From Group to Individual: Modeling InformNapalm’s Article on Sergey Morgachev of APT28
by savage | 2023-06-28
In April 2023, InformNapalm profiled Lieutenant Colonel Sergey Alexandrovich Morgachev, an officer in Unit 26165 of the Main Intelligence Directorate of the General Staff of the Russian Army (GRU), which multiple sources have assessed to be responsible for cyber activity associated with APT28. The report was based on information provided by individuals calling themselves the Cyber Resistance, who had gained access to Morgachev’s email and various other online accounts, including a social media profile, e-commerce account, and an account with a Russian government service portal. Capturing this information within Synapse not only allows us to ask and answer questions about this individual, but also understand how they connect to other previously modeled data such as threat clusters and organizations.
Who is Sergey Alexandrovich Morgachev?
Prior to InformNapalm’s report, publicly available information about Morgachev was primarily limited to that included in the US Department of Justice's 2018 indictment of Morgachev and eleven of his compatriots for, among other things, conspiracy to commit an offense against the United States through their efforts to interfere with the 2016 presidential election. The indictment noted that Morgachev was a Lieutenant Colonel in the Russian military and supervised a team within Unit 26165 of the GRU that was responsible for developing and managing malware used in operations.
InformNapalm’s publication of Morgachev’s emails and personal documents provides access to much more granular information about Morgachev, including that gleaned from his:
Passport
Curriculum Vitae
Driver’s license
Security clearance forms
Email correspondence
Social media and online accounts
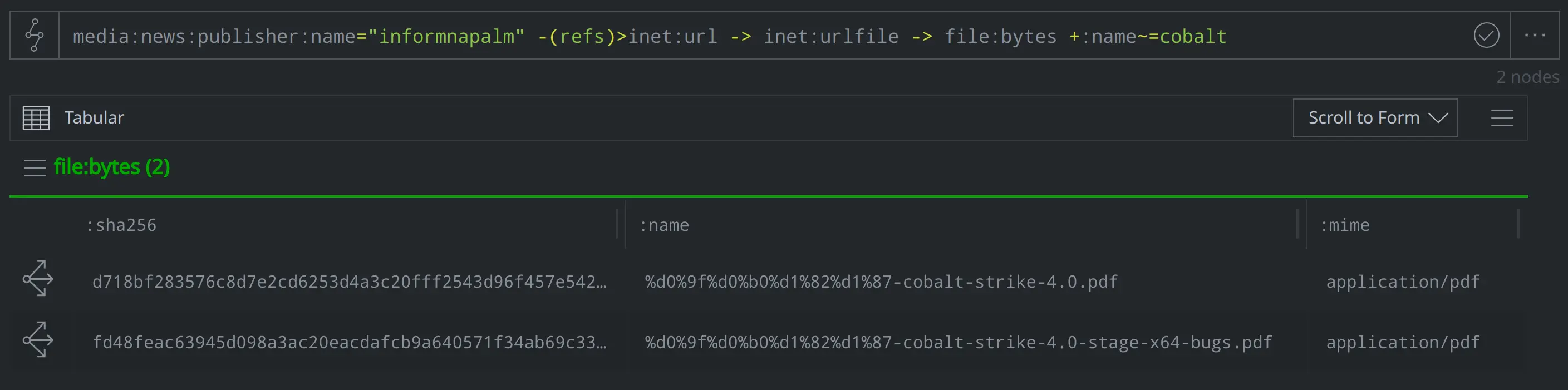
Notes on Cobalt Strike patches
Capturing this information in Synapse allows us to answer questions such as:
What contact information did InformNapalm release for Morgachev (note that this would include instances of contact data found on his passport, license, documented places of employment, and other data with records of address)?
