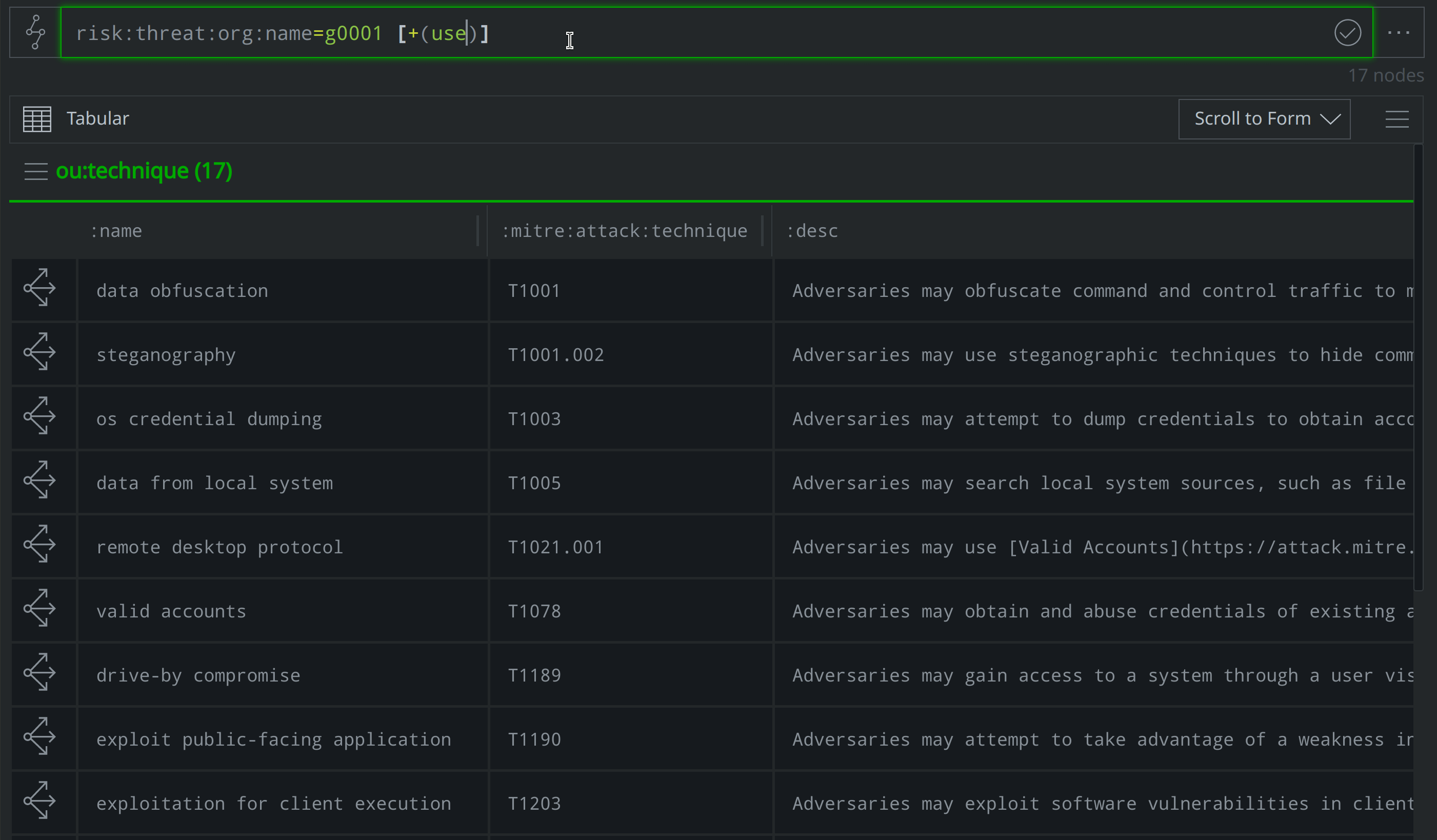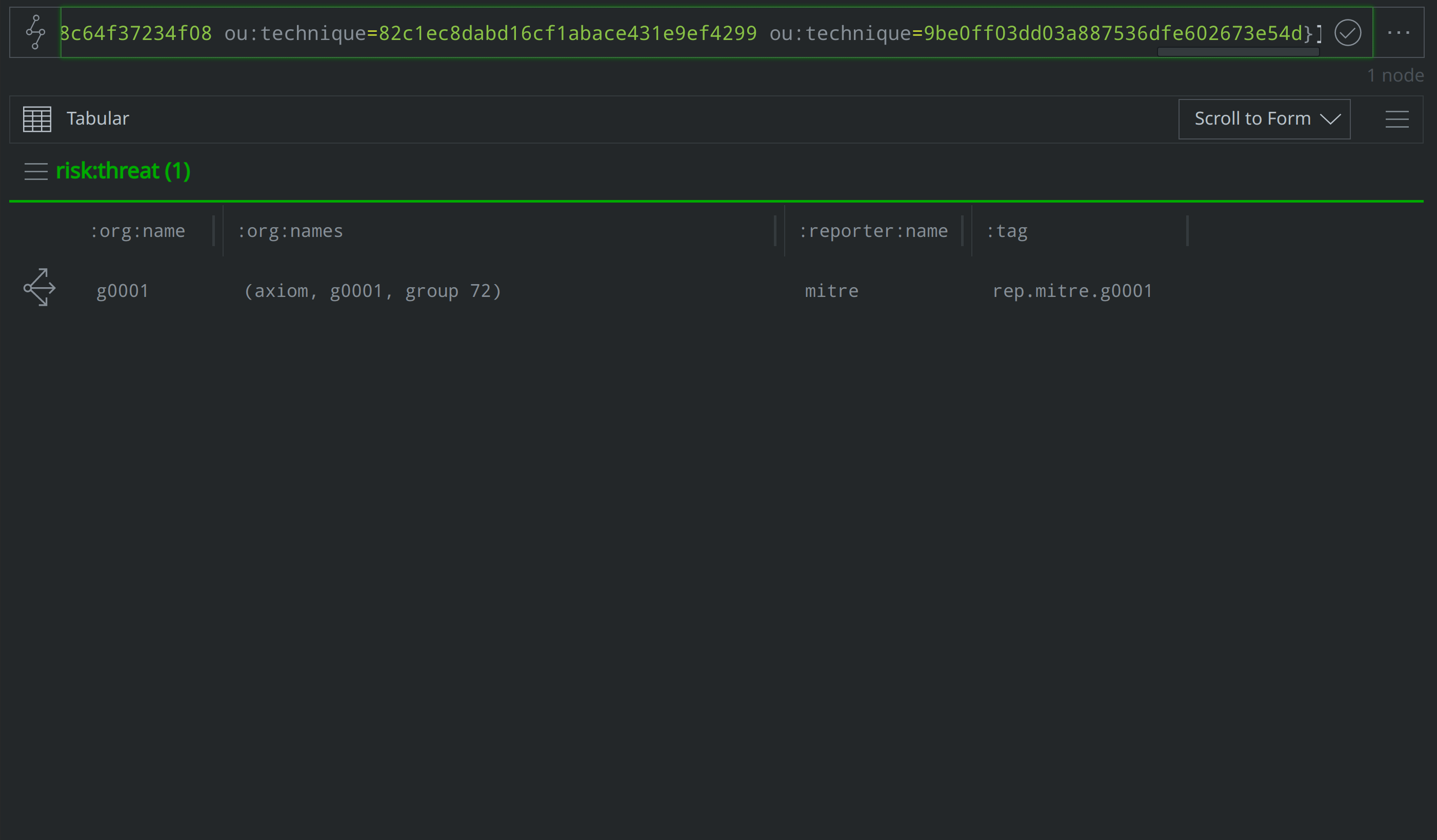
Analysts can use the Synapse-Mitre-Attack Power-Up’s mitre.attack.translate command to "translate" the ATT&CK-identified