media:news:publisher:name="informnapalm" -(refs)> ps:contact +:name^=serg
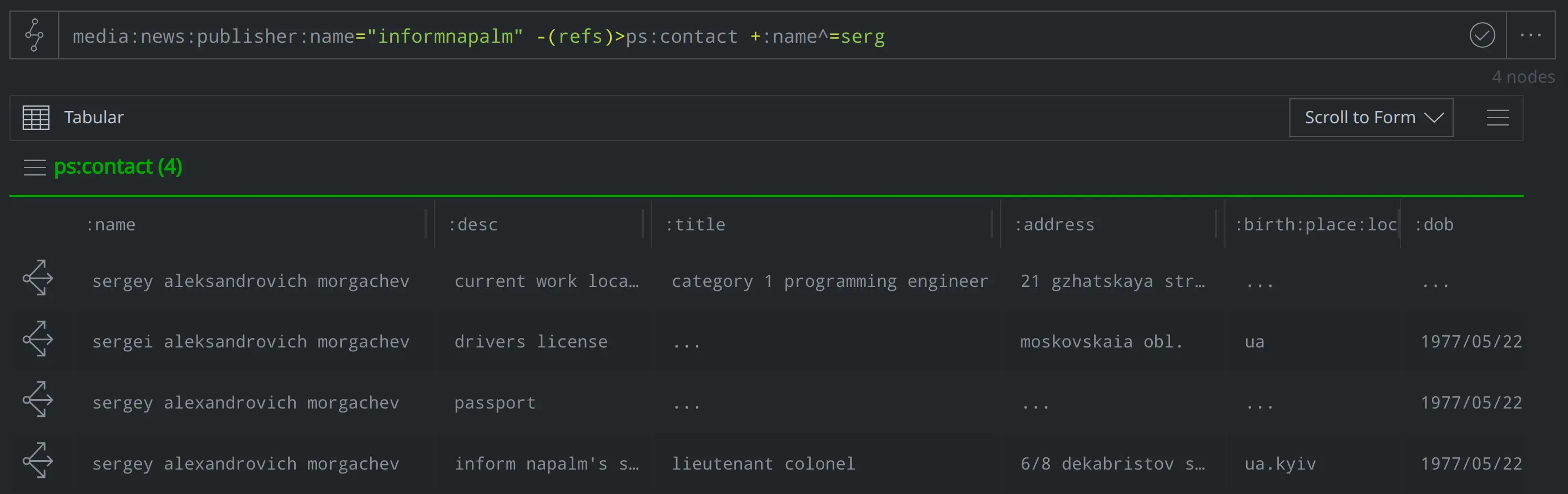
What contact information did InformNapalm include for his wife?
media:news:publisher:name="informnapalm" -(refs)> ps:contact +:desc~=wife
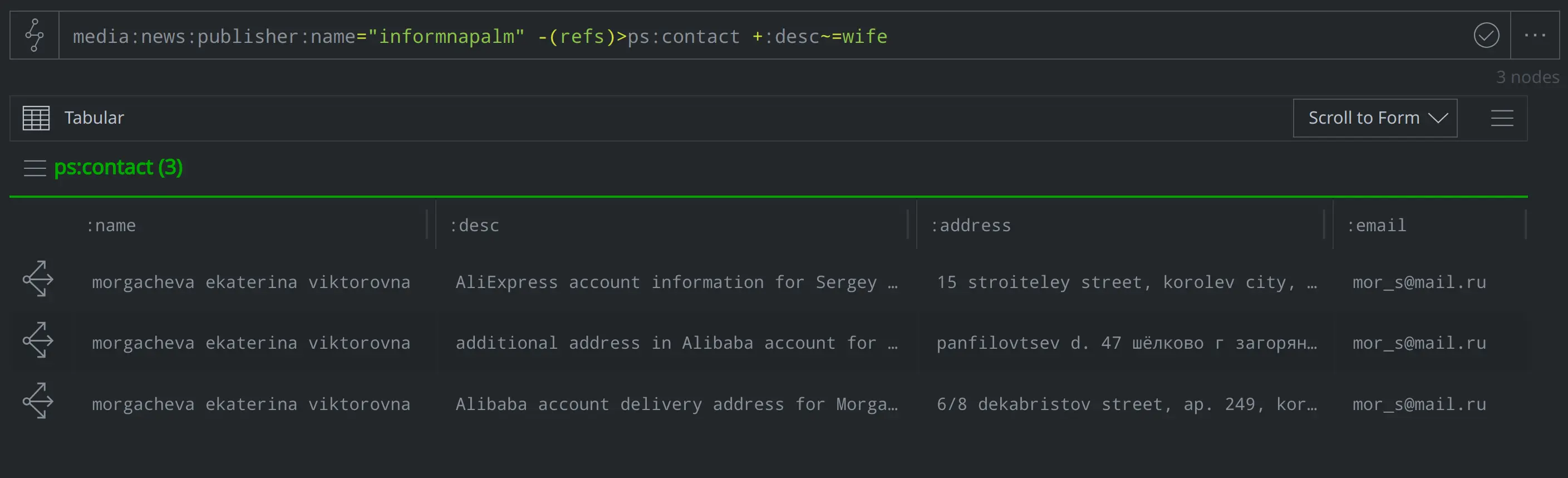
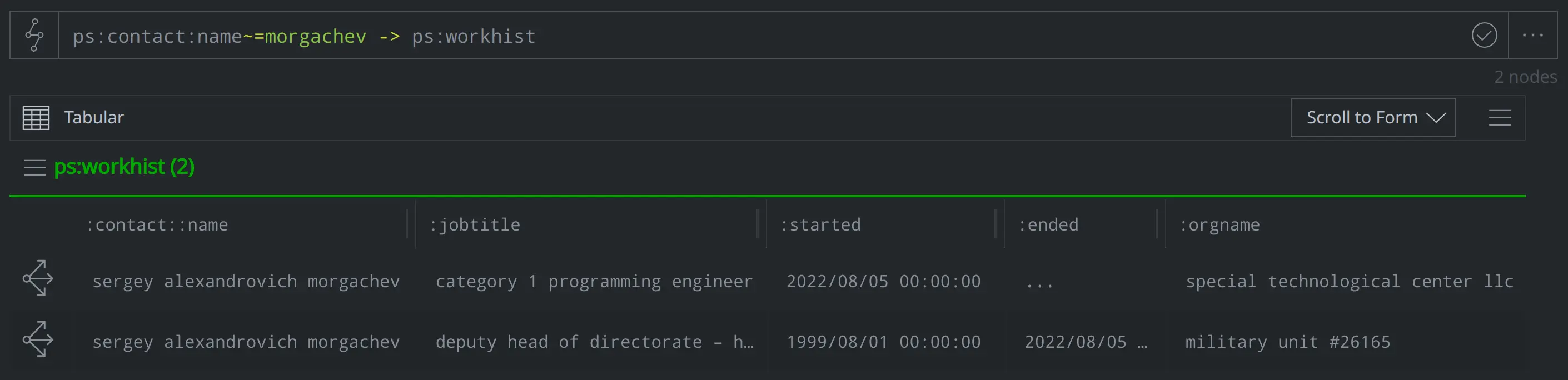
Where does Morgachev work? What jobs has he held previously?