groups, software, and techniques into risk:threat, risk:tool:software, and ou:technique nodes. Below, we use the mitre.attack.translate command to translate five it:mitre:attack:group nodes into corresponding risk:threat nodes:
it:mitre:attack:group | limit 5 | mitre.attack.translate --yield
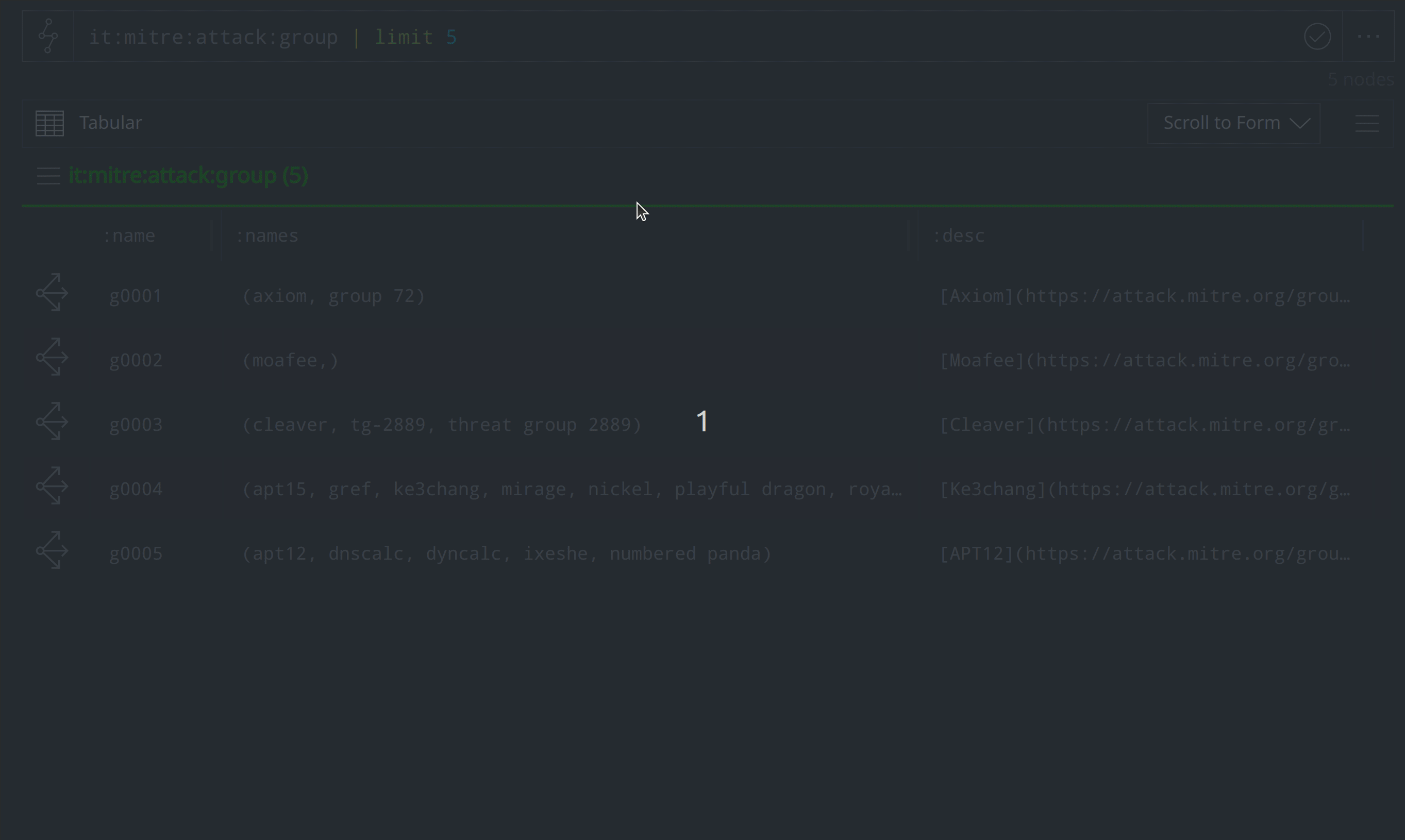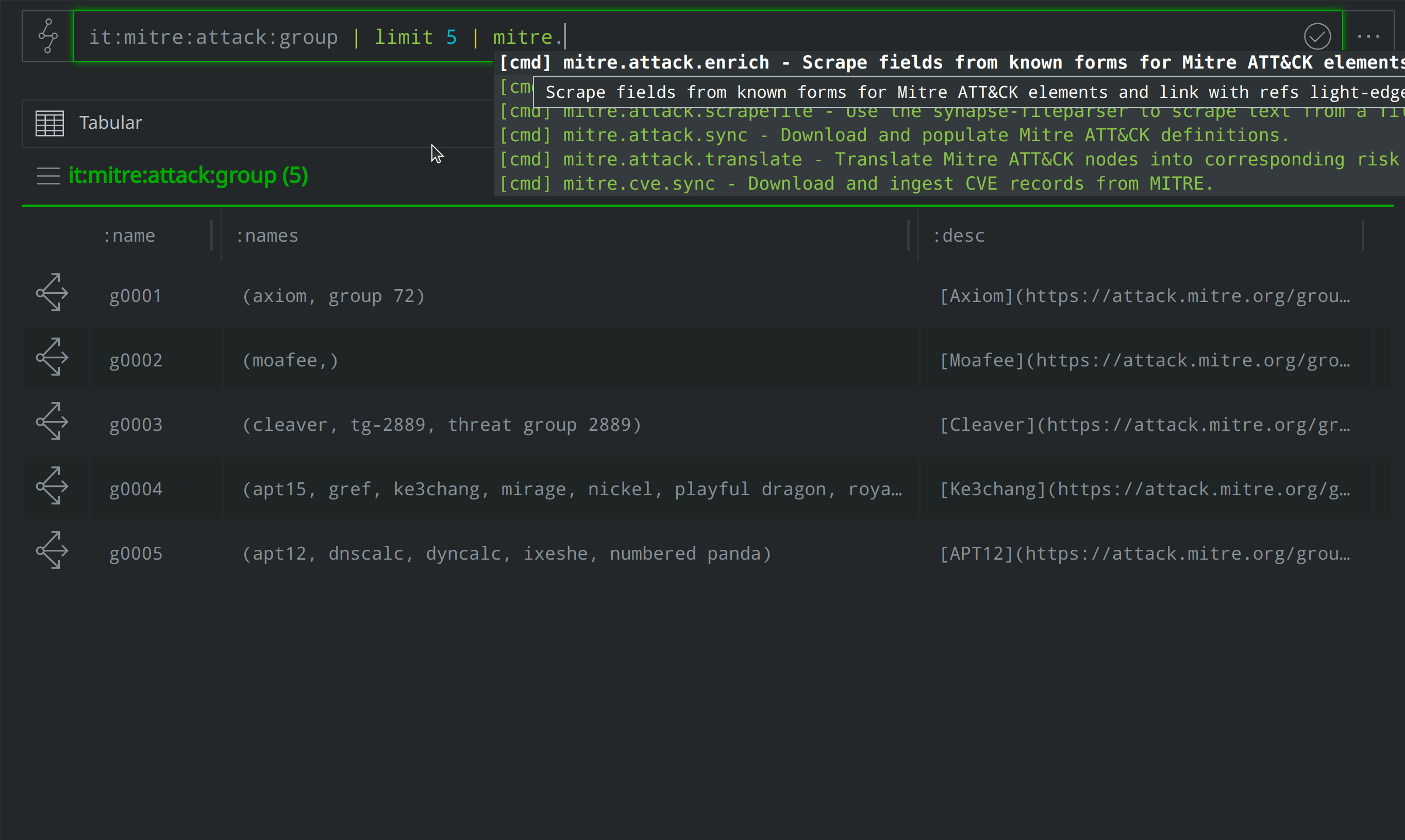