ps:contact:name~=morgachev -> ps:workhist
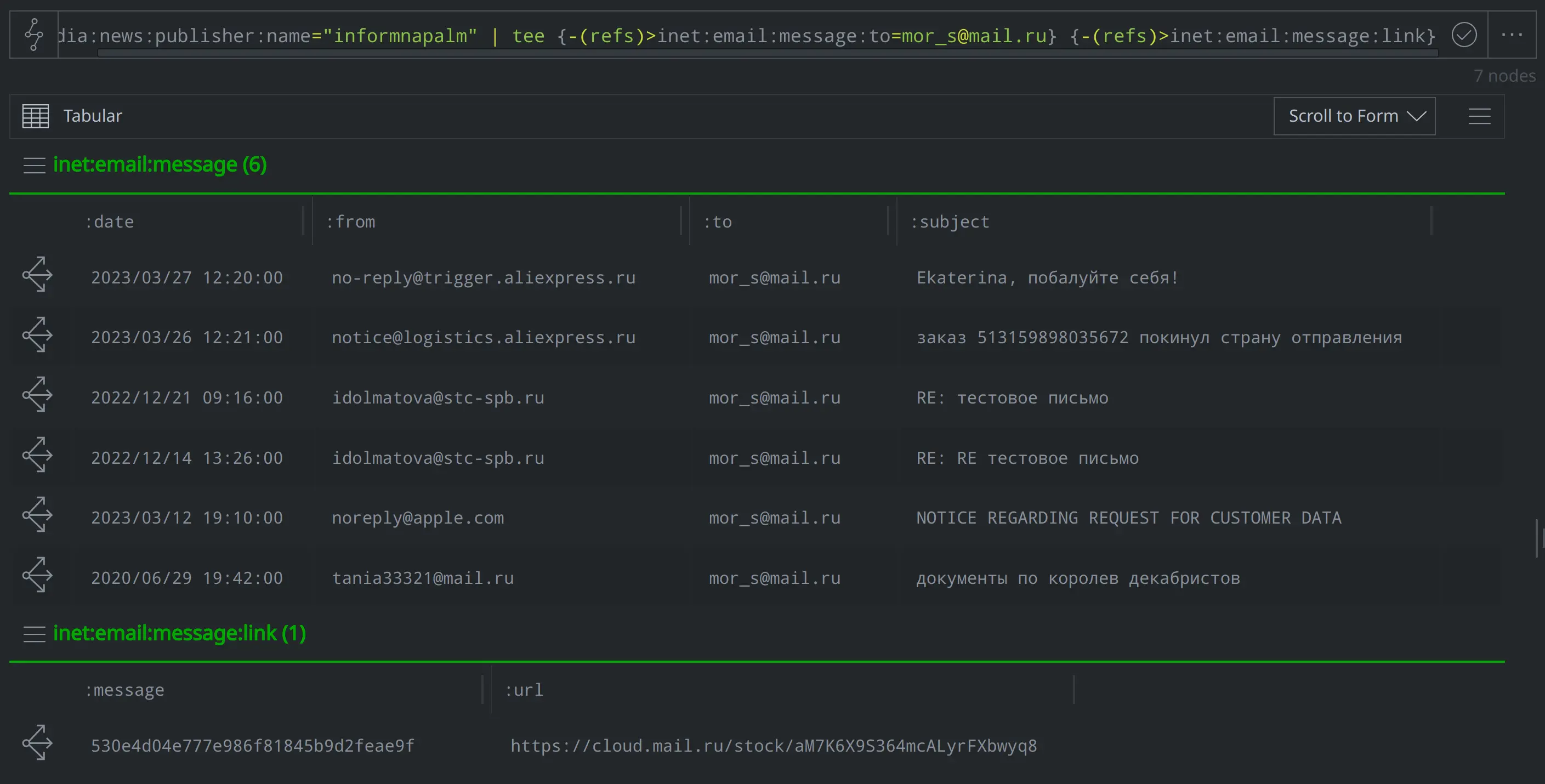
Which of Morgachev's email correspondence did InformNapalm include in their article? Did any contain an embedded URL?
media:news:publisher:name="informnapalm" | tee {-(refs)> inet:email:message:to=mor_s@mail.ru} {-(refs)> inet:email:message:link}
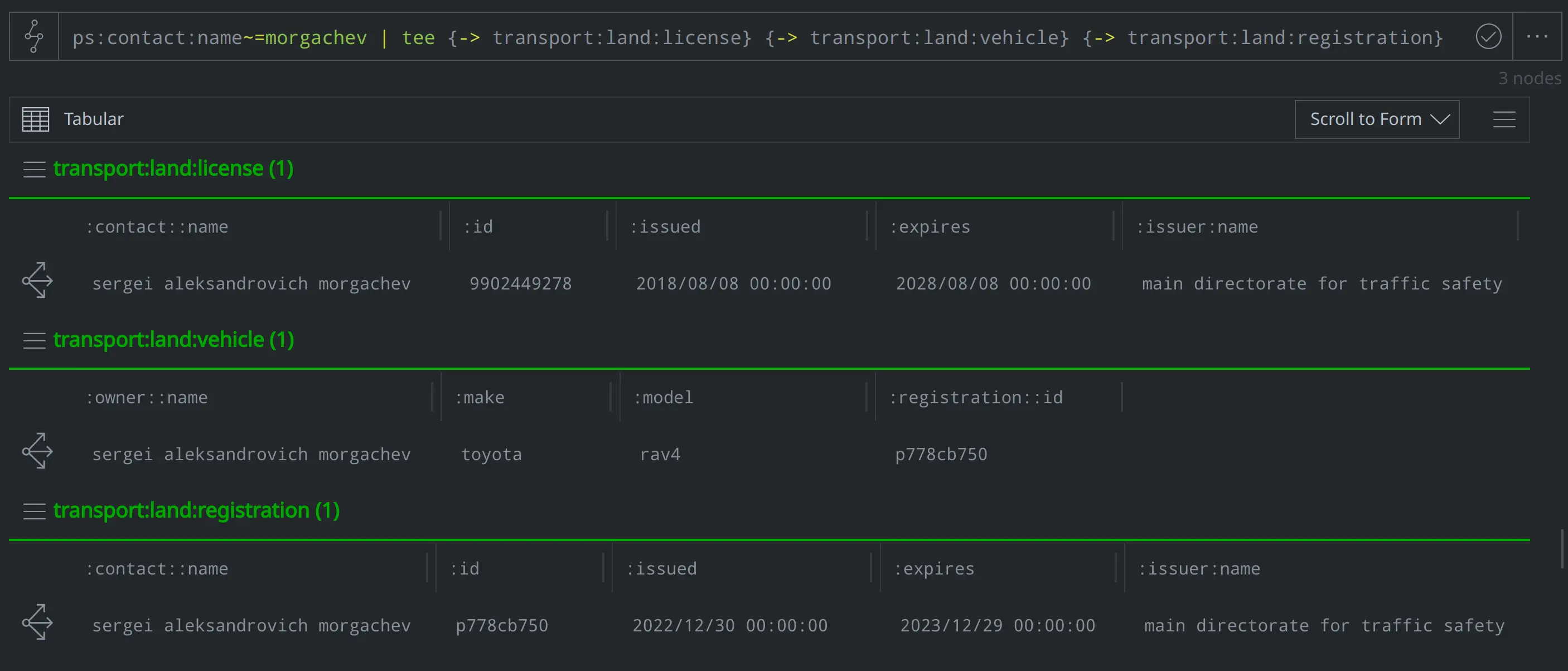
Does Morgachev have a driver's license? Does he have a car, and if so, what do we know about its registration?
ps:contact:name~=morgachev | tee {-> transport: land:license} {-> transport:land:vehicle} {-> transport:land:registration}
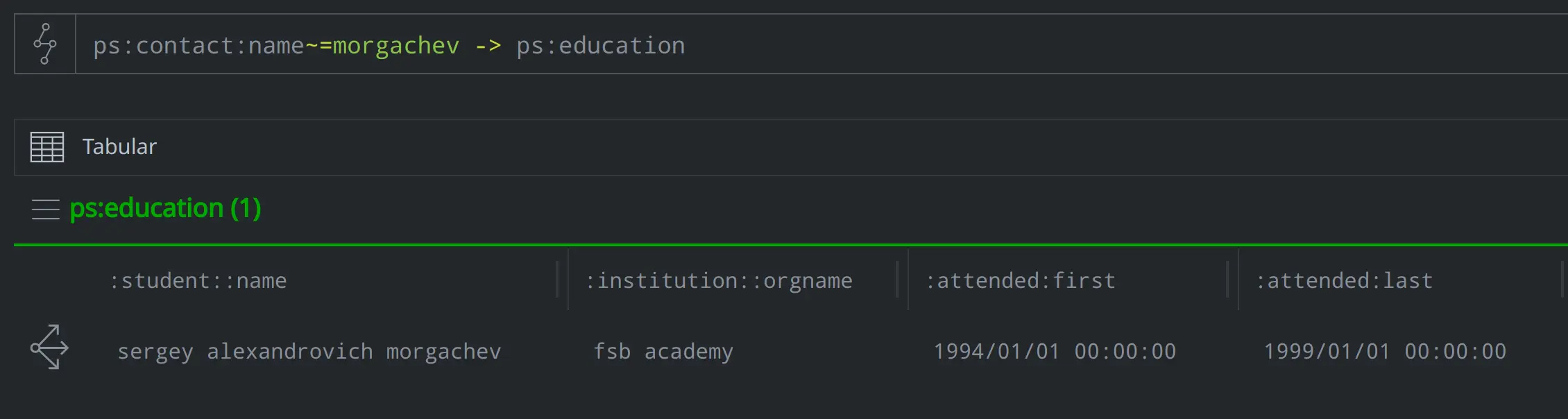
Where did Morgachev go to school and during what timeframe?