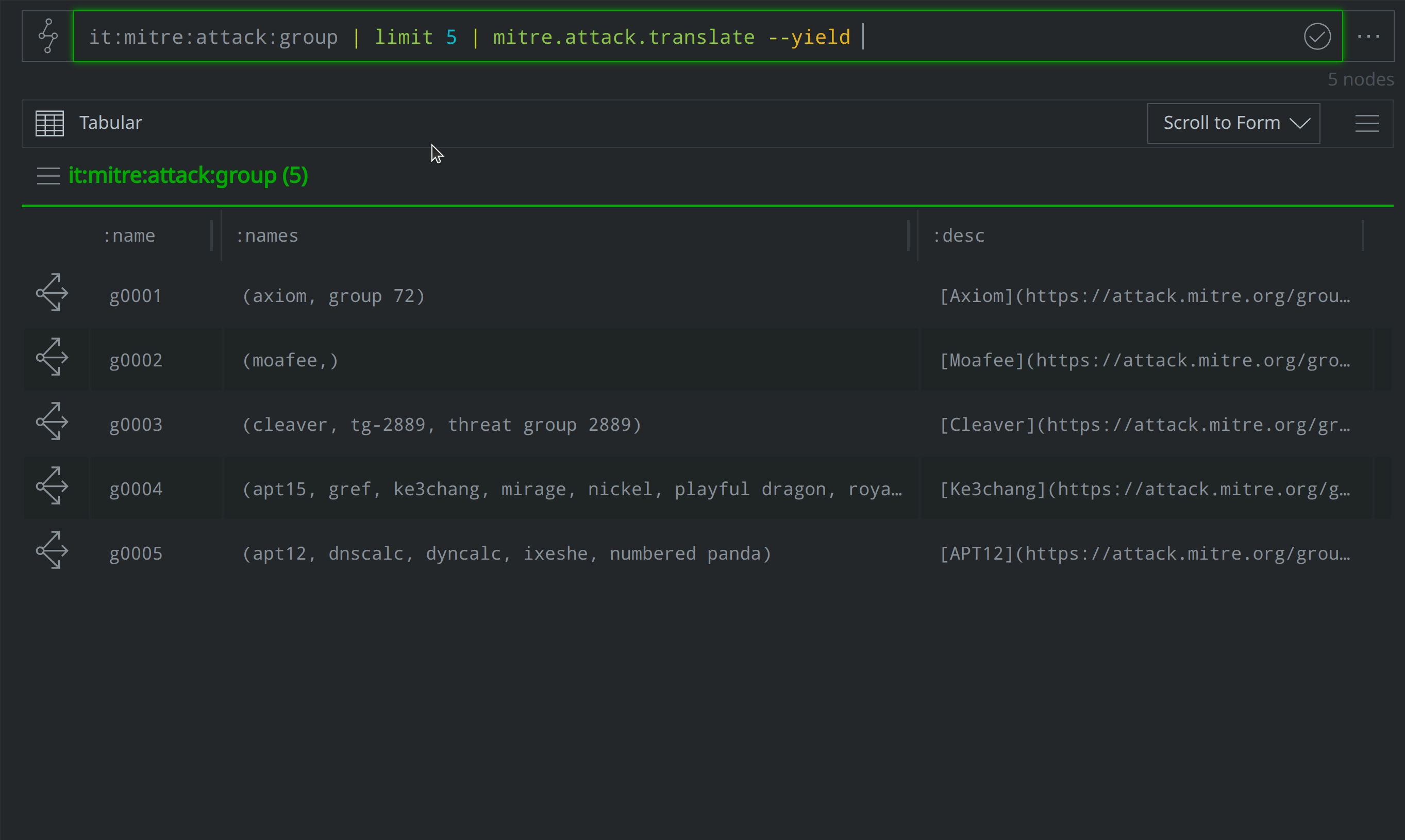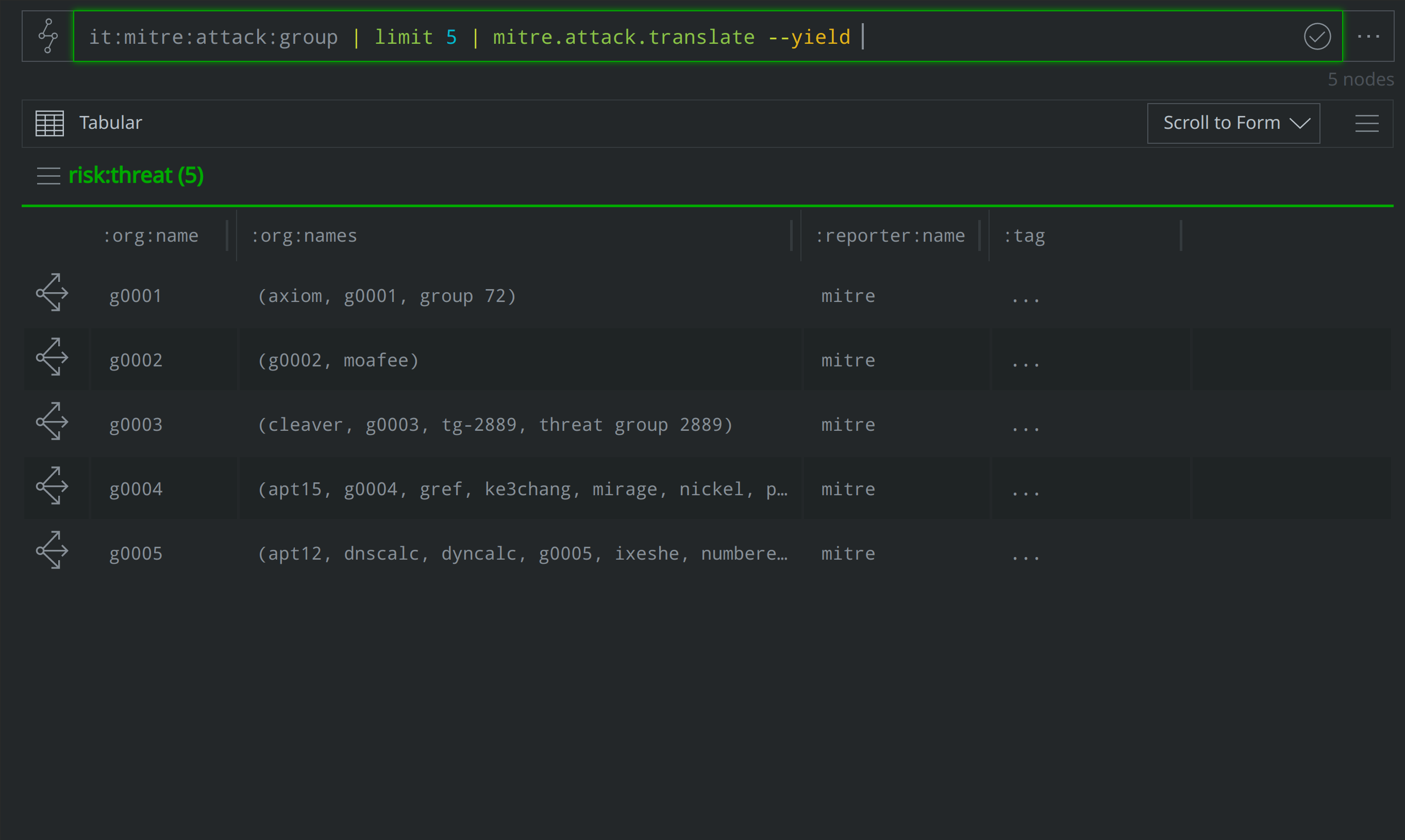
Translating the ATT&CK group, software, and technique elements integrates the ATT&CK elements into the risk:* and ou:* aspects of the Synapse data model. This lets us include ATT&CK elements in our results when we run queries to answer questions such as:
What threat clusters do we know of that correspond to the name "Lazarus"?