ps:contact:name~=morgachev -> ps:education
The Bigger Picture
Modeling data from InformNapalm’s report enables us to answer specific questions about Morgachev, while other, previously captured information from indictments and other sources helps to reveal additional context and allow analysts to see the bigger picture. Here are some examples of additional questions we might ask:
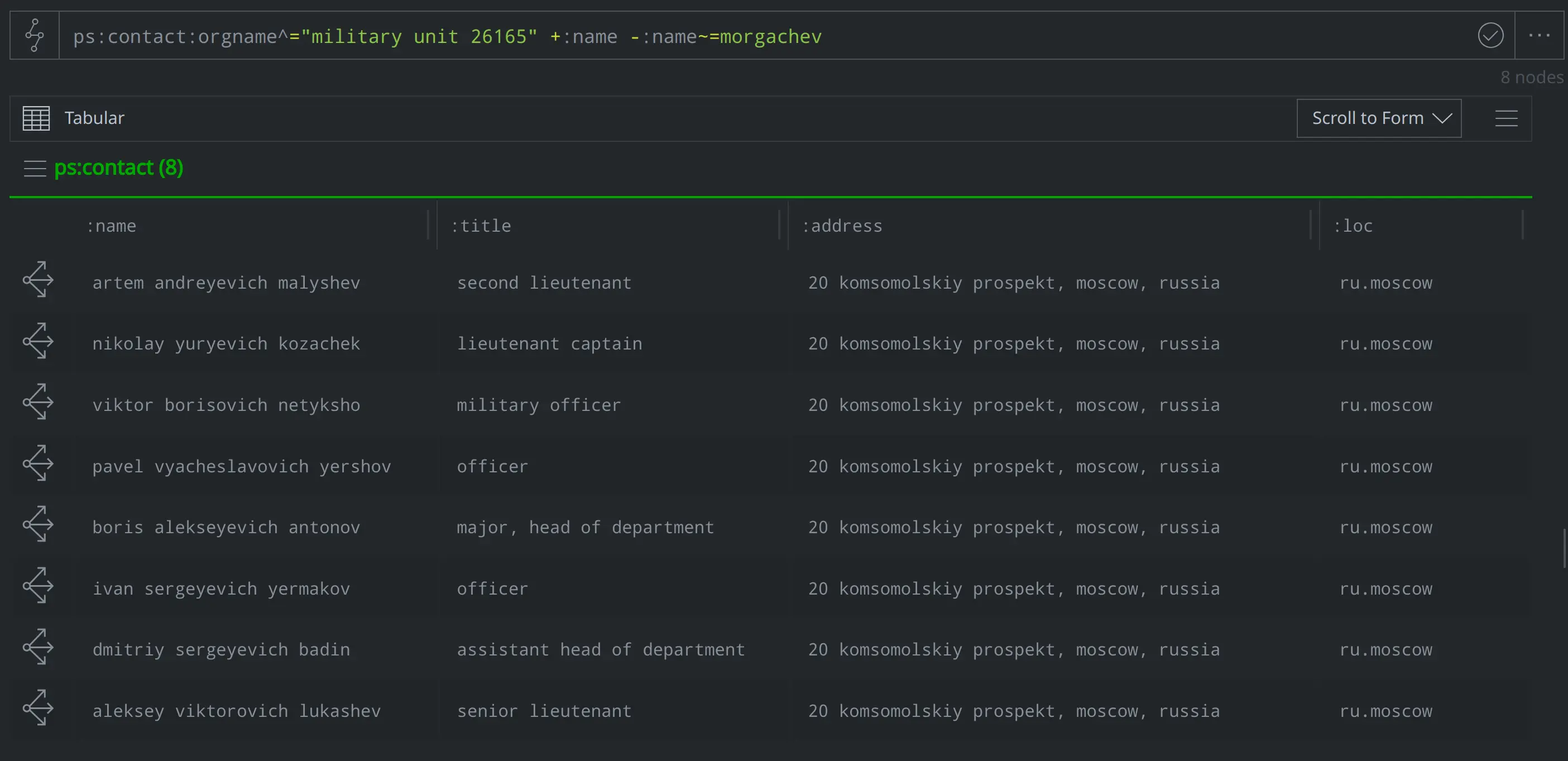
InformNapalm notes that Morgachev worked with GRU Unit 26165 - what other individuals do we know of who also worked in that same unit?
ps:contact:orgname^="military unit 26165" +:name -:name~=morgachev
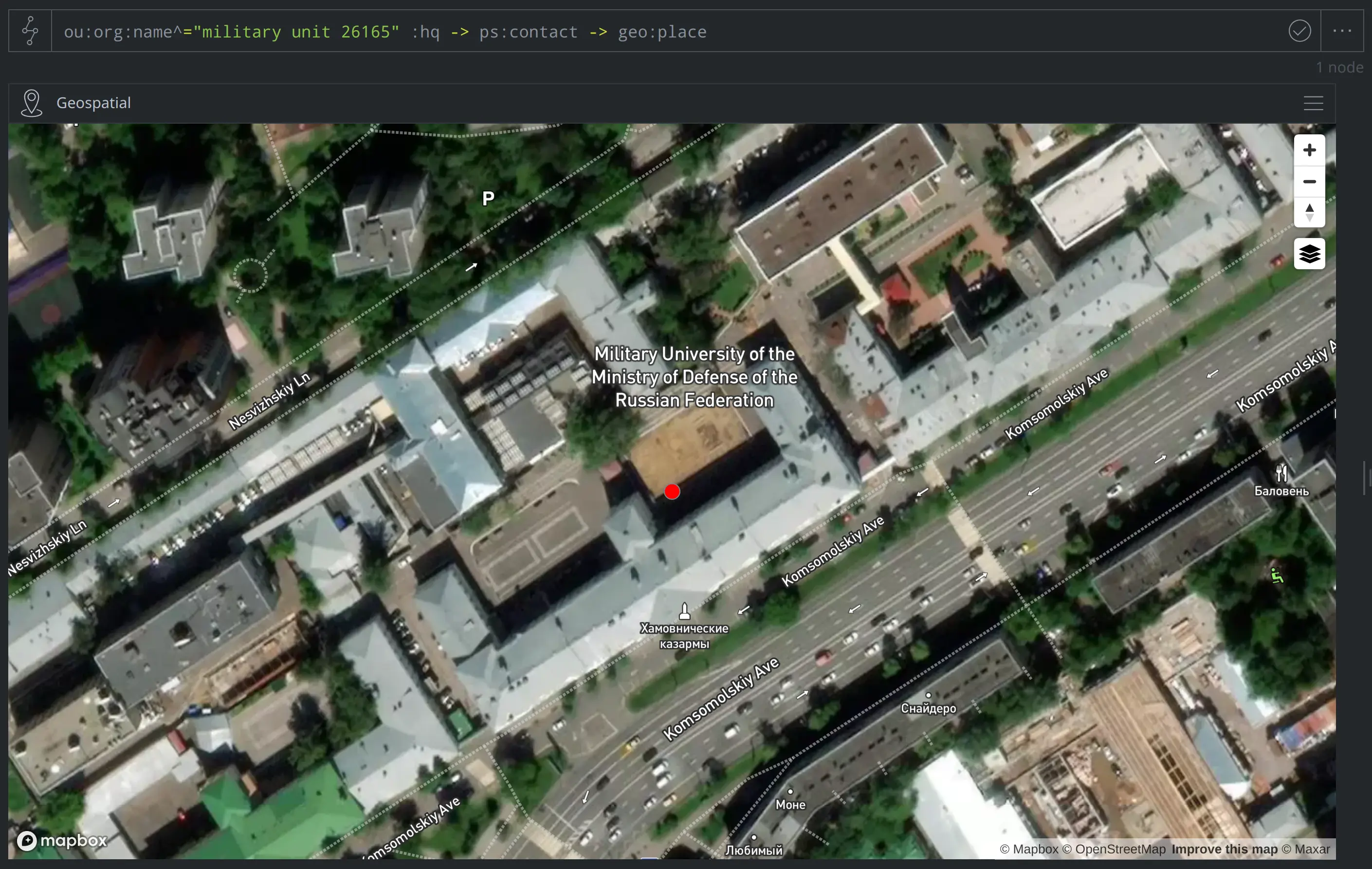
Based on our other modeled data, it looks like we have an address for Unit 26165. Where was that unit located?