Note that we can use the Vertex Threat Intel Workflow for this query, as seen below:
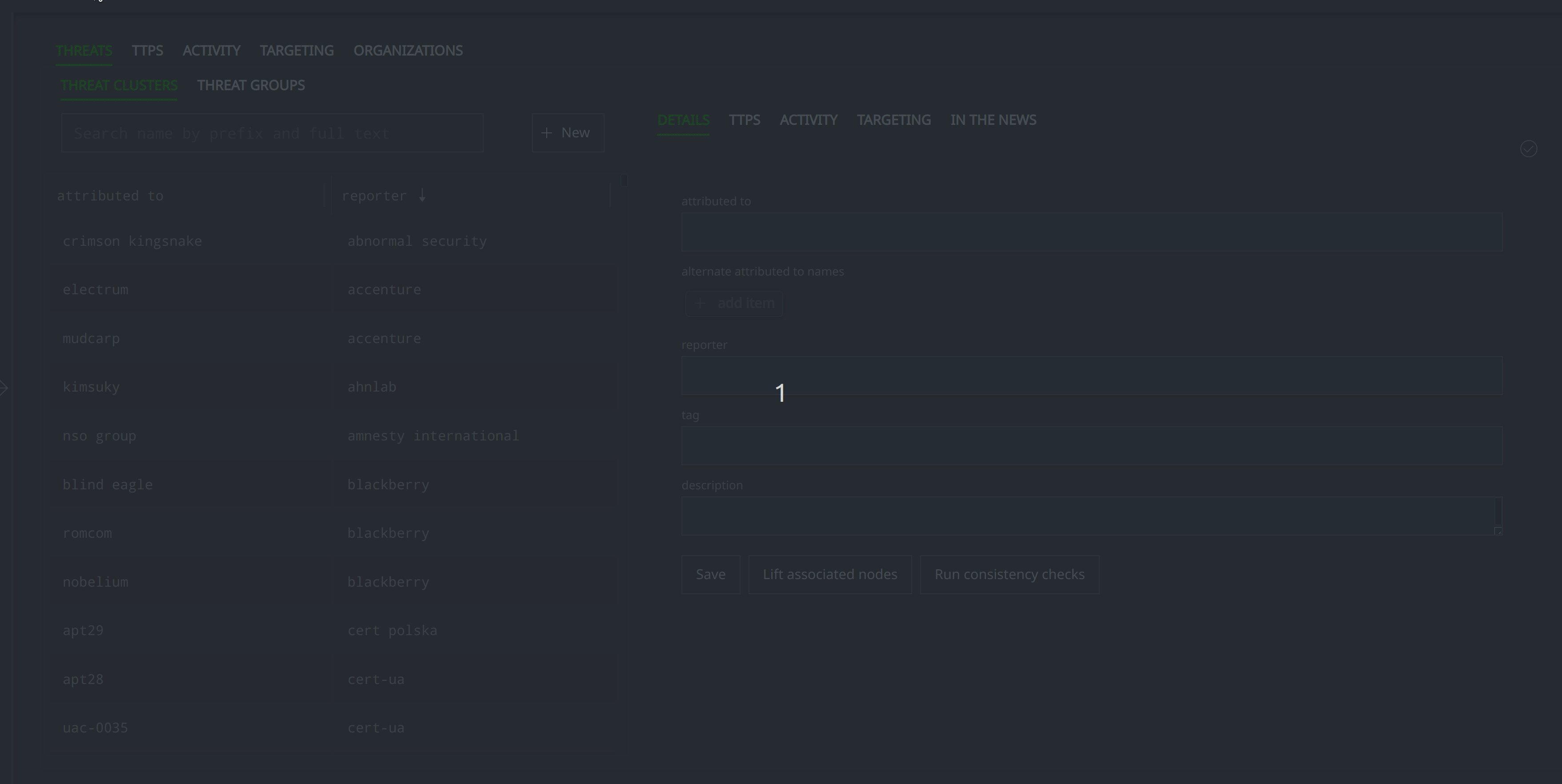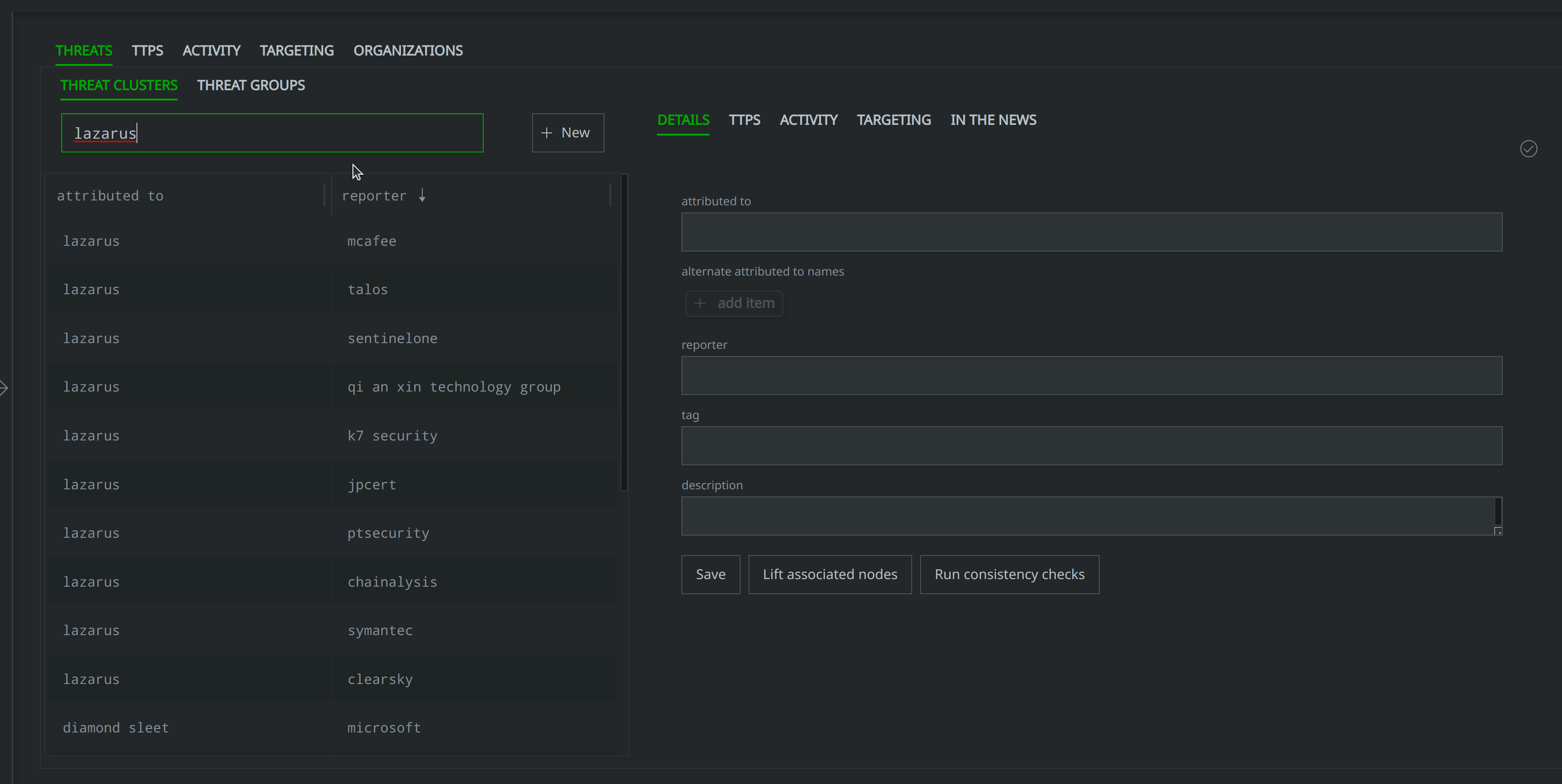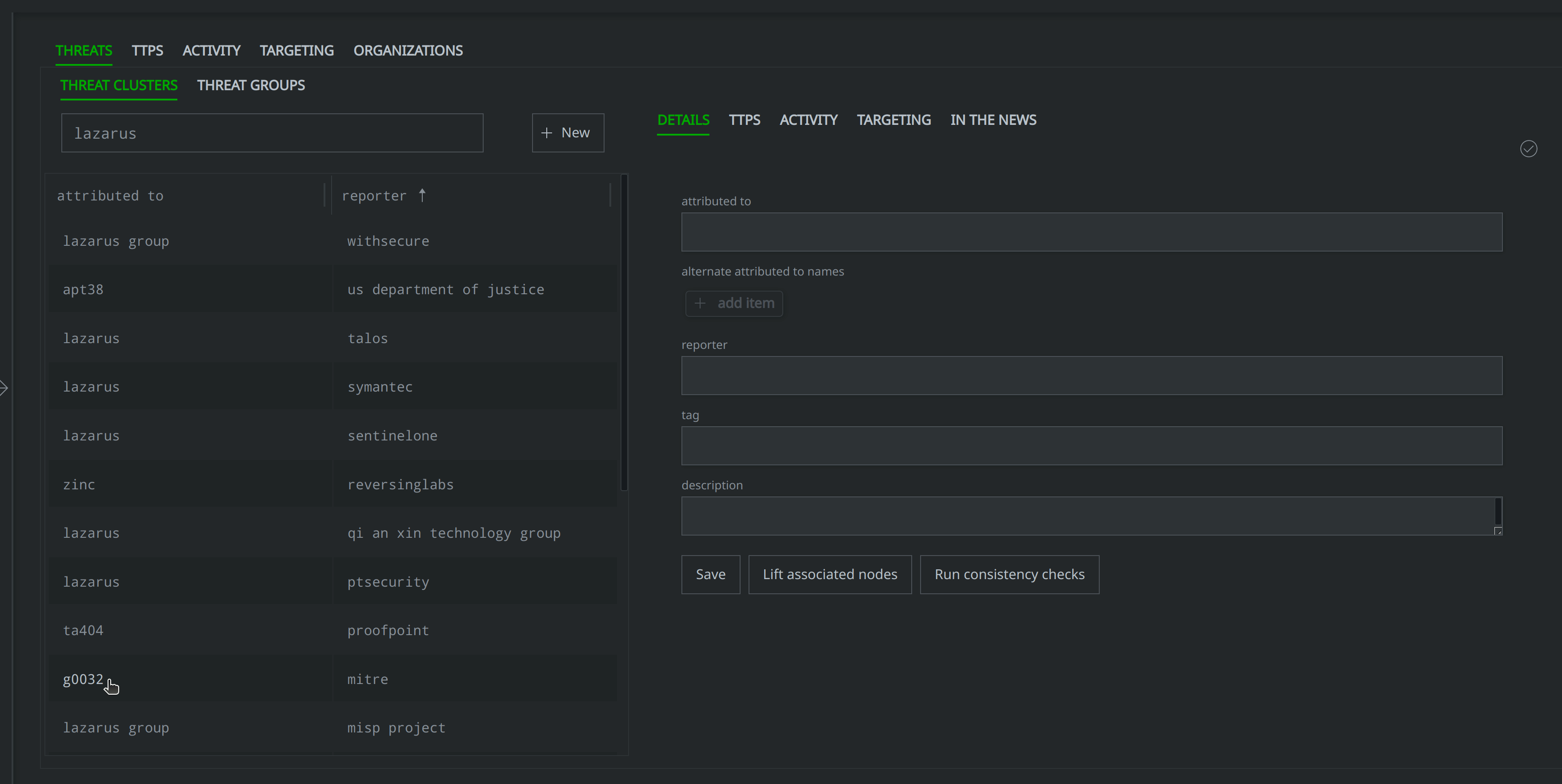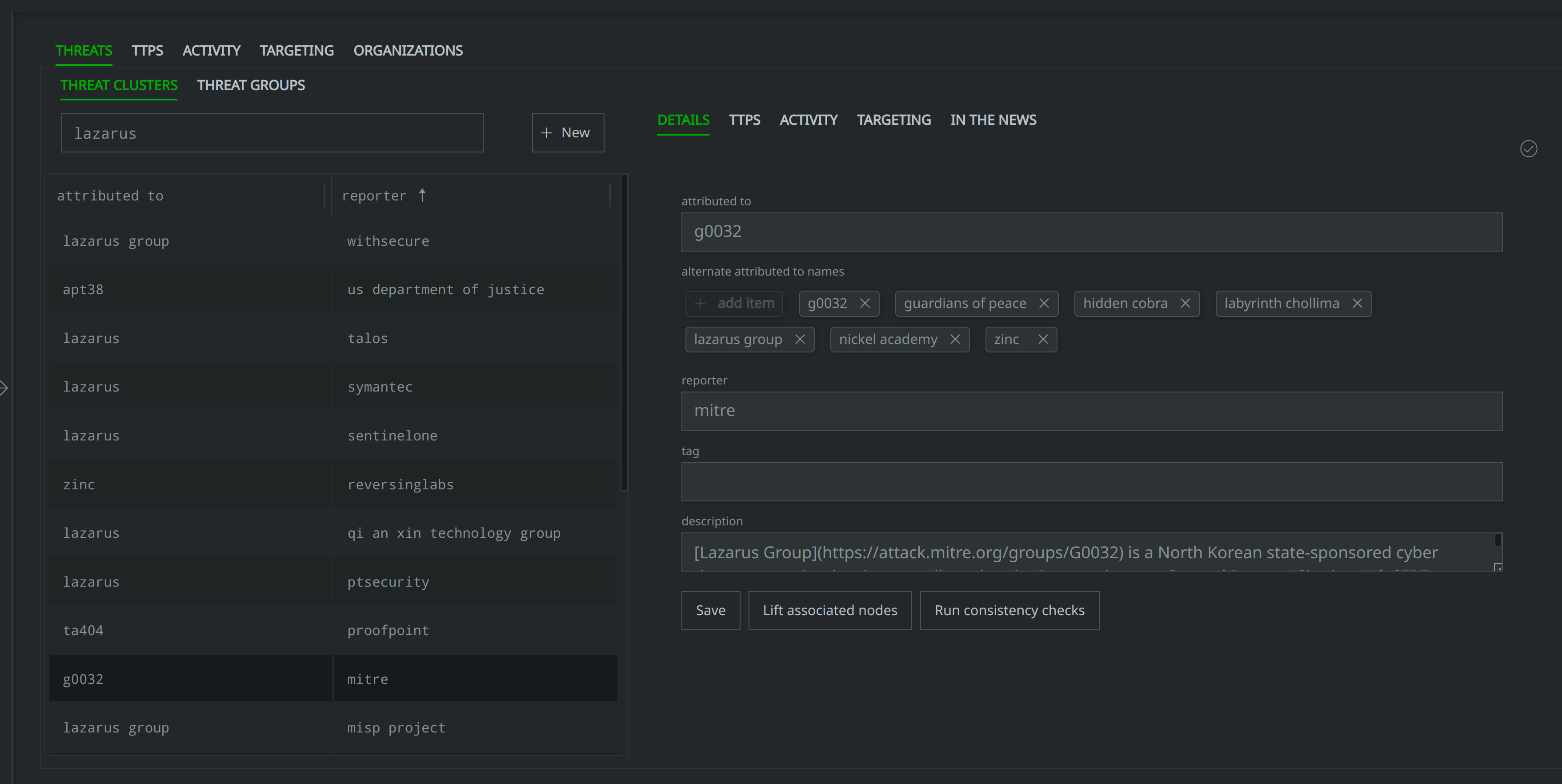
Ability to Query and Link to MITRE ATT&CK® Elements Opens the Door for More Granular Use of the Framework within Synapse
The ability to represent the MITRE ATT&CK® framework within Synapse allows analysts to query and ask questions of the Enterprise, ICS, and Mobile matrices and ATT&CK elements, as well as map references and pivot from ATT&CK elements to query other data within their Synapse instance. This means that you can view the matrix without leaving your Synapse instance, as well as ask questions about how ATT&CK elements pertain to other data that you’ve modeled. Representing ATT&CK elements within Synapse gives you the ability to integrate the framework into your analysis and workflow, allowing for more granular use of the framework.
To learn more about Synapse and its different capabilities and use cases, join our Slack community, check out our videos on YouTube, and follow us on Twitter.