ou:org:name^="military unit 26165" :hq -> ps:contact -> geo:place
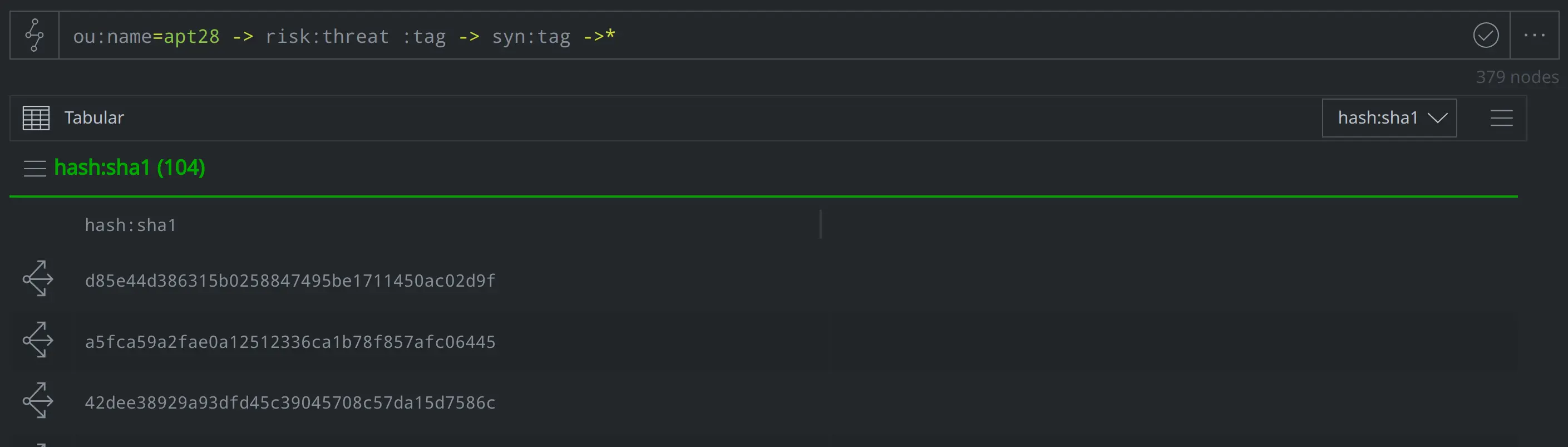
InformNapalm notes that this unit is frequently associated with the threat group APT28 - what nodes have we tagged as associated with APT28 activity?
ou:name=apt28 -> risk:threat :tag -> syn:tag -> *
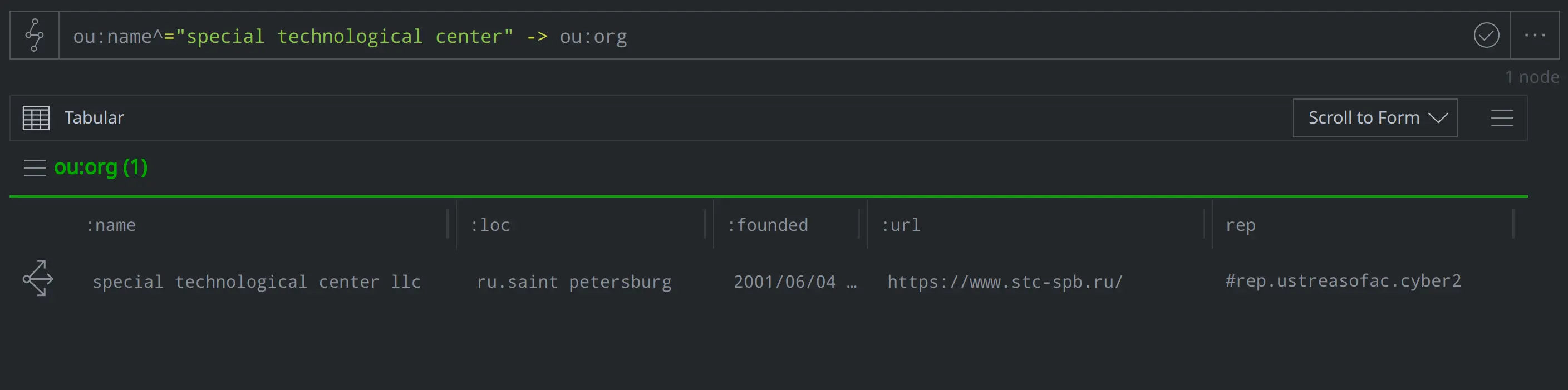
InformNapalm also noted that Morgachev currently works at a company called the Special Technological Center. What do we know about this organization?
ou:name^="special technological center" -> ou:org
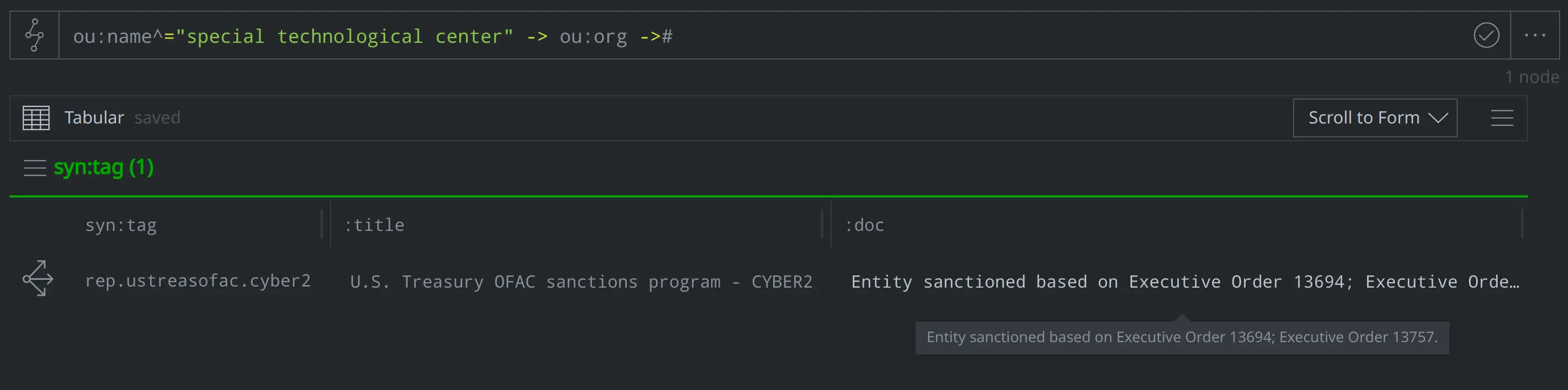
This query lifting the ou:org node representing the Special Technological Center shows that the node is tagged with #rep.ustreasofac.cyber2. Based on the :doc strings for that syn:tag node, we know that the #rep.ustreasofac.cyber2 tag is used to identify organizations that the US Treasury’s Office of Foreign Assets Control (OFAC) has sanctioned as part of a program called CYBER2:
ou:name^="special technological" -> ou:org ->#
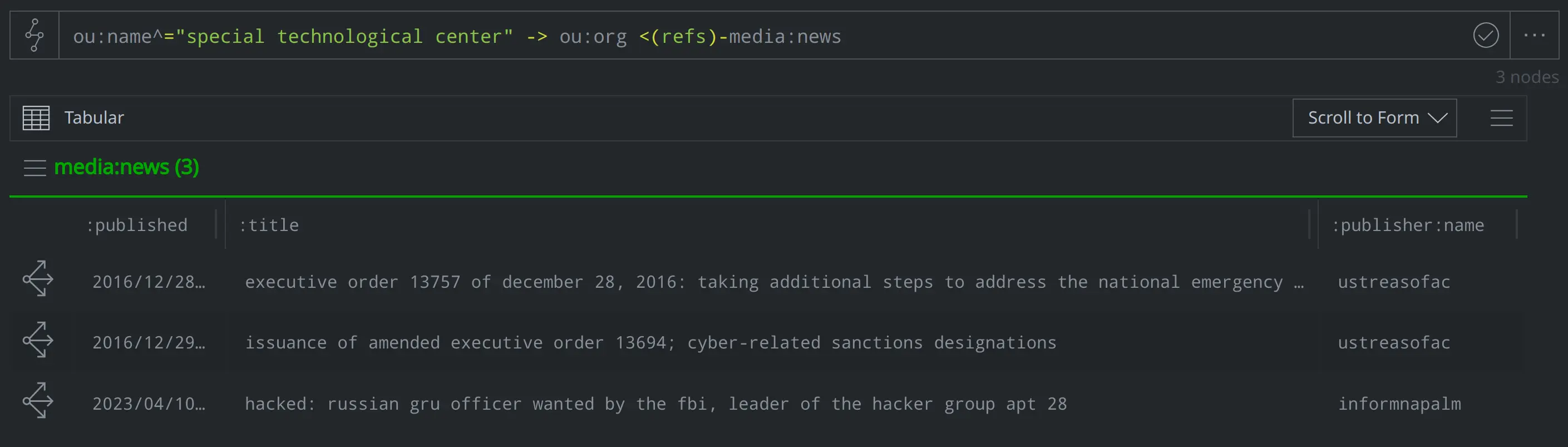
For more information, we can pivot to query for any media:news nodes referencing the Special Technological Center. Our query lifts nodes representing the Executive Orders, as well as InformNapalm’s article:
ou:name^="special technological center" -> ou:org <(refs)- media:news
From Morgachev to the GRU
In this blog we used Synapse’s data model to capture information about a specific individual, allowing us to answer questions about his educational background and work history, contact history, and official documentation, among other details. We were also able to pivot from the InformNapalm-reported data to see how Morgachev related to other data we had previously modeled within our Synapse instance, such as information about other members of GRU Unit 26165, as well as additional information about the Special Technological Center.
Synapse is designed for use across various disciplines as well as levels of analysis. In this example, we initially focused on very detailed information specific to an individual, before broadening the scope of our focus to examine how this individual fit into other information we know about related organizations, threat activity, and even US sanctions programs. Taking advantage of the depth and breadth of Synapse’s data model not only supported our analysis at those two different analytical heights, but also allowed us to pivot between the two when asking and answering questions about the data.
To learn more about Synapse, join our Slack Community, check out our videos on YouTube, and follow us on Twitter.